Understanding How BGP Routers Work
When a BGP router first comes up on the Internet — whether as a new router or one that was off but has been turned back on — it connects with other BGP routers. It immediately copies the routing tables of each neighbor router. Then, after initially getting the routing tables, the BGP router only sends and receives update messages to and from the other BGP routers.
The list of update messages changes depending on the preferred route for a host’s IP address. The router also updates its own routing tables when this new path is more efficient. Updating the routing tables can be very intensive and may slow the routers down, and, therefore, slow down part of the Internet. There is an addressing technique called CIDR (Classless Inter-Domain Routing), described in the next section, that reduces the size of the routing tables to help the routers perform faster.
Juicing Up Routing with CIDR
When you use classful IP addressing,you need a separate entry in a router’s routing table for each network. You wind up with a bloated routing table with heaps of entries because of the large number of networks that exist. Depending on the size of the router, large routing tables lead to degraded performance and the eventual crash of the router. If you use CIDR (instead of the traditional Class A, B, and C addressing scheme), you can use one routing-table entry to represent a whole group of networks. This keeps your router nice and lean and fit. This technique is called route aggregation. Don’t worry. You haven’t lost the routes to individual networks. Those routes simply exist in another router down the path.
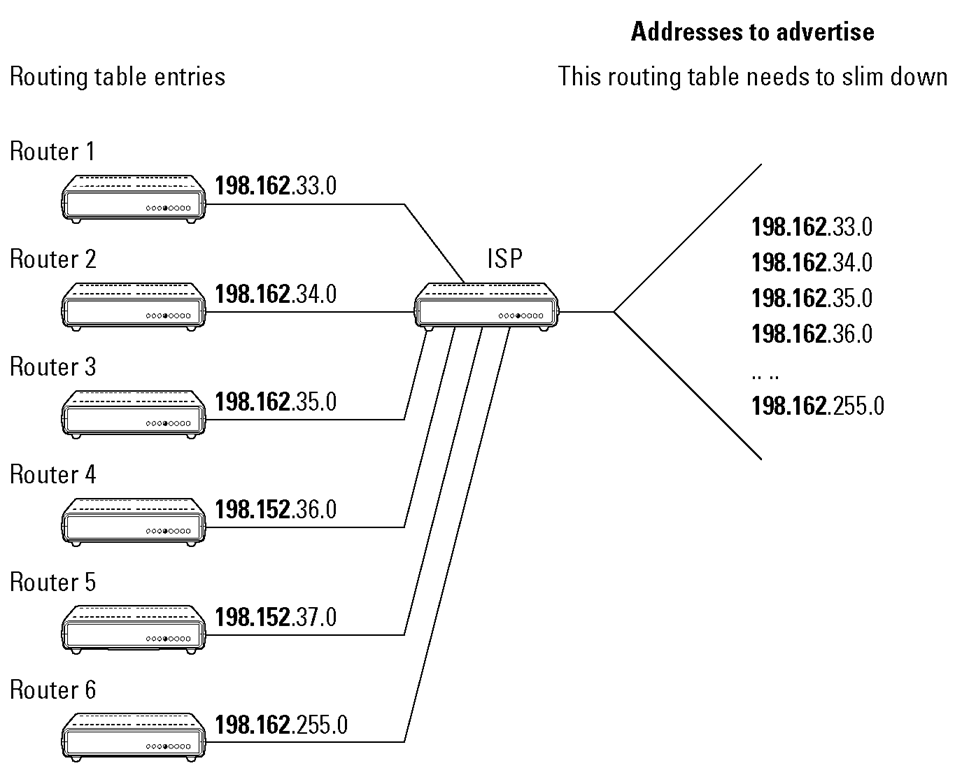
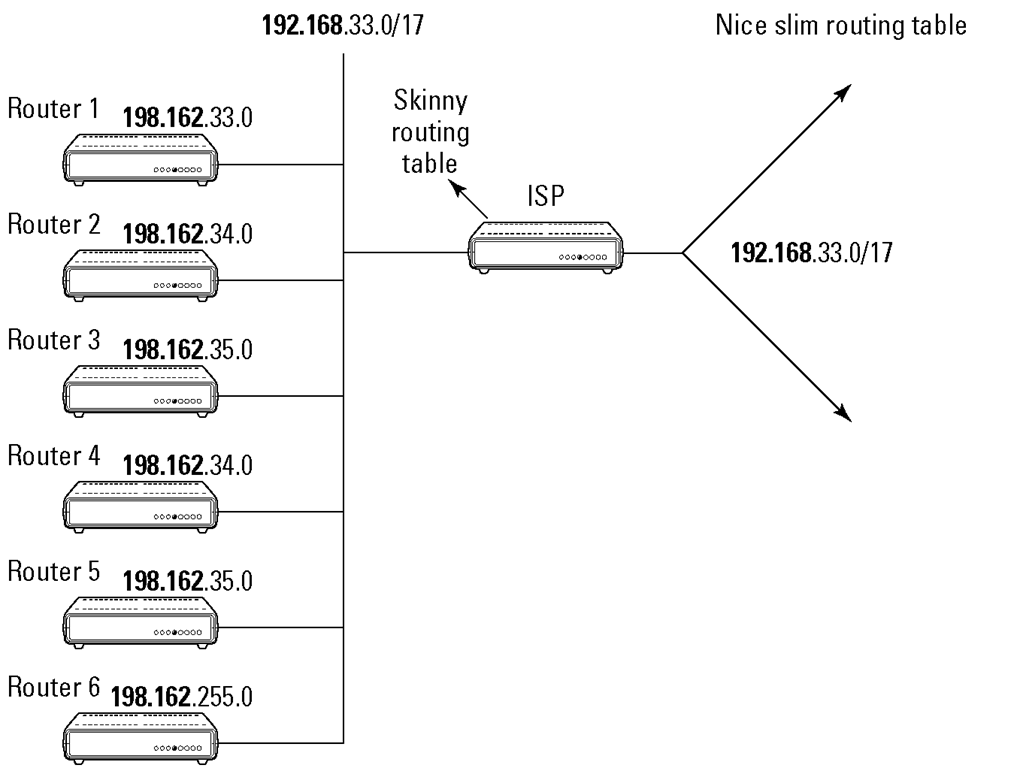
This scheme works because each entry in the router has a network prefix associated with it. The network prefix identifies the correct network for a given IP address. Figures 8-13 and 8-14 show a network before and after "CIDRizing."
