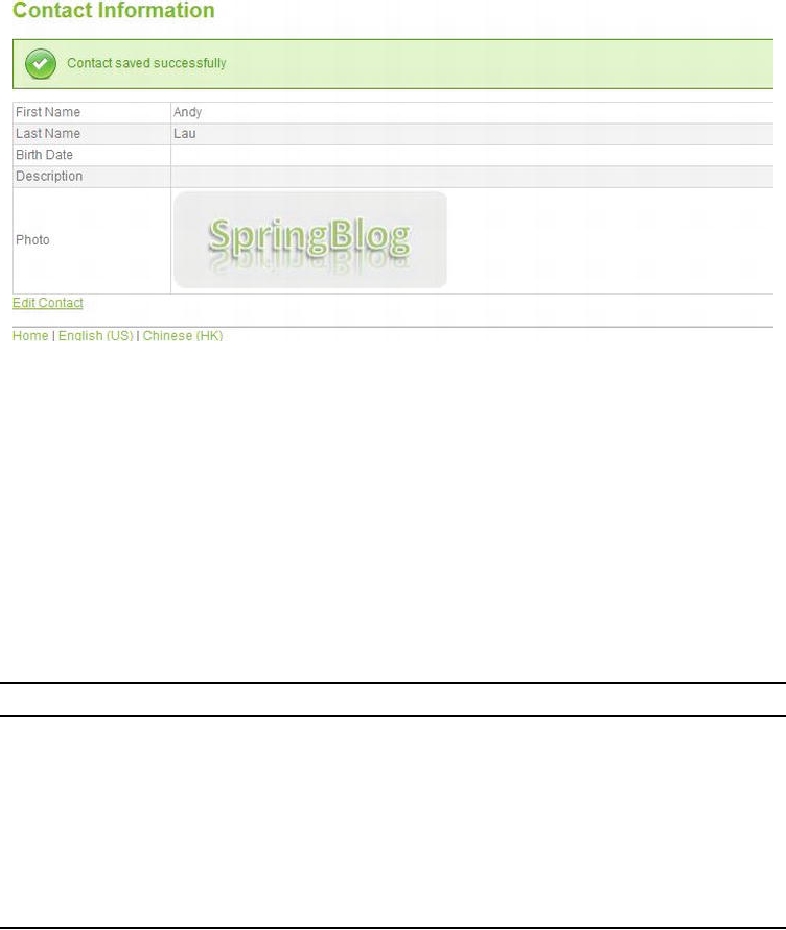
Figure 17-22. Show contact view with photo
We also need to modify the edit function for changing the photo, but we will skip it here. You can
refer to the sample source code.
Securing a Web Application with Spring Security
Suppose now we want to secure our contact application. Only those users who logged into the
application with a valid user ID can add a new contact or update existing contacts. Other users, known
as anonymous users, can only view contact information.
Spring Security is the best choice for securing Spring-based applications. Although mostly used in
the presentation layer, Spring Security can help secure all layers within the application, including the
service layer. In the following sections, we will demonstrate how to use Spring Security to secure the
contact application.
Table 17-8 lists the dependencies required for Spring Security.
Table 17-8. Maven Dependencies for Spring Security
Group ID
Artifact ID
Version
Description
org.springframework.security
spring-security-
3.1.0.RELEASE
Spring Security core
core
module
org.springframework.security
spring-security-
3.1.0.RELEASE
Spring Security web module
web
org.springframework.security
spring-security-
3.1.0.RELEASE
Spring Security
config
configuration module
org.springframework.security
spring-security-
3.1.0.RELEASE
Spring Security JSP tag
taglibs
library
Search WWH :