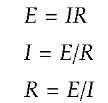Ohm’s Law
Ohm’s Law is the mathematical relationship among electric current, resistance, and voltage. The principle is named after the German scientist Georg Simon Ohm. In direct-current (DC) circuits, Ohm’s Law is simple and linear. Suppose a resistance having a value of R ohms carries a current of I amperes. Then the voltage across the resistor is equal to the product IR. There are two corollaries. If a DC power source providing E volts is placed across a resistance of R ohms, then the current through the resistance is equal to E/R amperes. Also, in a DC circuit, if E volts appear across a component that carries I amperes, then the resistance of that component is equal to E/I ohms.
Mathematically, Ohm’s Law for DC circuits can be stated as three equations:
When making calculations, compatible units must be used. If the units are other than ohms (for resistance), amperes (for current), and volts (for voltage), then unit conversions should be made before calculations are done. For example, kilohms should be converted to ohms, and microamperes should be converted to amperes.
ohnosecond
An ohnosecond is that very short moment in time during which you realize that you have pressed the wrong key and deleted hours, days, or weeks of work.
OK
OK (pronounced oh-KAY and occasionally spelled okay) is a short way to say ”I agree.” It’s sometimes encountered in computer messages that seek the user’s confirmation of a request.
OLE
OLE (Object Linking and Embedding) is Microsoft’s framework for a compound document technology. Briefly, a compound document is something like a display desktop that can contain visual and information objects of all kinds: text, calendars, animations, sound, motion video, 3-D, continually updated news, controls, and so forth. Each desktop object is an independent program entity that can interact with a user and also communicate with other objects on the desktop. Part of Microsoft’s ActiveX technologies, OLE takes advantage and is part of a larger, more general concept, the Component Object Model (COM) and its distributed version, DCOM. An OLE object is necessarily also a component (or COM object). Some main concepts in OLE and COM are: Microsoft terms are shown first; industry or alternative versions of those terms are shown in parentheses:
|
Concept |
What it is |
|
OLE |
A set of APIs to create and display a |
|
(compound) document |
|
|
Document |
A presentation of different items |
|
(compound |
in an ”animated desktop” |
|
document) |
|
|
Item (object; |
An element in a document, such |
|
also called a |
as an animated calendar, a video |
|
component) |
window, a sound player, a sound |
|
file… |
|
|
Container or |
The program entity that holds a |
|
container |
document or a control |
|
application |
|
|
Server or server |
The program entity that holds |
|
application |
an item within an OLE container |
|
Embedding |
Adding the source data for an item |
|
to a document; use the Paste |
|
|
command in a container application |
|
|
Linking |
Adding a link to the source data for |
|
an item to a document; use the Paste |
|
|
Link command in a container |
|
|
application |
|
|
Visual editing |
Activating an item that is embedded |
|
in a document and ”editing” it |
|
|
Automation |
Having one container or server |
|
application drive another applica- |
|
|
tion |
|
Concept |
What it is |
|
Compound files |
A standard file format that |
|
(structured |
simplifies the storing of (com |
|
storage) |
pound) documents; consists of |
|
storages (similar to directories) and |
|
|
streams (similar to files) |
|
|
Uniform Data |
A single data transfer interface |
|
Transfer (UDT) |
that accommodates drag-and-drop; |
|
clipboard; and dynamic data |
|
|
exchange (DDE) |
|
|
Component |
Provides the underlying support |
|
Object Model |
for OLE items (objects) and |
|
(COM) |
ActiveX controls to communicate |
|
with other OLE objects or ActiveX |
|
|
controls |
|
|
ActiveX control |
An item (object) that can be |
|
distributed and run on top of a COM |
|
|
Microsoft |
A set of ready-made classes or |
|
Foundation |
templates that can be used to |
|
Class (MCF) |
build container and server |
|
library |
applications |
OLE contains about 660 new function calls or individual program interfaces in addition to those already in Win32. For this reason, Microsoft provides the Microsoft Foundation Class (MFC) Library, a set of ready-made classes that can be used to build container and server applications, and tools such as Visual C++.
