Technique
Save Time By
Understanding Windows Firewall’s shortcomings
Knowing if you need a better firewall
Installing and using Zone Alarm, if you need it
You probably know that a firewall watches incoming Internet traffic and makes sure that the bad guys stay out. Windows Firewall, which ships with Windows XP Service Pack 2, does a good job of blocking bad inbound traffic (although the interface makes it harder than it should be — see Technique 50). You may be surprised to know that most firewall programs also block outgoing traffic if it looks suspicious. Windows Firewall doesn’t. I guess Microsoft ran out of money when they were building Windows Firewall. Something like that.
While it’s much more important that you keep the bad guys out, once they’ve jumped over the fence and infected your machine, it’s important to keep them from spreading their offal all across the Internet. If you were infected before you got Service Pack 2 installed, or while you have a momentary lapse in Windows Firewall’s protection for whatever reason, your PC may have been turned into a zombie — under the silent control of someone else. Millions of PCs have been subverted. If your firewall doesn’t warn you about bad outgoing traffic, you have no way of telling when your PC starts spewing millions of spam messages, or launches a Denial of Service attack on a Web page.
This technique explains why the built-in firewall in Windows XP Service Pack 2 may not be the best choice, how to set up a free-for-personal-use firewall from Zone Alarm, and how to configure Zone Alarm quickly and correctly the first time.
Understanding Firewalls
The term firewall evokes an image of an impregnable barrier between your computer and the Internet. Alas, in reality, life isn’t so simple. A computer firewall is more like a harried cop at a busy intersection than a solid wall.
For the home and small office user, firewalls fall into two broad categories:
Hardware firewalls are built into a box that connects directly to the Internet. Many DSL and cable routers, and Internet address sharing boxes (see Technique 45) include their own built-in firewalls. D-Link and LinkSys both offer good stand-alone hardware firewalls for about $50. They’re difficult to update because you have to change the firmware inside the hardware box. Typically, you can change settings on the firewall by using Internet Explorer.
Software firewalls run on the computer that’s connected to the Internet. If you have Windows XP Service Pack 2, you’re running Windows Firewall. (Unless you’ve disabled it, anyway.) Windows Firewall does a good job of playing traffic cop with incoming data. But it doesn’t even try to catch bad data that’s headed out.
Each type of firewall has its pros and cons, as you can see in Table 51-1.
Blocking bad outbound data isn’t merely an exercise in good Internet citizenship. It also adds an extra layer of protection for your own home or office network. A firewall that catches malicious outbound packets tells you if your PC has been turned into a zombie, and it’s spewing spam or Denial of Service attacks. It also tells you if one PC on your network is trying to infect other PCs, retrieve data from them surreptitiously, or use uninfected PCs to break out to the Internet. Attacks are getting more sophisticated every day. If a piece of malware gets in to a specific PC, you should be very concerned about it getting out.
Every PC should be running a software firewall. In addition, I generally recommend that people use hardware firewalls on small networks, simply because they add an independent layer of protection. To further complicate matters, you may well find that you want to run two software firewalls on the same PC. There’s nothing wrong with that, particularly if one of the firewalls is Windows Firewall.
Table 51-1: Pros and Cons of Hardware and Software Firewalls
| Type of Firewall | Pros | Cons |
| Hardware firewalls | Excellent for keeping intruders from getting into your PC or your local network. | Generally don’t do much to monitor outgoing traffic (such as data being transmitted by a Trojan that resides, unbeknownst to you, on your system). |
| Easy to use. | Hard to set up. | |
| Runs fast. | ||
| Software firewalls | Don’t weigh anything — a definite plus if you want a firewall for your portable computer when you’re on the road. | The kind that monitors outgoing traffic is more difficult to train because they monitor outgoing traffic. You have to tell the firewall which Internet traffic originating on your machine or network is legitimate so that the firewall can block the rest. |
| Easier to customize, and usually easier to set up and get working. | Because software firewalls run on your PC, they slow down your PC whenever you’re online. | |
| After they’re trained, they’re also easy to use. |
What to Look for in a Software Firewall
Software firewalls examine traffic as it leaves your network and goes to the Internet and traffic from the Internet that’s being directed to your network. A good firewall can
Allow only data into your network that’s been requested by someone on your network. If you ask for a Web page, it appears. But if somebody tries to send something that you didn’t request, the unsolicited data gets trashed. The same thing happens on a stand-alone computer: You get only data that you request from the Internet.
Ask you if it’s okay for a specific program to send out data. That gives you a chance to clear programs such as Internet Explorer and MSN Messenger that have to send data, but take a look at other programs that may not be so benign. With some firewalls, you can block all outbound traffic from all programs except a handful that you specifically allow (such as Internet Explorer).