Another benefit of CIDR is that it reduces the demand for classful Class C networks. Okay, we know — how can something that’s classless work on something that’s classful? Please have patience and read on.
Figure 8-13:
A chubby routing table before CIDRizing.
Figure 8-14:
A slimmed-down routing table after CIDRizing.
C Is for Classless
With the enormous growth of the Internet, everyone needs to accept that IP addresses are an endangered resource that must be managed for the good of the many. CIDR replaces the system of A, B, and C classes with a way to allocate IP addresses that allows the Internet to grow without getting ungainly and sluggish.
With CIDR, the remaining — enormous — Class A networks are split into various sizes, including the traditional Class B size. The Internet backbone’s routers understand CIDR and distribute packets to the right destinations. The following sections describe how CIDR works to conserve IP addresses and, most importantly, how it makes routing tables more efficient.
CIDR pressing the routing tables
CIDR is an addressing and routing scheme that enables routing decisions to be made more efficiently by reducing the size of routing tables. Reducing the size of anything in the Internet is a good thing. (Too bad TCP/IP doesn’t have a protocol for reducing the size of our waists — excuse the digression).
If you’re an Internet user who doesn’t need to configure IP addresses on your computer, then you now know all you need to know about CIDR to discuss it intelligently. Stop here if you don’t want to read too many stressful techie details. But if you’re a network administrator, read on.
The problem
In late 1990, there were 2,190 routes to be managed by routing tables. In early 1999, that number exceeded 40,000 routes. It takes almost 64 MB of computer memory and a powerful CPU to store 60,000 routes. If you use CIDR, you can save lots of router memory and CPU power, too.
