Step 3: Set up your Wireless router
This step may seem complicated. That’s because it is. It’s also required. The good news is that you should only have to do it once, or (at most) once in a blue moon.
Start with the wired side
Gather this information from the router’s documentation and your ISP:
✓ The router’s default intranet IP address. In many cases, it is 192.168.0.1 or 192.168.1.1.
✓ The router’s default administration username and password. In many cases, the username is admin or nothing. The password might be password.
✓ The username, password, and connection method that your router must use to authenticate with your ISP. It might be something like PPPoE (Point-to-Point Protocol over Ethernet).
Don’t try to guess these answers. You’d just waste a lot of time and maybe get needlessly annoyed before gathering the right information anyway.
Now you’re ready to configure the router’s connection to your ISP and the Internet. Here goes:
1. Open a Web browser on the computer and surf to the router’s intranet IP address.
The router’s built-in Web server gives you a login page.
2. Enter the default administration name and password to log in to the router’s administration interface.
After you’ve surfed to your router, you can check the status.Depending on your router’s supplier, your display will differ slightly. However, the basic information remains the same.
3. Set the date, time, and time zone if your router gives you the option.
Don’t worry if your router doesn’t let you control these settings. They may come automatically from your ISP after the router is connected to the Internet.
4. Enter the username, password, and the connection method that your router needs to authenticate itself with your ISP.
Without these, the router cannot obtain an IP address and connect to the Internet.
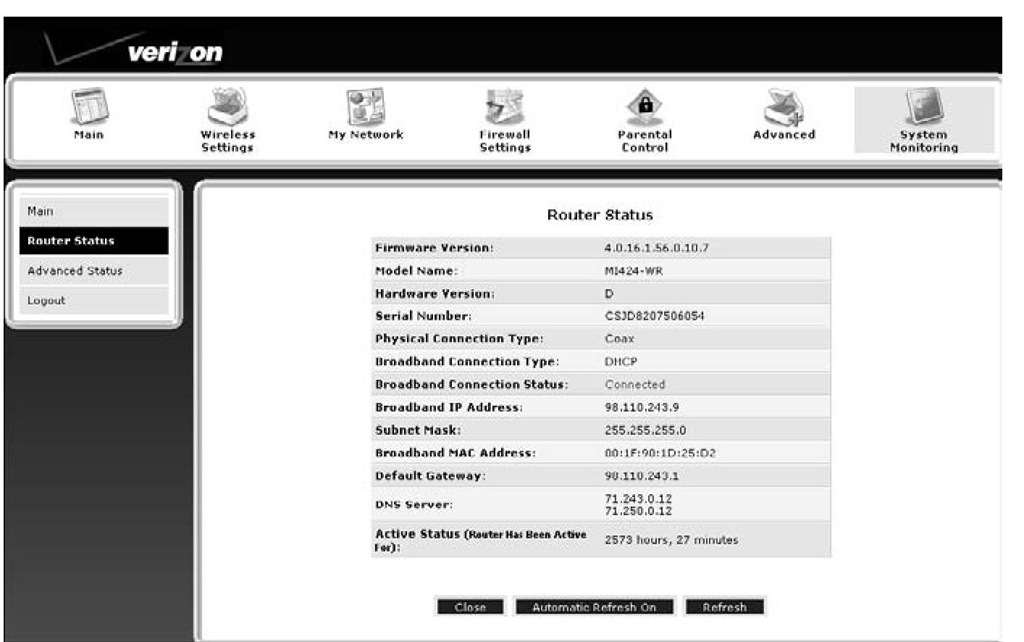
Typically, your router gets an IP address from your ISP via DHCP. That’s right; your router is a DHCP client. Figure 7-5 shows that this router gets its IP address from DHCP. Later on we show you that it’s also a DHCP server. Many ISPs use a basic security control. Their DHCP server only responds to requests from registered MAC addresses, so they have to know your router’s MAC address.
Figure 7-5:
The router’s broadband connection status is connected.
If you have arranged with your ISP for a static IP address, enter the information they gave you:
✓ The IP address itself
✓ The routing prefix (also known as a subnet mask)
✓ The default gateway
✓ The addresses of DNS servers
As soon as you have this information in place correctly, your computer — the one wired directly to the router — can access the Internet! If it can’t, then either your settings are wrong for username, password, and connection method or your ISP may be experiencing trouble.