Block attempts to get at blacklisted Web sites from your network. If you want to keep everyone on your network from getting at www. IHateBigCompanies.com, you can tell the firewall not to allow any information going out that’s bound to that site. It can block other types of outbound traffic as well.
Make your network (or your computer) invisible to the Internet. Even if somebody knows your IP address, any attempt to get information from that address is met with silence.
Windows Firewall scores high on the first point, and reasonably well on the last point, but doesn’t even begin to look at the two in the middle. And there’s the rub.
Using Windows Firewall
Windows Firewall comes along for the ride when you install Windows XP Service Pack 2. In general, Windows Firewall just works — you don’t have to do anything to it — although you may find yourself in a position where you need to poke a hole in the firewall, particularly if you use software that needs to communicate with other computers on the Internet.
I talk about poking holes in Windows Firewall in Technique 50. A full rundown on using Windows Firewall is in Windows XP All-in-One Desk Reference , 2nd Edition. And more about firewalls in general is in Firewalls, 2nd Edition, by Brian Komar, Ronald Beekelaar, and Joern Wettern ( Publishing, Inc.)
If you’ve never looked at Windows Firewall, it’s well worth a few minutes right now to take a look at the high points:
7. Choose Start Control Panel Security Center.
Windows brings up the Windows Security Center, which I discuss in Technique 49.
2. At the bottom of the Security Center, click Windows Firewall.
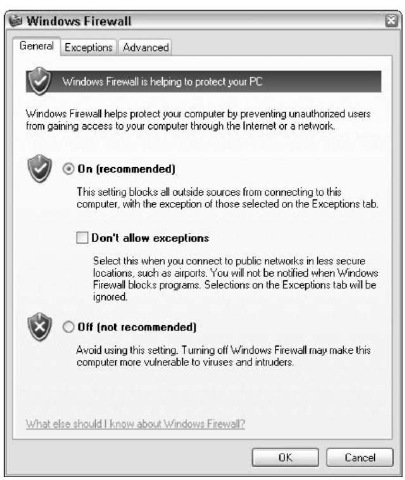
Windows Firewall’s main dialog box appears (see Figure 51-1). To understand the precise meaning of the three choices, see Table 51-2. Unless you’ve changed things, Windows Firewall is set On, and it’s protecting all your networking connections.
If any of the options in Windows Firewall are grayed out, you aren’t permitted to change the settings. Usually that happens when you’re connected to a Big Corporate Network, and somebody has decided that you can’t be trusted to control your own computer.
• Figure 51-1: Windows Firewall’s main control point.
3, Click the Exceptions tab (see Figure 51-2).
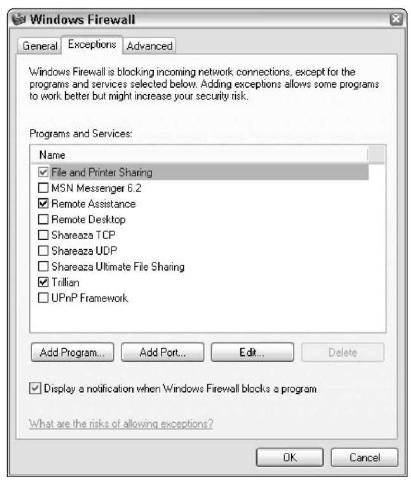
• Figure 51-2: Exceptions to the stateful firewall rules are listed here.
Windows Firewall allows data packets into your machine only if they were sent in response to a specific request originating on your machine (that’s the stateful firewall). Exceptions to that
Table 51-2: Windows Firewall Settings on the General Tab
| This setting | Means |
| On | Windows Firewall keeps track of requests for information headed out of the computer (for example, |
| (recommended) | requests to retrieve a Web page, or to download a file) and allows traffic back in only if it can be |
| matched to a specific earlier request. (That’s called stateful monitoring.) Windows Firewall allows any | |
| exceptions detailed on the Exceptions tab (see Technique 50). And it monitors all the networking con- | |
| nections that are checked at the top of the Advanced tab (see Figure 51-3). | |
| Don’t Allow | Same as On but all the entries on the Exceptions tab are ignored, and every connection gets |
| Exceptions | monitored, regardless of whether or not it’s checked on the Advanced tab. |
| Off (not | Turns off Windows Firewall. |
| recommended) |
rule — either programs, or designated ports (addresses) — are spelled out on this tab, and you can control which exceptions get enforced by checking or unchecking boxes on this tab. I talk about both kinds of exceptions in Technique 50.
4, Click the Advanced tab (see Figure 51-3).