In the ”Introduction to OLE” on its Developer Site, Microsoft says that ”OLE” no longer stands for ”Object Linking and Embedding,” but just for the letters ”OLE.”
OLE DB
OLE DB is Microsoft’s strategic low-level application program interface (API) for access to different data sources. OLE DB includes not only the Structured Query Language (SQL) capabilities of the Microsoft-sponsored standard data interface Open Database Connectivity (ODBC) but also includes access to data other than SQL data. As a design from Microsoft’s Component Object Model (COM), OLE DB is a set of methods (in earlier days, these might have been called routines) for reading and writing data. The objects in OLE DB consist mainly of a data source object, a session object, a command object, and a rowset object. An application using OLE DB would use this request sequence:
1. Initialize OLE.
2. Connect to a data source.
3. Issue a command.
4. Process the results.
5. Release the data source object and uninitialize OLE. OLE once stood for ”Object Link Embedding” and ”DB” for database. However, Microsoft no longer ascribes these meanings to the letters ”OLE” and ”DB.”
OLTP
OLTP (online transaction processing) is a class of program that facilitates and manages transaction-oriented applications, typically for data entry and retrieval transactions in a number of industries, including banking, airlines, mailorder, supermarkets, and manufacturers. Probably the most widely installed OLTP product is IBM’s CICS (Customer Information Control System).
Today’s online transaction processing increasingly requires support for transactions that span a network and may include more than one company. For this reason, new OLTP software uses client/server processing and brokering software that allows transactions to run on different computer platforms in a network.
on the fly
In relation to computer technology, ”on the fly” describes activities that develop or occur dynamically rather than as the result of something that is statically predefined. For example, the content of a page that is sent to you from a Web site can be developed (and varied) ”on the fly” based on dynamic factors such as the time of day, what pages the user has looked at previously, and specific user input. The Web server calls an application program to produce the ”on-the-fly” page that is to be returned. There are several techniques for on-the-fly page development, including the server-side include, the use of cookies (information previously stored about you that is located in a special file on your hard disk), and Microsoft’s Active Server Page.
In general usage, the expression often connotes a degree of haste and improvisation as in ”I usually grab breakfast on the fly.” This usage is somewhat similar to the expression ”catch as catch can.” The term also can simply connote being in a mobile or fluid situation. Our Webster’s New World Dictionary reminds us that the term probably originated with bird hunting and shooting birds on the fly (rather than on the ground). The dictionary says simply ”in flight” and adds a colloquial meaning of ”in a hurry.”
one-armed router
A one-armed router is a router that routes traffic between virtual local area networks (VLANs). A one-armed router operates on the 80/20 rule, which states that 80% of traffic in a network remains within a virtual local area network and doesn’t need routing service. The other 20% of network traffic is between VLANs and goes through the one-armed router. Because the one-armed router takes care of the more intensive traffic between VLANs, it frees the primary data path in a network for inter-VLAN traffic.
In order for a one-armed router to be beneficial, the VLAN must be configured to the 80/20 rule. One disadvantage of using the one-armed router structure is that it represents a single point of failure in a network. Another disadvantage is it can develop into a bottleneck if there are large amounts of traffic between VLANs.
one-time pad
In cryptography, a one-time pad is a system in which a private key generated randomly is used only once to encrypt a message that is then decrypted by the receiver using a matching one-time pad and key. Messages encrypted with keys based on randomness have the advantage that there is theoretically no way to ”break the code” by analyzing a succession of messages. Each encryption is unique and bears no relation to the next encryption so that some pattern can be detected. With a onetime pad, however, the decrypting party must have access to the same key used to encrypt the message and this raises the problem of how to get the key to the decrypting party safely or how to keep both keys secure. One-time pads have sometimes been used when the both parties started out at the same physical location and then separated, each with knowledge of the keys in the one-time pad. The key used in a one-time pad is called a secret key because if it is revealed, the messages encrypted with it can easily be deciphered. One-time pads figured prominently in secret message transmission and espionage before and during World War II and in the Cold War era. On the Internet, the difficulty of securely controlling secret keys led to the invention of public key cryptography.