Now for the Wireless side
Gather these default values from the router’s documentation, or if you use an ISP to install your router, get these values from the ISP:
✓ The SSID (service set identifier), also called the wireless network name. It’s usually the manufacturer’s name.
✓ Is the SSID being broadcast or not? It often is.
✓ Is the wireless network enabled or disabled? Most of the time, it’s enabled.
These days, most wireless routers come pre-configured to provide an open, public wireless network. That helps you get up and running quickly, but there is no security. Anyone can get on your wireless network! People called wardrivers drive around with their laptops booted up looking for available networks. If you broadcast your SSID and have no security on your network, these wardrivers park and connect to your network. Often these people are harmless. They just want to borrow a little of your bandwidth to access the Internet. However . . .
Beware the malicious wardriver! If one of these troublemakers uses your network to hack into a site and do damage, the origin of the hacking will trace back to your network. Uh-oh.
A little later, we tell you how to tighten security and limit who can use your wireless network.
Step 4: Connect your computers
Here’s how to connect your computers, based on whether their NICs are wired or wireless:
✓ If a computer has a wired NIC, plug one end of an RJ-45 Ethernet cable into one of the router’s LAN ports and the other end into the computer’s Ethernet NIC. Make sure the computer is set to be a DHCP client.
✓ If a computer has a wireless NIC, whether inside or attached to the computer, there is no cable to connect. Use the software that’s built into the operating system (or that came with the NIC) to specify the SSID you want to connect to; then set the computer as a DHCP client.
In either case, the computer is ready to go as soon as it gets an IP address from the DHCP server inside the router.
The wired side of your network provides a little security because strangers can’t easily plug network cables into your router without your knowledge. The wireless side, however, is a totally different story — Insecure City. So, in the following section, we look at how you can tighten things down.
Securing Your NetWork
After you’ve set up your wireless network, it’s time to enable security. You need to protect both the wired side and the wireless side.
Securing the wired side
From a computer with a wired connection to the router, open a Web browser and return to the router’s administration interface. (Use the router’s default intranet IP address, and then enter the default username and password.) Consult the router’s documentation to find the specific ways to accomplish these tasks.
Change the administrator’s name (if possible) and the password. Don’t forget either of those!
By default, you can only access the router’s administration interface from a wired connection. However, you may find it more convenient to use a wireless connection. If you choose to lift the restriction, however, remember: Doing so means that anyone on the Internet can manage your router if they know — or guess — the password!
Securing the wireless side
Always remember that if you change the router’s wireless settings, you must make matching changes on the computers! If you don’t, they can’t reconnect to the network.
Your router’s documentation will help you find the specific ways for your hardware to accomplish the following tasks:
✓ Change the SSID from the default value. Pick something that doesn’t identify you or your location.
✓ Disable broadcasting the SSID. This is not a real security protection — it’s "security by obscurity" — but it does make it a bit harder for people to connect to your wireless network.
✓ Restrict use of the wireless network to those NICs whose MAC addresses are recorded on the router. This technique is called MAC filtering.
✓ Enable wireless security. You have several 802.11i security protocols to choose from. Use the strongest combination possible, keeping in mind the phrase "lowest common denominator." That is, use the strongest combination that all the computers and wireless devices have in common. These protocols depend on some form of encryption.Basically, encryption translates your data into a secret code so snoopers can’t read it. On the receiving end, the secret code is decrypted back into readable form. So here’s the list of protocols, from strongest to weakest:
• WPA2: Wi-Fi Protected Access version 2. The latest and strongest wireless security protocol. You may need to buy the newest hardware to enable this WPA2.
• WPA: Wi-Fi Protected Access is much more intelligent than previous wireless security protocols.
• TKIP (pronounced "tee-kip") Temporal Key Integrity Protocol was a solution to replace WEP. TKIP eventually became the first version of WPA.
• WEP: Wired Equivalency Privacy, the original wireless security protocol, comes in different strengths: 64-bit, 128-bit, and 256-bit, the higher the better.
Hackers find WEP extremely easy to break, and there are programs for cracking WEP posted on the Web. Bottom line: WPA2 is best, WPA/TKIP is okay, and WEP is better than nothing.
