Information Technology Reference
In-Depth Information
Without a doubt, COR lists take some practice before the concept sinks in fully. At a high-
level view, here's how the process works:
1.
A user picks up his IP phone and is immediately associated with an incoming COR
list (which lists the “tags” he can access).
2.
The user dials, causing CME to match an outgoing dial-peer.
3.
If the outgoing dial-peer requires a COR “tag,” CME checks to see if that tag is listed
in the user's incoming COR list.
4.
If the “tag” is listed in the user's incoming COR list, CME permits the call.
5.
If the “tag” is not listed in the user's incoming COR list, CME denies the call.
Note:
I know the word “tag” is vague, but when you see the configuration of COR lists,
you will understand why I chose this word.
Similar to the famous quote in
The Matrix
, “Unfortunately, no one can be told what COR
lists are. You have to see them for yourself.” Let's walk through a practical configuration
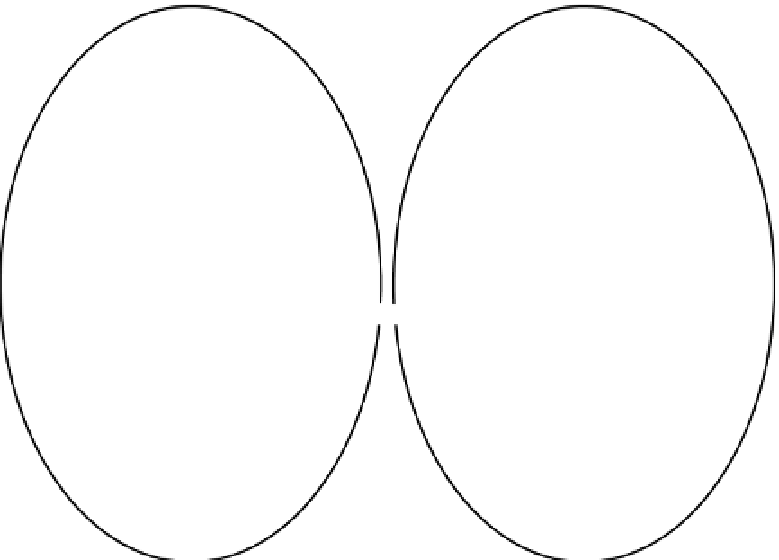
example (see Figure 6-19).
Internal Network
PSTN
Dial-Peer 10
(Emergency)
EPhone-DN1
X 2000
Dial-Peer 11
(Local PSTN)
CME Router
EPhone-DN2
X 2001
Dial-Peer 12
(Long Distance
PSTN)
EPhone-DN3
X 2001
Figure 6-19
Practical COR List Example
As shown in Figure 6-19, three phones are on the internal network:
Ephone-dn 1 (x2000)
■
Ephone-dn 2 (x2001)
■
Ephone-dn 3 (x2002)
■