Make sure that all the boxes in the Network Connection Settings section at the top are checked. If you uncheck a box, Windows Firewall stops monitoring that connection unless you check the Don’t Allow Exceptions box on the General tab (refer to Figure 51-1).
5, Click OK to get out of Windows Firewall.
No doubt you noticed that absolutely no provision controls outbound data. Windows Firewall doesn’t even look at it.
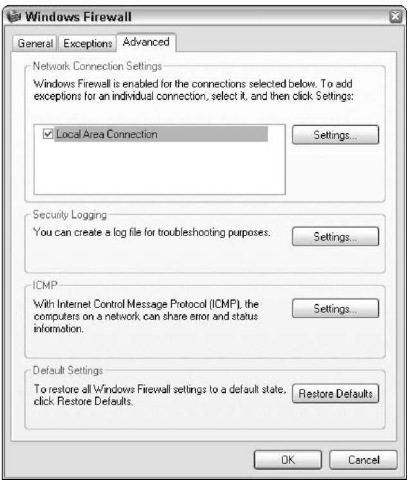
• Figure 51-3: Make sure all your networking connections are being monitored.
Installing Zone Alarm
If you aren’t overly worried about infecting other PCs on your network — indeed, if you don’t have a network — and you’re reasonably sure that your computer isn’t currently infected, you may wish to stick with Windows Firewall. That’s certainly a reasonable choice, although you should be ever mindful of the fact that your PC could be sending out all sorts of information, and you’d never even know.
If you’re ready to move up in the firewall world, I believe that Zone Alarm is your best choice. It’s effective, reasonably easy to install and use, and the price is right — free for individual use. (But there’s a charge if you use it for a company.)
Zone Alarm and Windows Firewall can work together. You may hit an occasional bumpy patch, but if you do, rest assured that the Zone Alarm folks are most interested in keeping Zone Alarm compatible with Windows Firewall. Zone Alarm even shows up in the Windows Security Center firewall status report.
To install Zone Alarm, follow these steps:
1 Start Internet Explorer and surf to
www.zonealarm.com.
Zone Labs, the company that makes Zone Alarm, sells a wide variety of products. If you want to buy Zone Alarm Pro — just $9.95 at this writing, including one year of updates — by all means do so. If you want the free version, you want the product called, simply, Zone Alarm.
2, You may have some difficulty finding the free download link, but at this writing, you can download Zone Alarm by clicking the Download & Buy and then Zone Alarm links; then click the Free Download button.
3, Follow the instructions and download it.
4, After you download the file, double-click it.
Zone Alarm then steps you through a very simple setup wizard and has you going in no time.
5, Click the Select Zone Alarm Pro radio button in
the ZA License Wizard.
That gets you kick-started, feeding Zone Alarm a list of “safe” programs (see Figure 51-4). When you finish the 15-day trial, you can switch back to Zone Alarm, no problem.

• Figure 51-4: Install Zone Alarm Pro to cut down on your setup hassles.
6, Finish the setup using Automatic Program Alert Advisor Settings.
Zone Alarm Pro reboots your machine and takes you through a quick tutorial.
After the tutorial is done, if you have a network, you are taken to a Network Configuration Wizard, which steps you through the process of protecting the PC from the network. Although there are some subtleties, Zone Alarm is primarily interested in setting up File and Printer Sharing for this computer on the network. In the end, you see Zone Alarm’s main screen (see Figure 51-5).
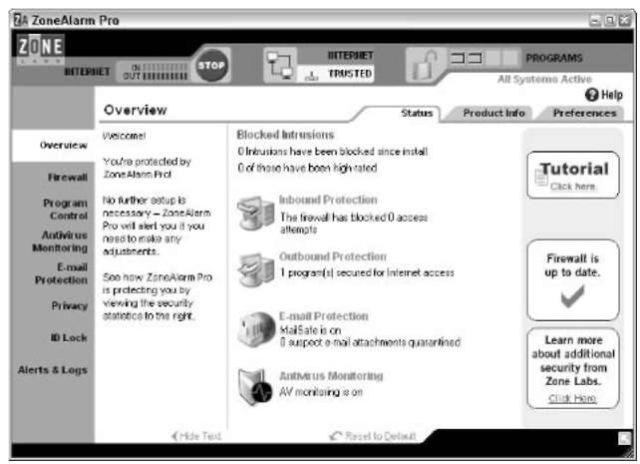
• Figure 51-5: Zone Alarm’s control screen.
Honing Zone Alarm
If you followed the instructions in the preceding section and set up Zone Alarm Pro with its automatic Alert Advisor settings, you’re ready to run. From time to time, particularly when you start to use the product, you see warnings, such as the one in Figure 51-6. It’s easy to get spooked. In the immortal words of Douglas Adams, “DON’T PANIC!”