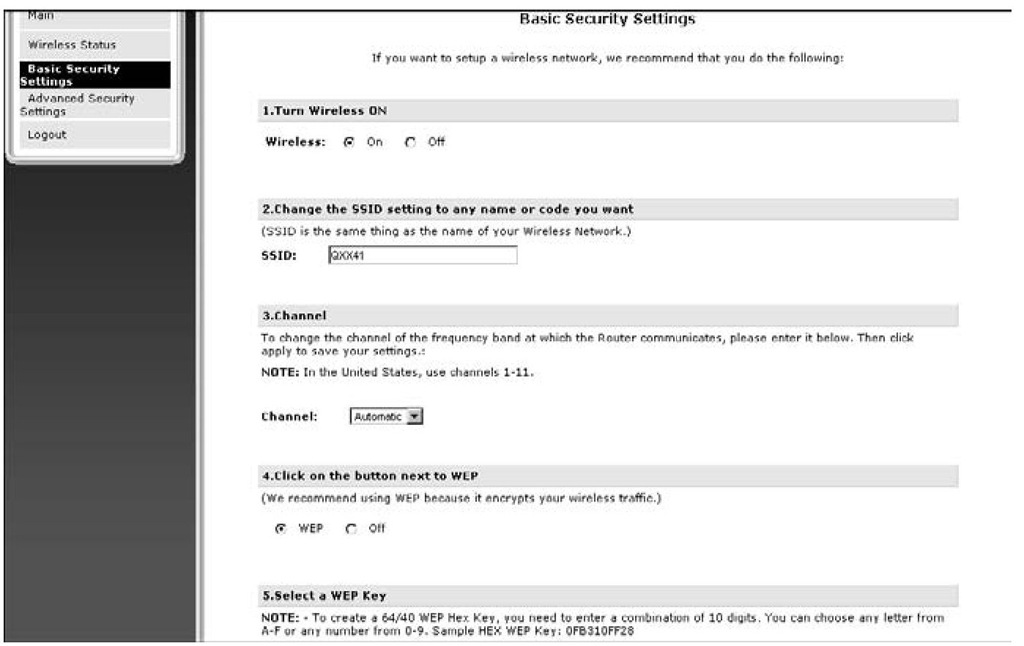
Unfortunately, you may want to use a strict level of security, such as WPA2, but if even one device on your network doesn’t support your preferred security choice, you must use the lowest common denominator. In the case of the network in Figure 7-6, we unwillingly use WEP. All of the devices on our wireless network are state of the art except for one ancient wireless printer. Because that printer only supports WEP, we’re stuck with lax security until we replace the old printer.
Figure 7-6:
It’s time to replace the old printer in order to upgrade wireless network security.
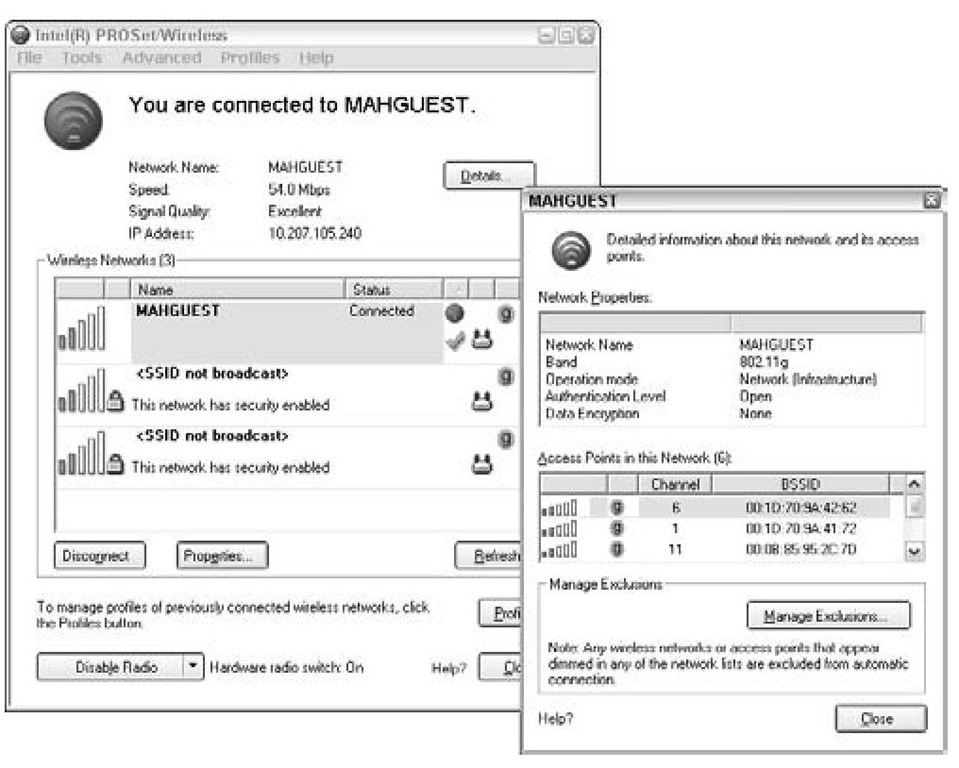
Figure 7-7 shows three wireless networks, two with security enabled, one that is wide open. The MAHGUEST network is a public network at a wireless hotspot. It has no security or encryption enabled. Public networks open to all are by their very nature not very secure.
