The Wireshark GUI is the gateway to unraveling the mystery of your VoIP calls. It allows you to start packet captures, end packet captures, and sort the data that you get from those captures. The main window for the Wireshark GUI consists of
Menu bar: Contains drop-down lists of options for the standard applications. The only two items on this bar you use when capturing and analyzing VoIP calls are the Capture section (if you’re starting captures from the GUI) and the Statistics section (to isolate VoIP calls).
Tool bar: Provides buttons to quickly start and stop captures, as well as navigate quickly through a capture. These are great shortcut buttons that you should investigate after you’re comfortable with the basics of Wireshark packet capture and analysis.
‘ Filter bar: You use this bar frequently. The Filter: button automatically generates the filters that Wireshark uses in many instances. You need to generate a filter manually only if you’re isolating RFC2833 DTMF packets to investigate why your DTMF touch tones aren’t being sent or received properly.
Data windows: Wireshark displays the data from the packet capture in these three windows allowing you to analyze the SIP banter on the call between the SIP nodes:
• Summary: Provides a summary of the packet captured. The SIP methods and responses are displayed in this section, allowing you to see a high-level overview of the packets that make up the VoIP call.
• Protocol Tree: This window displays the nuts and bolts of the SIP information. Selecting a row in the Summary window populates the specifics for that packet in the Protocol Tree window. The Protocol
Tree window allows you to expand the SIP messaging, the SDP, and the RTP to view the specifics of each and validate the information provided and negotiated.
• Data View: The Data View window shows the raw data collected in the capture and highlights the information that corresponds to the element of the protocol tree you’ve selected. You don’t use this section of the screen for VoIP call analysis because you can find all the data you require in plain English in the Summary and Protocol Tree windows.
Figure 11-2 shows a VoIP call capture displayed with Wireshark. Opening a capture with Wireshark is very easy. As long as the capture being opened has the .pcap suffix, Wireshark may be automatically selected to open it. If it doesn’t default to Wireshark, you can either
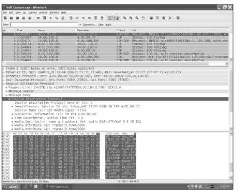
Figure 11-2:
The Wireshark GUI.
Right-click the file and select Open With. As long as you have Wireshark loaded on the computer, it will be listed on the pop-up menu of programs, and you can click on it to select it.
Open Wireshark and then choose FileOOpen from the main Menu bar. A pop-up window allows you to navigate around your computer to find the Wireshark capture file you want to view. Highlight the desired file and click the open button to view the file with Wireshark.
After the file opens, the entire content of the capture is displayed, as shown in Figure 11-2.
Using the Summary window
The Summary window of Wireshark provides you with an overview of the packets in the capture.
The capture covers everything flowing through the device during the time the capture was open. If the capture was executed on your Internet facing router, it’ll probably have TCP/IP traffic from Web surfing and e-mails, as well as the packets of your VoIP calls.
The data in the Summary section is grouped into six columns:

Number: This column identifies the frame number of the capture. This very helpful section of the Summary window allows you to reference a specific line in the capture when speaking to someone. The capture in Figure 11-2 has an INVITE message sent in frame 1 and in frame 3. If you’re sending the capture to your vendor for analysis, it’s easier to speak about “the INVITE in frame 3″ rather than “the second INVITE.”
Time: This column identifies the duration of time elapsed in the capture until the packet arrived. For example Figure 11-2 shows that, packet number 5 arrived 0.144084 seconds after the capture was started. This section provides the timeline from which you can track how much time passed between packets or events.
Source: This is the IP address of the device that originated the VoIP packet listed.
Destination: This is the IP address of the device to which the VoIP packet was sent. The INVITE packet in frame 1of Figure 11-2 was sent
from the Source of 4.00.00.00 to the destination IP of 24.00.100.0.
Protocol: This column identifies whether the packet listed was SIP, SIP/ SDP, RTP, T.38, or UDPTL. Not every SIP packet contains SDP, so you can skip to the important packets as you need.
Info: The Info column provides a summary of what’s being said in the packet. In this column, you see whether the packet was an INVITE, 100 Trying, 180 Ringing, or 200 OK or ACK, to name a few.
The Summary window provides the general information allowing you to identify specific packets that need further investigation.
Branching into the protocol tree
Selecting a row of data in the Summary section of Wireshark populates the Protocol Tree window with all the information contained in that packet. The information is displayed from general to specific, and you can expand each section to reveal more detailed information by clicking the plus sign (+) to the left of the section.
The example provided in Figure 11-2 has the first INVITE message in packet 1 selected, displaying the specifics for it in the Protocol Tree window, including
‘ Frame: Lists the size of the frame captured.
‘ Ethernet: Covers data from layer 2 of the OSI model on the frame. (More information on the OSI model is available in topic 5.)
Internet Protocol: The origination and destination IP addresses.
User Datagram Protocol (UDP): This would be TCP in a standard Internet packet. The example in Figure 11-2 shows that the standard SIP signaling port of 5060 is being used for the source and the destination.
Session Initiation Protocol: Used to research SIP and higher level VoIP issues. Expanding the lower-level section of the SIP protocol reveals the specifics of the IP addresses, ports, and codecs offered or established in the call. The SIP message in Figure 11-2 is expanded to show:
• Request Line
• Message Header
• Message Body
• SDP
topic 2 and topic 3 show normal SIP header and SDP information in detail. The Protocol Tree window of Wireshark allows you to see the specifics for the selected packet, ensuring that protocol mismatches or blatant SIP handshaking issues aren’t affecting the packet.
