TCP/IP is like a restaurant. When the restaurant runs out of a popular dish, it substitutes another one on the menu. When IP runs out of addresses, it also substitutes other dishes.
The Internet is running out of 32-bit IPv4 addresses! You must have heard that before, maybe many times. But is that shortage still a problem? But many organizations and people haven’t moved to IPv6 yet. So, we need some other items on the menu to keep surviving with the limited number of IPv4 addresses still available while the great migration goes on. In this topic, we describe some ways to conserve IPv4 addresses without giving up any Internet connectivity.
So take heart as you peruse some appetizing subnet techniques and a tasty short menu of protocols to help satisfy the Net’s short-term appetite for addresses.
Working with Subnets and Subnet Masks
Subnets divide one network into multiple smaller networks, normally interconnected by network devices called routers.
Not every network environment requires subnets. For example, if your organization’s network has 254 or fewer hosts — and the network lives in one building (what a concept), there’s no reason to subnet it. But if your organization’s network expands into multiple locations, the network administrator needs to look at a couple of options:
✓ Ask for another entire network number for every new facility — which is greedy if your existing network still has enough unassigned host numbers to go around.
✓ Split your existing network into pieces (subnetworks — subnets for short), one piece for each location.
Class C networks are the smallest. When you get a Class C network, you get 254 addresses whether you need them or not. Imagine The Crepe Place in Paris (TCPIP), a restaurant with 3 branches. Each branch has a separate Class C network, but there are only 100 network devices in each branch restaurant. That means in each branch, 154 addresses go unused. That’s greedy (or at least wasteful)!
When subnets are necessary and the network administrator (this may mean you!) uses good common sense to subdivide the network, subnets yield some advantages over one large network:
✓ Smaller networks are easier to manage and troubleshoot, even though there are more pieces.
✓ Network traffic overall is reduced and performance may improve because most traffic is local to its location’s subnet.
✓ Network security can be applied more easily at the interconnections between the subnets.
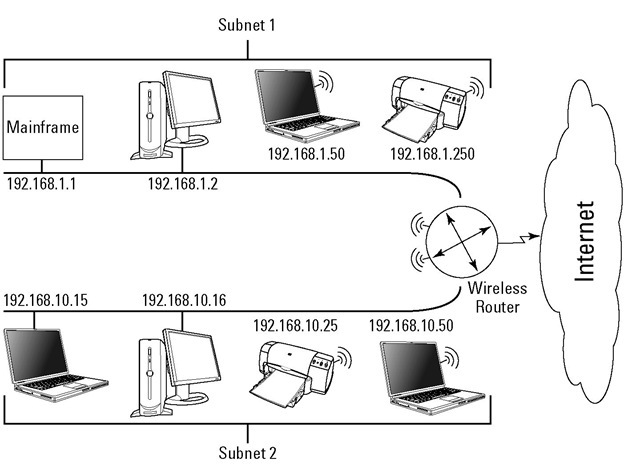
Figure 5-1 shows a main network with two subnets. Whether wired or wireless, each network and each host has an address. Look carefully at field3 in each address; can you find some subtle differences?
Part of the address for a subnet includes the address for the main network:
and borrows some bits from the host part to extend the network section. The borrowed bits enable each subnet to have its own unique network address: 192.168.1,192.168.2,and so on.
What are routers? And how big do they get?
A router is a computer that runs software that figures how a packet should be forwarded on the route to its destination. A router works at the internet layer of the TCP/IP layer cake, and connects to at least two networks. Most routers are in homes and offices and send Web, e-mail, and other Internet messages from the local area network (LAN) through your broadband connection (such as cable or DSL modem) to your ISP. Your ISP sends your routed messages out to the Internet. A combination cable modem/ router connects the home LAN to the ISP. Some of the fancier routers combine routing functions with a DHCP server and a firewall.
The routers at the biggest ISPs that connect the Internet backbones (major Internet segments) have huge capacity. Cisco Systems Inc., for example, makes most of the Internet routers, including one that’s so powerful, it’s listed in the Guinness World Records. This enormously powerful router can move up to 92 Tbps (terabits, that is, trillion bits) of data per second. Just one of these routers on the Internet will allow 1 billion people to play an online game, and use real-time voice-and-chat — all at the same time. (For that matter, it would let everyone who’s ever read any edition of this topic watch a video simultaneously.) Whew! Luckily, most of us don’t really need a router that costs half a billion U.S. dollars.
Figure 5-1:
Each subnetwork has its own address.
Because the subnet addresses come from the main network’s address, you don’t have to ask a registrar to assign them. These addresses already belong to your organization; you’ve just decided to use them differently.
Defining subnet masks
When the network administrator borrows bits from the main network address’s host section, TCP/IP needs to know which bits of the host section are borrowed to be used as the network address. The administrator uses a subnet mask to borrow those host bits. A subnet mask is 32 bits that overlay an IP address.
An IPv6 subnet mask is 128 bits, but IPv6 subnet masks are only rarely needed.