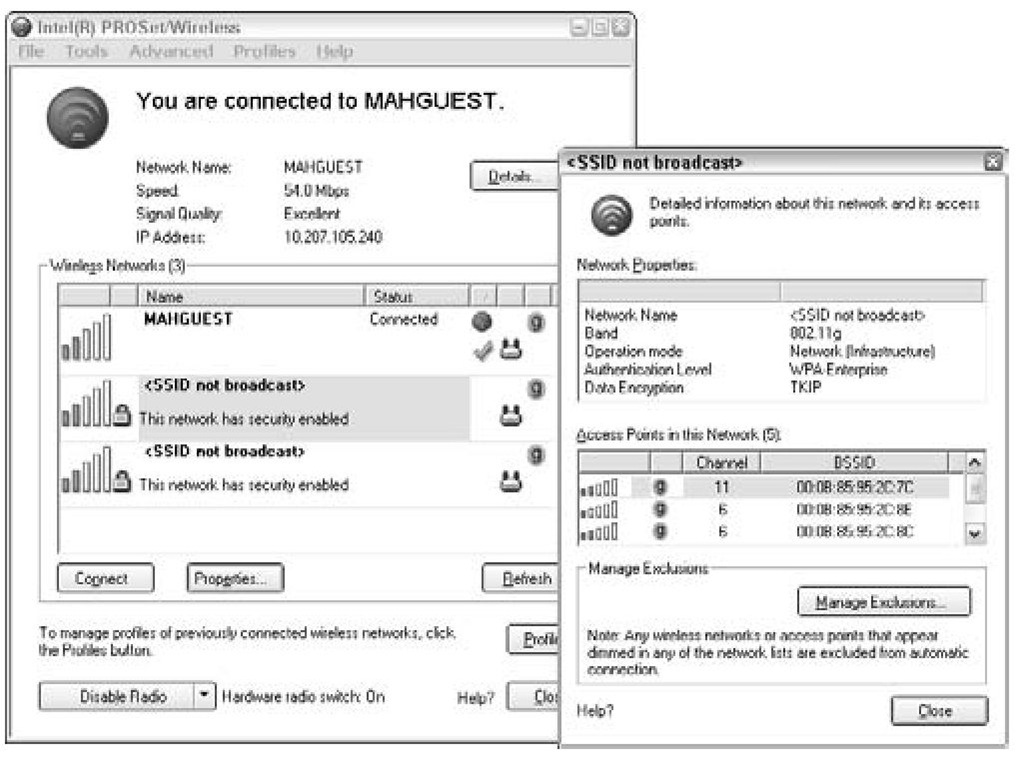
Figure 7-8 shows another network at the same location as MAHGUEST. We don’t know the name of the network because its SSID is not broadcast. This network also uses the TKIP security protocol. Interestingly, whether secure or not secure, you can see the MAC addresses of both networks.
Figure 7-7:
This public Wi-Fi network is quite convenient, but wide open.
Figure 7-8:
This network has security enabled.
Each wireless vendor provides an interface for checking and troubleshooting network connections. Figures 7-7 and 7-8 were snapped from an Intel interface. Different NICs will have different interfaces, and your screen may look different from Figure 7-7, but the data collected will be the same.
Broadband for Everyone? We Hope
WiMAX (Worldwide Interoperability for Microwave Access), pronounced "why max," is wireless over very long distances up to a couple of thousand miles. It’s based on the IEEE 802.16 standard, also called Broadband Wireless Access. Although WiMAX is still in the early stages and is not widely used, WiMAX could become important for home networkers who live in rural areas. Cable and DSL providers have ignored rural areas for a long time, and rural users have been stuck with dial-up or satellite networking. WiMAX means people out in the countryside (Hi, Dad!) will be able to have wireless broadband connections.
