23.4
23.4.1
Case I: Interactive Voice Response (IVR) System
An interactive voice response (IVR) is a phone technology that allows a computer to detect voice and touch tones using a normal phone call. The IVR system can respond with prerecorded or dynamically generated audio to further direct callers on how to proceed [7]. The IP and traditional (i.e., PSTN) telephone networks are full of IVR systems where
FIGURE 23.3 Real-world attack scenario.
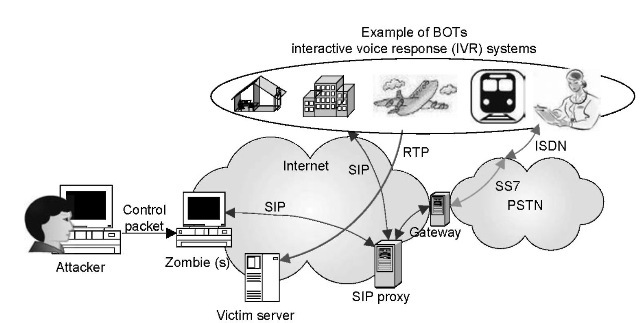
FIGURE 23.4 IVR systems acting as bots.
an user calling a telehone number is briefly interfaced with an automatic call response system. The typical usage of IVR includes call centers, bank and credit card’s account information system, air and rail’s reservation system, hospital’s helpline, University’s course registration system, etc.
As shown in Figure 23.4, imagine an attacker knowing this vulnerability sends out few hundred INVITE messages (while keeping the same media connection address in the message body) to well-known automatic call response systems and establishes fake call sessions with them. In response, the IVR systems flood the victimized connection address with UDP-based RTP packets. In order to establish a call, an exchange of few call setup SIP messages (i.e., INVITE/200 OK/ACK) can result in few hundreds to thousands of RTP packets. Such an attack scenario uses both reflection and amplification effect to make a DDoS attack more potent.
23.4.2
Case II: User’s Voicemail System
Sometimes when a callee is busy or he is not available to answer a phone call, the caller is directed to an answering machine or a voicemail system that plays a greeting message and stores incoming voice messages. An attacker may send fake call requests with the same media connection address to hundreds and thousands of individual telephone subscribers distributed over the Internet. The simultaneous playing of individual greeting messages can overwhelm the link’s bandwidth connecting to the victim.
23.4.3
Case III: User’s Voice Communication—RTP Stream
Even if we assume that the callee is not busy and answers a phone call, the callee’s voice stream (e.g., Hello, hello . . . or some other initial greeting message) can be directed to a target machine. As in the previous examples, an attacker sends fake call requests with the same media connection address to hundreds and thousands of individual telephone subscribers and simultaneous response of subscribers can cause a flooding attack on the victim.
23.4.4
Case IV: SPIT Prevention—The Turing Test
In many aspects a voice spam is similar to an e-mail spam. The technical know-how and execution style of e-mail spam can easily be adapted to launch voice spam attacks too. For example, first, a voice spammer harvests user’s SIP URIs or telephone numbers from the telephone directories or by using spam bots crawling over the Internet. In the second step, a compromised host is used as a SIP client that sends out call setup request messages. Finally, in the third step, the established sessions are played with pre-recorded WAV file. However, voice spam is much more obnoxious and harmful than e-mail spam. The ringing of telephone at odd time, answering a spam call, phishing attacks and inability to filter spam messages from voicemail box without listening to each one, are real nuisance and waste of time.
The Internet Engineering Task Force (IETF)’s request for comments (RFC) [8] analyzed the problem of voice spam in SIP environment examining various possible solutions that have been discussed for solving the e-mail spam problem and considered their applicability to SIP. One such solution is based on the Turing test that can distinguish computers from human. In the context of IP telephony, the machine-generated automated calls can be blocked by applying an audio Turing test. For example, a call setup request from an unidentified caller is sent to an IVR system where a caller may be asked to answer few questions or to enter some numbers through the keypad. The successful callers are allowed to go through the SIP proxy server and may also be added to a white list.
The VoIP security products such as NEC’s VoIP SEAL [9] and Sipera Inc.’s IPCS [10] have implemented audio Turing test as an important component in their anti-spam product to separate machine-generated automated calls from real individuals. However, an attacker may use these devices as reflectors and amplifiers to launch stealthy and more potent DDoS attacks. For example, to determine the legitimacy of a single spoofed INVITE message, these devices send few hundreds of RTP-based audio packets (assuming —1020 sec. of audio test) toward the media connection address of an INVITE message. A victimized connection address can be flooded with audio packets if an attacker sends one or two spoofed INVITE messages (with same media connection address) to several of such devices distributed over the Internet.