The mask sets all the bits for the network address to 1, and all the bits for the host address to 0. The mask tells the router, "Look only at the bits that lie under the 1s. Forget about any bits that lie under the 0s." Because the router can skip the masked-out bits (that is, the zeroed-out bits), it can send packets on their way faster than if it had to look at the entire address.
Before defining a subnet mask, the network administrator needs to figure out how many subnets to create and how many hosts will be in each subnet. This determines how many bits should be set to 1.
The more bits used for the subnet mask, the fewer hosts can be on each subnet created.
Why a network has a mask when it has no subnets
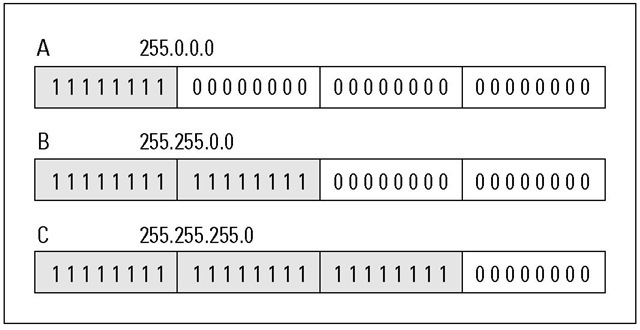
Your network always has a subnet mask even if it doesn’t use subnets. Most TCP/IP implementations supply a default subnet mask, which says, "Hi. I’m a network that’s not subnetted." Figure 5-2 shows the default subnet mask for each class of network. Most TCP/IP vendors automatically set the default subnet mask for you.
Regardless of your operating system, you can see the mask when you look at your network properties.
The subnet mask must be the same for each computer on that part of the network; otherwise the computers don’t understand that they’re on the same subnet.
Figure 5-2:
Each class has a default subnet mask.
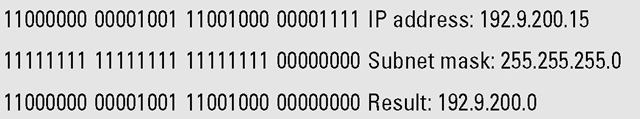
The subnet mask is applied to the IP address in every message in order to separate the network number and the host number. For example, when your computer examines the address 192.9.200.15 and applies the default subnet mask of 255.255.255.0, it sees the network number 192.9.200 and the host number 15.
Okay, how do you know this works? Hold on to your techie hats. It’s done by converting nice decimal numbers, such as 255, to not-so-nice binary numbers, such as 11111111. Then, after all the numbers are converted to binary, they get ANDed. AND is a binary mathematical operation. If you aren’t fed up AND bored by now, read the upcoming sidebar "Boolean arithmetic: AND." Just remember: Although this stuff may seem incomprehensible to you, your computer lives, breathes, and eats binary — and thinks this is Really Fun!
(The authors of this topic cannot be held responsible for any medical or mental complications that result from reading the Boolean arithmetic sidebar.)
Subnetting 101
Say, for example, that you’re going to split one Class C network with 256 addresses into two equal subnets of 128 addresses each. First order of business: Change the Class C default subnet mask of 255.255.255.0 — along some very specific lines . . .
For this example, you use network number 192.9.202, which means the 256 addresses are numbered 192.9.202.0 through 192.9.202.255. To split the network into two parts — giving one part addresses 0 to 127 and giving the other addresses 128 to 255 — you need the custom subnet mask 255.255.255.128. The 0 becomes 128 because you borrow the high-order bit from field4. (In binary, 128 is 10000000.
Boolean arithmetic: AND
In the AND operation, regardless of the value in the data bit, a mask bit of 0 yields a result of 0. And a mask bit of 1 preserves the value in the data bit, also regardless of the value in the data bit. Another way to say this is that the result bit is a 1 if and only if both the data bit and the mask bit contain 1. Otherwise the result bit is 0. This table demonstrates:
Here’s an overview of how a subnet mask is used to obtain the network number part of an IP address. In your computer, the fields of the dotted decimal IP address 192.9.200.15 are already in binary as
The fields of the dotted decimal subnet mask 255.255.255.0 are also already in binary:
The AND operation yields the network number 192.9.200, as shown here:
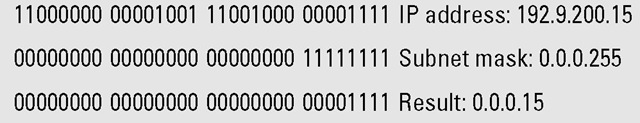
To get the host number, your computer inverts the bits of the subnet mask — each 1 becomes a 0 and each 0 becomes a 1 — and does another AND. Easy as pi, right?
In the 192.9.202 network, there are 128 addresses that happen to have the high-order bit of field4 set to 0 and another 128 addresses that happen to have the high-order bit set to 1. If you thought the custom subnet mask would be 255.255.255.1, you were close, but that mask borrows the low-order bit of field4. It puts all the even-numbered addresses (0, 2, 4, 6, and so on up to 254) in one subnet and all the odd-numbered addresses (1, 3, 5, 7, and so on up to 255) in the other.