Depending on your needs, you can have different types of mobility:
✓ Using wireless hotspots
✓ Paying for broadband wireless service within a cellular area
✓ Going anywhere you want to connect to the Internet
We describe these different levels in the following sections.
Level 1: Using Wireless hotspots
You must go to them. Wireless hotspots let you go out of range of your home base station to use the hotspot’s Internet connection. Sometimes you must pay to connect to the hotspot. Sometimes these are free. Sometimes you have to pay. The library supplies one if you want. (It’s a fantastic library. Shameless plug for the Cary Memorial Library in Lexington, MA.)
Although you do need to buy a cup of coffee or tea or whatever is your beverage, so is it technically free? We think so, but not everyone agrees. You can also get free Wi-Fi with your fast food. McDonald’s has Wi-Fi hotspots on every continent except Antarctica. Well, DUH! There are no golden arches in Antarctica. However, Antarctica has other Wi-Fi hotspots so you can stay in touch with the rest of the world while dining with the penguins. (Hey — we said dining with the penguins, not on the penguins!)
Level 2: Paying for broadband wireless service
Some cellular providers let you subscribe on a daily/weekly/monthly basis for wireless access anywhere they provide cell phone service. Your NIC needs to be a broadband cellular modem. Most newer NICs support wired, wireless, and cellular connections in one NIC. This kind of service is similar to smart phones, such as the iPhone and the G1 by Google that let you access the Internet.
Level 3: Going anywhere you want to connect to the Internet with WiMAX
The dream of WiMAX technology is to let you connect to the Internet no matter where you are on the planet (and beyond — maybe even the Restaurant at the End of the Universe).
The reality is that WiMAX access is scattered around here and there, depending on who’s providing it. You don’t need any fancy hardware, just a standard wireless NIC. There are no distance limits. Theoretically WiMAX lets you roam as far as you want or just stay home to access the Internet. WiMAX is just getting started as an Internet connection for real life. There are plenty of test sites and demonstrations, but a good site is hard to find.
Here are some examples of WiMAX in action:
✓ In the United States, entire towns, such as Sandersville, a town in rural Georgia, are already using WiMAX. The coverage extends for about 300 square miles. Besides household and business subscribers, the police and fire departments use the network. If you live in Sandersville, you don’t need an ISP; you subscribe to the town’s WiMAX provider.
✓ Internationally, cities such as Tripoli and Benghazi in Libya and Okinawa in Japan have deployed WiMAX networks. Also, the military is using WiMAX to connect remote sites. In Japan, UQ communication offered free, introductory WiMAX to residents of Tokyo, Yokohama, and Kawasaki, followed by an inexpensive monthly fee.
✓ Do you want to be connected on your entire trip wherever you roam? Last month, Stockholm, Sweden started a pilot program to provide WiMAX service on the Stockholm-to-Norrtalje route 676 commuter bus. Everyone on board gets free Internet access. Airplanes have started pilot programs (so to speak) as well.
Think of Wi-Fi as your LAN connectivity, as it’s pictured in most of this topic. Think of a WiMAX network as an ISP’s entire WAN (Wide Area Network), but no wires — just WiMAX towers (similar to cell towers) every couple of thousand miles. Actually, a WiMAX tower that connects directly to the Internet will use a high-speed wired line. Don’t worry that the landscape will become blighted by WiMAX towers. There are already many cell towers out there that you don’t see. (There’s one hidden in the steeple of our church, in fact.) WiMAX towers don’t always have to be in front of your eyes.
WiMAX roaming is similar to cellphone roaming. When you’re traveling outside your home network’s service, you can still access its wireless services (including Internet, e-mail, voice, and video) by automatically using a network outside that of your home network provider. Of course, your home network service must have a prior agreement in place with those other services before you can use their networks.
The WiMAX Forum is a non-profit, industry-sponsored organization to watch over and certify WiMAX devices as compatible with each others. This group supports the compatibility and interoperability of broadband wireless devices, using the IEEE 802.16, Broadband Wireless Access Standards. The WiMAX Forum coined the term "WiMAX" and serves as a watchdog for how it’s used. For example, the WiMAX Forum sponsors the global roaming program to help manufacturers learn how to build compatible roaming products.