How It Works
Typically, a one-time pad is created by generating a string of characters or numbers that will be at least as long as the longest message that may be sent. This string of values is generated in some random fashion—for example, by someone pulling numbered balls out of a lottery machine or by using a computer program with a random number generator. The values are written down on a pad (or any device that someone can read or use). The pads are given to anyone who may be likely to send or receive a message. Typically, a pad may be issued as a collection of keys, one for each day in a month, for example, with one key expiring at the end of each day or as soon as it has been used once.
When a message is to be sent, the sender uses the secret key to encrypt each character, one at a time. If a computer is used, each bit in the character (which is usually eight bits in length) is exclusively ”OR’ed” with the corresponding bit in the secret key. (With a one-time pad, the encryption algorithm is simply the XOR operation. Where there is some concern about how truly random the key is, it is sometimes combined with another algorithm such as MD5.) One writer describes this kind of encryption as a ”100% noise source” used to mask the message. Only the sender and receiver have the means to remove the noise. Once the one-time pad is used, it can’t be reused. If it is reused, someone who intercepts multiple messages can begin to compare them for similar coding for words that may possibly occur in both messages.
online
Online is the condition of being connected to a computer or a telecommunications system. The term is frequently used to describe someone who is currently connected to the Internet.
Deprecated spellings are on-line and on line. The opposite term is offline.
online analytical processing
Online analytical processing (OLAP) enables a user to easily and selectively extract and view data from different points-of-view. For example, a user can request that data be analyzed to display a spreadsheet showing all of a company’s beach ball products sold in Florida in the month of July, compare revenue figures with those for the same products in September, and then see a comparison of other product sales in Florida in the same time period. To facilitate this kind of analysis, OLAP data is stored in a multidimensional database. Whereas a relational database can be thought of as two-dimensional, a multidimensional database considers each data attribute (such as product, geographic sales region, and time period) as a separate ”dimension.” OLAP software can locate the intersection of dimensions (all products sold in the Eastern region above a certain price during a certain time period) and display them. Attributes such as time periods can be broken down into subattributes.
OLAP can be used for data mining or the discovery of previously undiscerned relationships between data items. An OLAP database does not need to be as large as a data warehouse, since not all transactional data is needed for trend analysis. Using Open Database Connectivity (ODBC), data can be imported from existing relational databases to create a multidimensional database for OLAP.
Two leading OLAP products are Arbor Software’s Essbase and Oracle’s Express Server. OLAP products are typically designed for multiple-user environments, with the cost of the software based on the number of users.
online service provider
1) On the Internet, OSP (online service provider) has several different meanings.
• The term has had some currency in distinguishing Internet access providers that have their own online independent content, such as America Online (AOL), from Internet service providers (ISPs) that simply connect the user directly with the Internet. In general, the companies sometimes identified as OSPs (in this usage) offer an extensive online array of services of their own apart from the rest of the Internet and sometimes their own version of a Web browser. Connecting to the Internet through an OSP is an alternative to connecting through one of the national Internet service providers, such as AT&T or MCI, or a regional or local ISP.
• Some Internet service providers (ISPs) describe themselves as online service providers. In this usage, ISP and OSP are synonyms.
• America Online has used the term to refer to online content providers (usually Web sites) with which AOL has a business agreement.
2) Some companies use OSP in describing themselves as office service providers.
ontology
In its general meaning, ontology (pronounced ahn-TAH-luh-djee) is the study or concern about what kinds of things exist—what entities there are in the universe. It derives from the Greek onto (being) and login (written or spoken discourse). It is a branch of metaphysics, the study of first principles or the essence of things.
In information technology, an ontology is the working model of entities and interactions in some particular domain of knowledge or practices, such as electronic commerce or ”the activity of planning.” In artificial intelligence (AI), an ontology is, according to Tom Gruber, an AI specialist at Stanford University, ”the specification of conceptualizations, used to help programs and humans share knowledge.” In this usage, an ontology is a set of concepts—such as things, events, and relations—that are specified in some way (such as specific natural language) in order to create an agreed-upon vocabulary for exchanging information.
