The Cisco VPN Client does not have built-in support for IPv6 like the Cisco AnyConnect solution does. However, it is still possible to support IPv6 through a Cisco VPN Client connection by using host-based tunnels (dynamic or static). One example of this is to leverage Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) (RFC 5214) on the remote client along with an established Cisco VPN Client connection. Remember that ISATAP is a host-based tunnel that can provide tunneled IPv6 connectivity between the host and a router, Layer 3 switch, or server. The idea is that after a Cisco VPN Client connection has been made, there should be a routing path between the host and the tunnel endpoint located inside the enterprise network. The Cisco VPN Client enables tunneled traffic through the IPv4 IPsec connection.
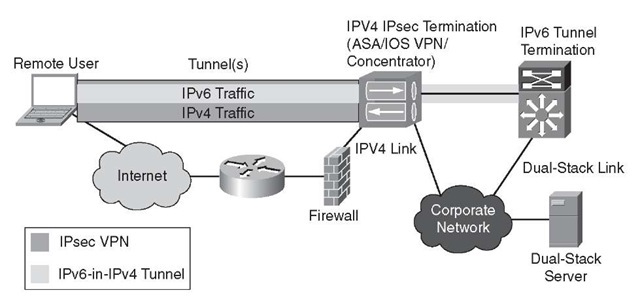
Figure 10-4 shows an example topology where there is a remote user connecting to a Cisco IPsec VPN termination device (for example, Cisco IOS, ASA, 3000 Concentrator) over an IPv4 IPsec session. After that connection is made, the ISATAP (or other host tunnel type) tunnel is established between the remote host and the IPv6 tunnel termination point inside the enterprise network. After the ISATAP tunnel has been terminated, the IPv6 traffic can be routed to its destination over a dual-stack or native IPv6-only connection. In this model, IPv6 security access control lists (ACL) and inspection needs to be applied to IPv6 traffic after decapsulation inside the enterprise (that is, the internal IPv6 tunnel termination point).
Figure 10-4 Using the Cisco VPN Client with Host-Based Tunnels
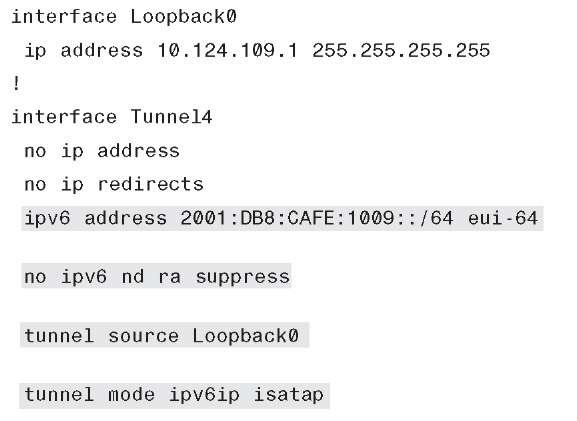
Example 10-3 shows the basic ISATAP configuration deployed inside the enterprise. A tunnel interface is defined on an internal Cisco IOS router or Layer 3 switch such as a Catalyst 6500 Supervisor 720. An IPv6 prefix is configured, and the interface ID uses a modified EUI-64-derived address (as defined in RFC 4291). This prefix will be used by the ISATAP client after it is connected. The default tunnel behavior in Cisco IOS is to disable router advertisements (RA). Because this tunnel is going to be connecting to multiple endpoints and the IPv6 prefix needs to be learned by those endpoints, RAs need to be sent. This is accomplished by turning off the default suppression of RAs. The tunnel source is the loopback on the router, and there is no tunnel destination because the "isat-ap" tunnel mode implies multipoint tunnel functionality.
Note The VPN termination device configuration is not shown because it is transparent to the actual IPv6 traffic.
Example 10-3 ISATAP Configuration for a Cisco VPN Client
As discussed in next topic, ISATAP can learn about the ISATAP router by either using a static configuration or dynamically through a DNS lookup. The static configuration is the recommended way to start because it enables granular control of when, how, and who can leverage ISATAP in the enterprise. The following command is used on a Microsoft Windows operating system and statically identifies the router interface (the loopback interface on the router). This statement can be an IPv4 address or host name (as resolved in DNS). In this example, the set router 10.124.109.1 statement is the IPv4 address configured on interface Loopback0—the source of the ISATAP tunnel.
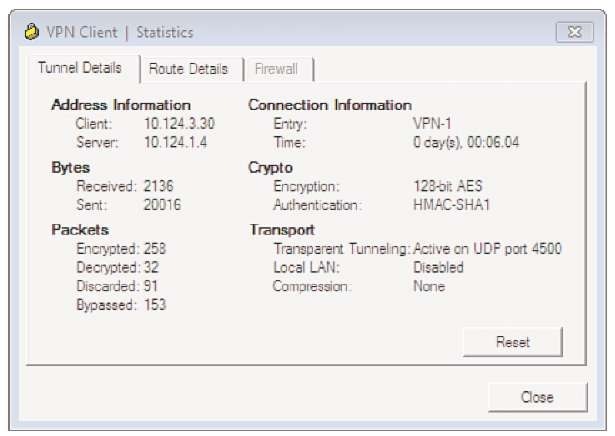
Figure 10-5 shows that the client has a Cisco VPN Client session and that the client address is 10.124.3.30.
Figure 10-5 Cisco VPN Client Session
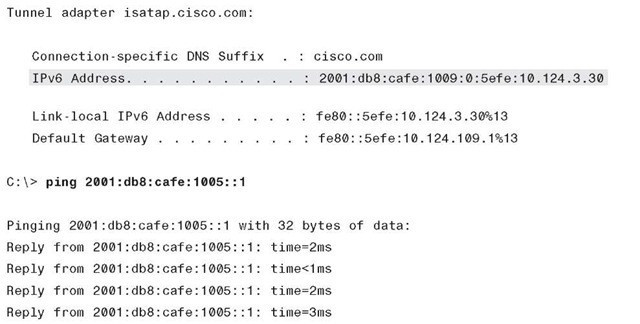
Example 10-4 is a summarized output from the Microsoft Windows 7 ipconfig command. The output shows that the IPv6 address of the client is 2001:db8:cafe:1009:0:5efe:10.124.3.30. The 2001:db8:cafe:1009 is the prefix defined on the Tunnel4 interface from Example 10-4. The 0:5efe is the ISATAP interface identifier as defined in RFC 5214. The 10.124.3.30 is the value that is derived from the client’s IPv4 address.
Example 10-4 also shows that the client can successfully ping a host inside the enterprise network.
Example 10-4 Microsoft Windows ipconfig and ping Output
Summary
You need to account for access to IPv6-enabled services and applications from anywhere within and outside of the enterprise. IPv6 access over remote VPN solutions is maturing. Cisco provides IPv6 access over Cisco AnyConnect, which is based on SSL VPN, and this solution enables dual-stack access to the enterprise. If the Cisco VPN Client over IPsec is being leveraged today, it is recommended to move to the Cisco AnyConnect solution. If it is not possible to move to Cisco AnyConnect and IPv6 access is required in the near term, host-based tunnels (ISATAP, 6to4, manual, and so on) can be leveraged to provide a remote client access over the Cisco VPN Client IPsec session.