The solution
CIDR offers a solution to the growing demand for IP addresses without making the Internet address space too hefty to manage. One way CIDR does this is to replace a Class B address with a group of contiguous Class C addresses that can be allocated differently. This technique is called address space aggregation. Aggregation has two benefits:
✓ Fewer Class B addresses are wasted.
✓ The routing table size is nice and slim and manageable.
CIDR specifies that every IP address include a network prefix that identifies either one gateway or an aggregation of network gateways. The length of the prefix is also part of the IP address.
A CIDR network address looks like this:
13 0.103.40.03 is the IP address, and /18 declares that the first 18 bits are the network part of the address. The last 14 bits (because 32 bits minus 18 bits equals 14 bits) represent the host address. A /18 address-space aggregation holds 16,384 hosts — that’s equivalent to 64 Class C networks and is one-fourth of a Class B network. Table 8-1 lists more details.
Taking CIDR apart
C is for classless— which means "Let’s revolt against the 4-class structure of IP addresses, especially Class B networks (65,533 hosts), which often waste lots of IP addresses."
I is for inter. Inter-domain means that CIDR is used between domains. The routers on the Internet’s backbone network that use BGP also use CIDR for routing between each other. The Internet’s regulating authorities now expect every ISP to use CIDR.
D is for domain. RFC 1518, "An Architecture for IP Address Allocation with CIDR," defines a domain as the group of "resources under control of a single administration." Internet service providers (ISPs) are domains of domains; that is, an ISP lets other domains hook into its network. Subscribers are the domains that connect to ISPs. A domain can be both an ISP and a subscriber simultaneously.
R is for routing. This paragraph is a brief review. A router is a computer that runs software that connects two or more networks. Routers determine the path a packet should follow on the network as it moves toward its final destination. A router stores a table of the available routes for packet travel and figures out the most efficient route that a packet should follow.
Table 8-1 CIDR Address Space Aggregations
|
Bits in Network Part |
Number of Hosts |
Number of Class C Networks |
|
/12 |
1,048,576 |
4,096 |
|
/13 |
524,288 |
2,048 |
|
/14 |
262,144 |
1,024 |
|
/15 |
131,072 |
512 |
|
/16 |
65,536 |
256 = 1 Class B network |
|
/17 |
32,768 |
128 |
|
/18 |
16,384 |
64 |
|
/19 |
8,192 |
32 |
|
/20 |
4,096 |
16 |
|
/21 |
2,048 |
8 |
|
/22 |
1,024 |
4 |
|
/23 |
512 |
2 |
|
/24 |
256 |
1 |
|
/25 |
128 |
1/2 |
|
/26 |
64 |
1/4 |
|
/27 |
32 |
1/8 |
|
/28 |
16 |
1/16 |
CIDR also works with the OSPF routing protocol.
You say "subnet,"aggregating.net says "aggregate"
Okay, just trust us — it’s aggregating not aggravating. Consider the example of a fictional Internet service provider (ISP) named "agregating.net." Agregating. net is allowed to give out addresses 162.9.*.* (where * represents 0 to 255). When you sign up with aggregating.net, you get a piece — some subnet — of its address space (numeric IP address range). From aggregating.net’s perspective, it is aggregating your address space into 162.9.*.*. For example, a mythical company called "example.com" gets 162.9.200.0/24, and your company gets 162.9.201.0/24. Remember: Table 8-1 says that the "/24" part of the address means you can have 256 hosts. With CIDR, it’s easier for agregating. net to give all of its customers the number of IP addresses they need without wasting too much.
Assume that aggregating.net has 100 customers. Before using CIDR, aggregating.net’s routing table had 100 entries — one for each customer’s address. But now it has just one entry on the Internet that benefits all 100 clients. That routing table entry says, "Send me all packets addressed to 162.9.*.*." That makes for a much smaller and, therefore, more efficient routing table. This is what CIDR does. Now, apply this sample routing efficiency across the entire Internet address space. The efficiency savings are impressive! We wanted to say staggering, but maybe we’re getting carried away — or maybe we drank too much hard CIDR.
The many free IP calculators that you can find on the Web also do CIDR calculations.
