Many of the security measures devised since the early 1990s have been centered on protecting private networks from the public Internet. Today the larger corporate networks use a firewall when connecting their private networks to the Internet. They then can run VoIP on their private network without threat from the Internet.
In the same way, smaller companies with fewer than four or five locations can elect to go with a private network in a similar way. But depending on their business needs and total number of employees, it may make more sense to use a virtual private network (VPN). VPNs present interesting firewall security challenges. (More on VPNs in a virtual minute.)
Consumer VoIP and firewalls
Consumers running VoIP over their broadband service have little to worry about with Internet security. No doubt someone will try to sell you a firewall security package to protect your VoIP service from a virus attack, but it would be foolish to spend the money.
Broadband providers and VoIP carriers include with their services a first level of firewall security. Your VoIP calls have firewall security first from your VoIP carrier and then again when
your voice packets travel through your broadband provider’s network.
Does this VoIP protection keep you safe if you download unsafe data files to your computer? No! You still should have a firewall security package running on your computer that protects you against nasty, corrupt, data Internet files. You don’t need such protection for your VoIP calls, however.
Most of the security measures utilized today read and inspect the packets that traverse the network. Security therefore comes down to deciding where in the network the packets will be examined and what type of systems you will use to monitor the packets. For most companies, the examination location is at the connection point to the Internet, as described earlier in this topic.
Companies that implement a VPN require each location on that VPN to use a firewall to access the Internet. If the company is to run VoIP over the VPN with good QoS, each site must use private, dedicated transport lines to connect their respective locations to the Internet.
The firewall must be configured to support tunneling of VPN traffic. Tunneling is a method for ensuring that packets traverse the public Internet in a secure manner that prevents disruption. With this type of network infrastructure, each location’s LAN is secure from outside Internet threats and VoIP telephony traffic is carried over the Internet.
Three major categories of firewalls are available. Each comes with a different price tag and level of sophistication or complexity. Depending on the firewall, a company may need to have full-time skilled staff or corresponding contractors available to set up, program, and maintain the system.
The three types of firewalls follow:
Packet filter: This is a simple firewall that entails only nominal cost. Some are even free. Consumers, mobile users, and very small businesses use the low-end flavors that cost from $0 to $59. Some small companies use router devices that come preprogrammed with this level of firewall security and cost from $800 to $2500.
Proxy server: Full-fledged proxy servers tend to be complex to establish and maintain. They are more suitable for use at a single location. Because they must first permit unwanted packets on the network before they can discard such traffic, they are controversial in multisite networks. Costs range from $5000 to $15,000.
Stateful event monitor (SEM): These firewalls are the most comprehensive and therefore the most complex. They are typically used in large networks that have an inside protected network that needs to be separated, at the physical layers of the network, from their public Internet access network and their semipublic intranet network. SEM firewalls can examine the entire contents of any packet it sees, make decisions based on any field contained in the packet, and, like any firewall, can reject any packet from access into the company’s protected network or even to its intranet. SEMs include extensive network management capabilities. Costs range from $24,000 to $35,000.
Figure 9-4 illustrates how a SEM firewall does its duties. This is the same type of firewall used in large networks, such as those shown in Figure 9-1. Most large corporate networks don’t use VoIP over the Internet. VoIP packets instead traverse the company’s private dedicated network and never even see the other side of the firewall.
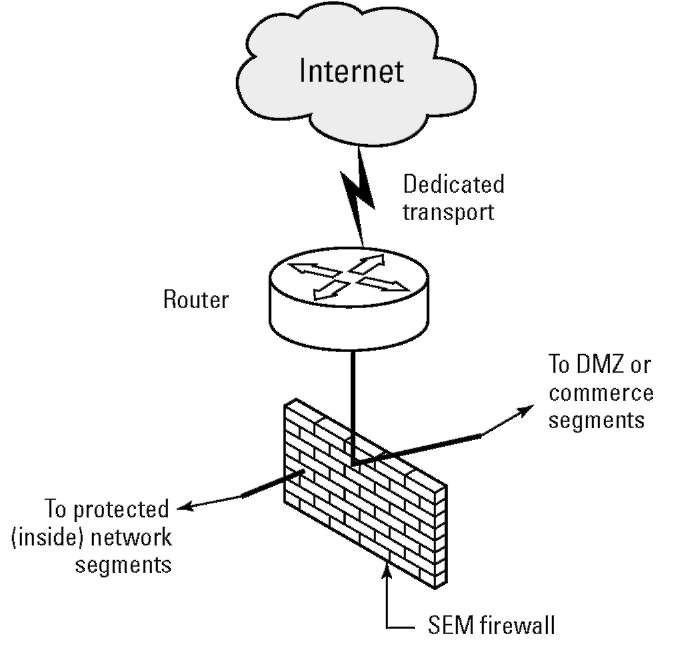
Figure 9-4:A SEM firewall.
A SEM firewall protects the network it runs on in many ways, but its main duty is to read packets that arrive at its “doorstep” and decide whether the packet is authorized to be there. If the packet is bad, the firewall discards it. If the packet is from a friendly network or user, packets that most likely are from customers and visitors, it may permit access to a portion of the company’s intranet. If the packet is from an employee or other authorized person, the firewall permits access to the inside protected network, to the resources the person is authorized to have.
If you have a VoIP phone that includes Web features — such as displaying Web pages — these features require fetching data that travels through the corporate firewall. This data, however, is standard Web data; it is not VoIP packets, which remain on the dedicated network.

