Information Technology Reference
In-Depth Information
by causing detaches and discharges. In relation to Example 4, when Alice informs
EBook of the payment by performing
Declare
(Alice, EBook, $12), then the
proposition $12 holds, and causes a detach of
C
(EBook, Alice, $12, BNW).
r
,
u
) is stronger than
C
(
x
,
y
,
s
,
v
) if and only if
s
entails
r
and
u
entails
v
. So, for
instance, a detached commitment
C
(
x
,
y
,
T
,
u
) is stronger than the commitment
before detachment
C
(
x
,
y
,
r
,
u
).
A commitment arises in a social or legal context. The context defines the rules of
encounter among the interacting parties, and often serves as an arbiter in disputes
and imposes penalties on parties that violate their commitments. For example, eBay
is the context of all auctions that take place through their service; if a bidder does
not honor a payment obligation for an auction that it has won, eBay may suspend
the bidder's account.
2.3 System Specification: Protocols
Traditional approaches describe a protocol in terms of the occurrence and relative
order of specific messages.
The protocol of Fig.
1
begins with EBook sending Alice an offer. Alice may
either accept or reject the offer. If she rejects it, the protocol ends; if she accepts it,
EBook sends her the topic. Next, Alice sends EBook the payment. Because an FSM
ignores the meanings of the messages, it defines compliance based on low-level
considerations, such as the order in which commitments are fulfilled. Moreover,
this type of specification is often inflexible. As illustrated in Example 2, Alice fails
to comply if she sends the payment before she receives the topic. Note that this
drawback applies to all process-oriented specification languages used for specifying
In contrast, we build on
commitment protocols
[
42]
, which describe mes-
sages along with their
business meanings
. Commitment operations are realized
in distributed systems by the corresponding messages. Commitment protocols are
therefore defined in terms of the operations introduced above:
Create, Cancel,
Release, Delegate, Assign,
and
Declare
. We introduce an abbreviation. Let
c
=
C
(
x
,
y
,
r
,
u
). Then, we
Create
(
c
) abbreviates
Create
(
x
,
y
,
r
,
u
).
Fig. 1
A purchase protocol
as a finite state machine,
taken from [
7]
. Each message
is tagged with its sender and
receiver (here and below, E is
EBook; A is Alice)




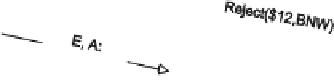

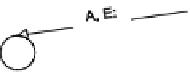
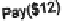


Search WWH ::

Custom Search