Before subnetting this example network, it was easy to say that all the hosts were in the 192.9.202 network. The good news: After subnetting, they still are.
Probably the most common example of subnetting is splitting a Class B network into 256 Class C networks. To accomplish this, every host sets its subnet mask to 255.255.255.0.
If you’re a network administrator and you hate this math, Google "free subnet calculators" for some handy tools to ease the pain.
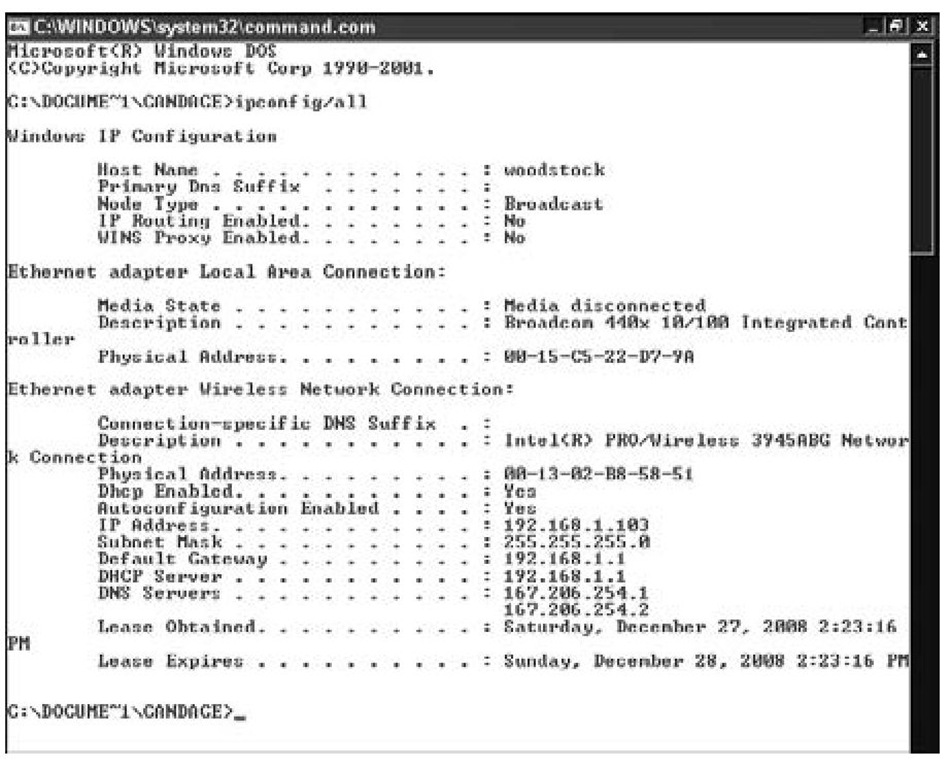
If you don’t know your subnet mask and you want to know it, the ipconfig or ifconfig command is an easy way to find out. (Use ipconfig if you’re running some form of Windows. Use ifconfig if you’re running some form of Linux or Unix.) If you add the following command option, as shown in Figure 5-3, you can see your subnet mask:
Figure 5-3:
Use the /all option on the ipconfig command to see the subnet mask.
Letting the DHCP Protocol Do the Work for You
If you could use some help with the complexities of subnetting, DHCP (Dynamic Host Configuration Protocol) provides some. It’s the TCP/IP protocol that automatically assigns and keeps track of IP addresses and subnet masks while the network administrator takes a stroll on the beach. DHCP has three major benefits:
✓ DHCP gives out IP addresses only when they’re needed
✓ DHCP automatically recycles IP addresses
✓ DHCP reduces network administrators’ workloads
So here’s a look at how gnarly subnetting can be, and how DHCP can help you through the maze.
One administrator’s nightmare is another’s fantasy
Imagine you’re the person in charge of the White Pages of the telephone topic. What a hard job it must be! You have to be sure that every customer’s name and number are in the topic correctly and in alphabetical order. When people move into your area and get phone service, you have to assign every one of them a number and list it in the directory. If people discontinue service, you have to remove their names and numbers. If you live where people move frequently, you spend all your time keeping that directory up to date.
Now fantasize that the telephone company gets a new system that’s magical — and whenever someone needs to be assigned a telephone number, you don’t have to do anything. The telephone system magically assigns a number automatically. If someone no longer needs a number, the telephone system automatically removes it and later recycles the number to someone else. And forget about keeping the telephone topic up to date. The telephone system magically does that, too. In fact, there’s no permanent telephone topic. If someone wants to call Emily, she picks up the telephone and says, "Please connect me to Emily’s telephone, wherever that is." This system would make your life as a telephone administrator so easy that you could work at the beach with a novel in one hand and a cold drink in the other.
Fantasy? Yes, for telephone administrators — but not necessarily for network administrators. People communicate on a network — big or small, Internet or intranet — via computer names and IP addresses. The network administrator keeps these names and addresses up to date in a hosts file or a DNS database. Maintaining this information is tedious and time-consuming in a volatile network environment, just as it is in a real-life telephone company.
In IPv6, DHCP changes its name to DHCPv6.