23.5
23.5.1
Case I: Reconnaissance Attack
A subscriber’s liveliness (whether the device (i.e., phone or PC) is still connected to the Internet or not) can be checked by sending the captured INVITE message and observing the response messages. The INVITE message acts more than a ping packet as it checks the availability of the SIP machine at a particular host (corresponding to the address obtained from the captured INVITE message). However, this approach generates a false ring at the subscriber’s telephone. Therefore, as a substitute, the INVITE message header fields can also be used to create a SIP OPTION message pinging the host at application layer.
23.5.2
Case II: Nuisance Attack
A telephone starts ringing after receiving an INVITE message and keeps on ringing until either a callee picks it up or a (486 Busy Here) response message is send back to the caller.
To harass a particular subscriber, the captured INVITE message (belonging to that particular subscriber) can be replayed again and again ringing his/her telephone at odd times.
23.5.3
Case III: Flooding Attack
The flooding attacks are the most severe threats to VoIP systems, perhaps due to its simplicity and the abundance of tool support. A captured INVITE message can be played in quick session to flood a victim with INVITE requests. This simple attack is potent enough to bring down the telephone adapter and cause a DoS attack on a particular subscriber.
23.5.4
Case IV: Phishing Attack
In the previous attacks, the integrity of INVITE messages remained intact. However, by changing the INVITE parameters, it is possible to launch a phishing attack too. For example, in phishing attack, an attacker modifies the INVITE header fields to represent himself as a financial institution and tries to steal the subscriber’s personal information. An unwitting subscriber believing on spoofed caller-ID, easily provides account number and PIN.
23.5.5 Case V: CANCEL/BYE DoS Attacks
The CANCEL method is used to terminate pending searches or call attempts. Specifically, it asks the UAS to cease the request processing and generate an error response to the request. In general, a CANCEL is for an outstanding INVITE request that can be generated for an UA or the proxy servers that have received 1xx response, but still waiting for the final 2xx response. When a caller has received the response message 200 OK, the session is considered to be established. An established media session is terminated upon receiving an end-to-end BYE message. A malicious user can send a fabricated CANCEL/BYE message to cause a DoS attack on a specific telephone subscriber.
23.5.6
Case VI: Media Stream Redirection Attack
An attacker may send a fabricated re-INVITE message (with spoofed media IP address) to a callee redirecting the RTP flow to another location. As a result, the two-way communication between the caller and a callee is broken and possibly the attacker may also barge in and establish a communication channel with the callee.
23.5.7
Case VII: SIP Fuzzing DoS Attack
In fuzzing attack, the SIP protocol machine at the callee side is fed with crafted SIP messages carrying unexpected and faulty parameter values. The vendor’s implementation of the SIP protocol machine is targeted for security vulnerabilities such as buffer overflow, unhandled exceptions etc. causing malfunctioning or crashing of the protocol machine.
23.5.8
Case VIII: Spam Attack
Contrary to popular belief that the launching of spam attack requires specialized tool, we show that by replaying SIP signaling messages and prerecorded voice messages, spam voice messages can be send to telephone subscribers. For example, as shown in Figure 23.5, the replay of INVITE and ACK messages (maintaining the same relative order with respect
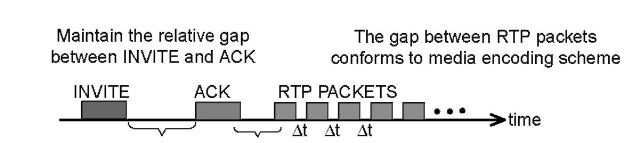
FIGURE 23.5 Spam attack on a subscriber.
to time) establishes a spam call session. Once a call session is established, a RTP stream is pushed toward the subscriber.
Further, it should be noted that the above attack list is not exhaustive. An attacker may monitor the signaling traffic flow to gain information such as the nature of traffic and load besides behavior and identity of subscribers.