OPAC
An OPAC (Online Public Access Catalog) is an online bibliography of a library collection that is available to the public. OPACs developed as stand-alone online catalogs, often from VT100 terminals to a mainframe library catalog. With the arrival of the Internet, most libraries have made their OPAC accessible from a server to users all over the world.
User searches of an OPAC make use of the Z39.50 protocol. This protocol can also be used to link disparate OPCS into a single ”union” OPAC.
open
1) In information technology, a product or system is described as open when its workings are exposed to the public and capable of being modified or improved by anyone. The alternative is a proprietary product or system. Also see open source.
2) In programming, to open (verb) a file or unit of data is to make it accessible for reading and writing. An open file is one that is ready to be read or written to.
Open Buying on the Internet
OBI (Open Buying on the Internet) is a proposed standard for business-to-business purchasing on the Internet, aimed particularly at high-volume, low-cost-per-item transactions. OBI uses a number of security technologies such as the digital certificate to allow orders to be placed and filled securely. On average, 80% of company purchasing is for non-production supplies such as office supplies, cleaning products, and computer equipment. Making and fulfilling an order can cost an organization up to $150 and the seller up to $50. In the fall of 1996, the Internet Purchasing Roundtable, a group of Fortune 500 buying organizations and their suppliers met to develop an open standard for business-to-business e-commerce. The result—OBI—is intended to eliminate redundant work in purchasing, minimize errors, and reduce labor and transaction costs.
There are four entities involved in an OBI transaction: The requisitioner, the buying organization, the selling organization, and the payment authority. The requisitioner is the person who places the order and must have a digital certificate for authentication. The buying organization maintains an OBI server that receives OBI order requests and approves them. The buying organization also negotiates and maintains contracts with selling organizations. It is the responsibility of the selling organization to provide a catalog tailored to each department in each company, maintain products and prices based on contracts with the buying organization, and authorize payments with the appropriate payment authority.
An OBI transaction is done without the user needing special knowledge of the OBI process. With OBI, a purchaser needs only a computer, an Internet connection, a Web browser, and an OBI-compliant application. The following is a typical OBI scenario:
• A janitor needs to purchase some cleaning supplies. Using the stockroom computer, the janitor connects to the organization’s purchasing server using a Web browser.
• The janitor selects a merchant from a list on the purchasing department’s home page and is authenticated by the merchant’s server.
• The janitor views a catalog that is tailored to company needs and selects the needed cleaning supplies. The janitor clicks a button to submit the order, which is then formatted into the Electronic Data Interchange (EDI) format. The order is then encapsulated into an OBI object.
• The janitor’s order is sent to the buying organization in the company for approval using Hypertext Transfer Protocol (HTTP) and Secure Sockets Layer (SSL). The buying organization decodes the OBI object and approves the order.
• The order is sent to the merchant and fulfilled.
• The merchant submits the payment to a payment authority.
• The payment authority sends the billing data to the company’s billing department.
OBI architecture, technical specifications, guidelines, and compliance and implementation information is available at the OBI Consortium Web site. Future OBI versions will include international support and the use of Extensible Markup Language (XML) data formats.
Open Database Connectivity
Open Database Connectivity (ODBC) is an open standard application programming interface (API) for accessing a database. By using ODBC statements in a program, you can access files in a number of different databases, including Access, dBase, DB2, Excel, and Text. In addition to the ODBC software, a separate module or driver is needed for each database to be accessed. The main proponent and supplier of ODBC programming support is Microsoft.
ODBC is based on and closely aligned with The Open Group standard Structured Query Language (SQL) Call-Level Interface. It allows programs to use SQL requests that will access databases without having to know the proprietary interfaces to the databases. ODBC handles the SQL request and converts it into a request the individual database system understands.
ODBC was created by the SQL Access Group and first released in September, 1992. Although Microsoft Windows was the first to provide an ODBC product, versions now exist for UNIX, OS/2, and Macintosh platforms as well.
In the newer distributed object architecture called Common Object Request Broker Architecture (CORBA), the Persistent Object Service (POS) is a superset of both the Call-Level Interface and ODBC. When writing programs in the Java language and using the Java Database Connectivity (JDBC) application program interface, you can use a product that includes a JDBC-ODBC "bridge" program to reach ODBC-accessible databases.