Zone Alarm shows two different kinds of alerts:
Firewall Alerts (see Figure 51-6) happen when an attempt occurs to get into your computer. If you see an alert with a red band at the top, however, you may have a problem, and Zone Alarm has already averted it. When you click OK in a Firewall Alert, you’re merely acknowledging that Zone Alarm has done its job. You aren’t changing any settings or reducing the scope of the firewall.
Program Alerts (as shown in Figure 51-7) occur when Zone Alarm doesn’t recognize a program on your network that’s trying to connect to the Internet. Internet Explorer is pre-configured as a “good” program. Others — including Outlook — may be allowed to pass through if you chose to
run an automatic configuration in the preceding section. If you click the Allow button in a Program Alert, you’re giving your permission for that program to go out to the Internet for as long as the program keeps running.
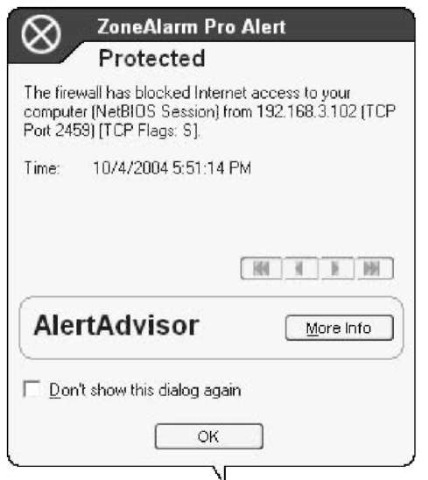
• Figure 51-6: An alert that another computer is attempting to access this computer directly.
ZoneLabs has a huge database of programs that may trigger Program Alerts. You can go straight to it by clicking the More Info button on the Alert itself.
When confronted with a Program Alert, if you want that program to contact the Internet just this time, click Yes.
To let that program always connect to the Internet, check the Remember This Setting box.
Click the Deny button if the program is a total unknown, but be alert: If some program you need to use mysteriously stops working, chances are that it’s been blocked by your new firewall (per your request).
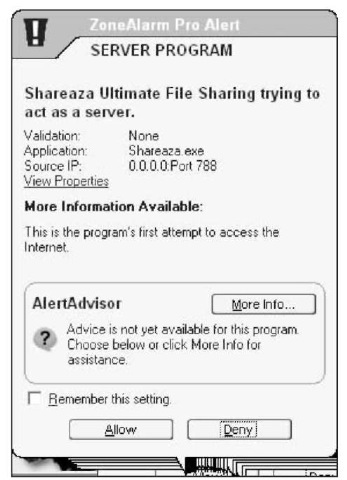
• Figure 51-7: An alert about a program inside the firewall that’s trying to get out — Shareaza, for example.
You have no automatic way to turn off Program Alerts permanently. Each one requires a Yes or No from you.
Checking the Logs
If you’re ever terminally curious about what’s been blocked — or if you can’t get something to work and you can’t figure out why — look at the log:
7. Double-click the ZA icon in the Windows notification area, down near the clock.
Zone Alarm appears. (Refer to Figure 51-5.)
2. On the left, click Alerts & Logs.
You see the Alerts & Logs dialog box.
3, Click the Log Viewer tab in the Alerts & Logs dialog box.
Zone Alarm shows you the log, as shown in Figure 51-8.
4 Click an individual alert to see the full details.
5, When you’re done, click the X in the upper-right corner of the main screen to exit Zone Alarm.
Of course, Zone Alarm keeps working. You’re just leaving the main screen.
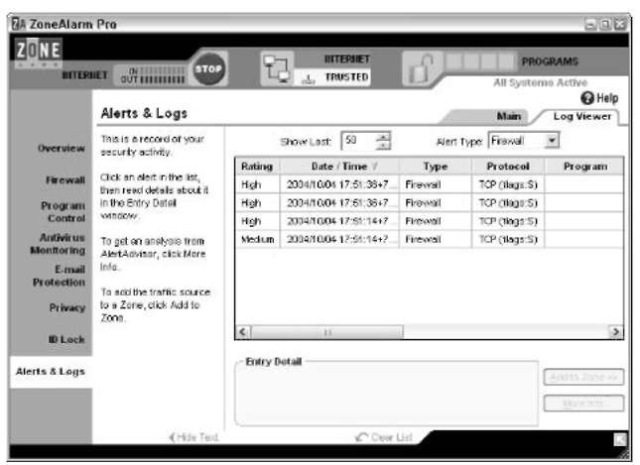
• Figure 51-8: A very handy interface for the Zone Alarm log.