Securing Your Router
There’s not much you can do about Internet router security unless you’re a network administrator at an ISP, but threats and attacks do exist at the highest levels. Most routers are multi-purpose and include a firewall as a first line of defense.
The United States government is sponsoring the BGPSEC program to secure BGP operations that are currently vulnerable to assault. BGPSEC is a multimillion-dollar, multi-year project. Why spend so much time and effort on one protocol? Remember, BGP is the core routing protocol of the whole Internet.
If you want to bring the Internet to its knees, bring down BGP. Unfortunately, the firewall doesn’t prevent attacks on Internet routers and BGP — in particular, these:
✓ Denial of Service (DoS)
✓ Router (IP) hijacking
✓ BGP eavesdropping
We describe each of these types of attacks in the sections that follow and end with a couple of proposals from private industry to shore up BGP router security.
Coring the apple with Denial of Service (DoS) Attacks
Along with the Domain Name System (DNS), BGP routers form the core of the Internet. In the year 2000, there was a rash of DoS assaults on popular Web sites. The goal of DoS is to prevent Web users from getting any information from their favorite sites. The attackers flooded the routers with far too many requests to be managed.
Routing protocols have rules that won’t allow millions of requests from the same address in a short time space. If a router receives too many requests, it throws away the extra requests. However, if you really want to outsmart the routers, you can do what the bad guys did: They inserted programs on various computers that sent thousands of requests per minute to a Web site. These programs spoofed the sender’s IP by putting a false IP address on each packet. IP spoofing let the bad guys get around the routers’ security rules. As the routers received this flood of legitimate-looking packets, they couldn’t handle the deluge. The routers discarded millions of packets and sent messages to other routers that the connection was full. Soon enough, honest traffic couldn’t get through the routes to the Web servers they wanted.
Hijacking routers
A router hijacking (also called an IP hijacking) can make it seem that a Web site has been wiped off the face of the earth. For example, in 2008, Pakistan Telecom hijacked YouTube traffic from around the world. Although YouTube was up and running, all the content it sent out was basically going into a black hole. No matter where in the world you were, you could not get to YouTube because it was clogged with false "advertisements" about the YouTube network sent to the Internet routers. Oddly enough, this hijack was not maliciously intended. It was a mistake — but a serious mistake.
When a router decides on the best path to reach an IP address, it checks a BGP table for the best route. That BGP table consists of "advertisements" issued by large networks, such as ISPs. The advertisements declare a list of IP prefixes (a mass of IP addresses) to which they’ll deliver Internet traffic.
The routing table searches for the destination IP address among those prefixes. To intercept data, someone with a BGP router advertises a smaller range of IP addresses than the mass other networks advertise. Because the BGP protocol likes smaller masses, it will go with the hijacker. The hijacker’s advertisement would take only minutes before data headed to legitimate addresses would be hijacked to the wrongdoer’s network.
Eavesdropping on BGP
BGP Eavesdropping tricks BGP routers into re-directing Internet traffic from a legitimate address to the eavesdropper’s network. Anyone with a BGP router (ISPs, large corporations) can intercept data headed to a group of IP addresses or to one address. Eavesdropping attacks only steal data headed to network destinations. They can’t affect outbound data.
It’s so sad
You might wonder, "How can someone shut down an entire Web site or spy on others’ data? It’s the Internet’s history of trust again. BGP’s architecture assumes routers are trustworthy. When a router says a route is the best path, BGP assumes the router is telling the truth. Attacks like those detailed here sadly prove that BGP’s assumption of trust is naive and gullible when compared with Net realities.
S-BGP (Secure BGP): Proposals to make BGP routing secure
In addition to the U.S. government’s BGPSEC research program described earlier, private corporations are looking for solutions to the BGP security problems. BBN Technologies, the company that launched the ARPANET (later to become the Internet) in 1969, has proposed S-BGP as an architectural solution to improve BGP security by adding additional data and checks to the existing BGP protocols. BGP relies on the IPSec group of protocols to add needed security features to BGP routing. BBN has implemented a test system for S-BGP.
Cisco Systems (the largest router vendor) has proposed Secure Origin BGP (SoBGP). So far, no BGP security research has been put into production because the proposed security features require too many changes to routers.