INTRODUCTION
Most large organizations that provide Internet access to employees also employ some means to monitor and/or control that usage (Reuters, 2002). A 2005 AMA report indicates that 76% of companies monitor worker’s Web surfing, while 26% have fired workers for improper Internet usage (AMA, 2005). This chapter provides a classification and description of various control mechanisms that an organization can use to curb or control personal Internet usage. Some of these solutions are technical, while others rely instead on interpersonal skills to curb cyberslacking.
After a review of goals for a monitoring program, a list of different activities to monitor and/or control will also be provided. Then a discussion of different techniques for monitoring and associated products will be explored, followed by a discussion of fit between corporate culture and monitoring.
BACKGROUND
The Worker’s Perspective
In this age of cell phones, pagers, wireless PDAs, e-mail, and home network links, many employees may feel like the employer owns them notjust during the workday, but perhaps constantly. Though tiresome, the worker may accept this as an unfortunate circumstance of 21st century knowledge work. However, in the tit-for-tat that this availability demands, the employee may feel that he or she should be allowed to use the Internet at work to take care of quick business tasks such as paying bills, sending an e-mail, or checking that evening’s movie listings. So long as it isn’t excessive, the employee may wonder why the employer even cares. Employers can and do care for many reasons, some more profound than others.
Goals for Monitoring
Why do companies monitor their employees? Organizations monitor for many reasons including simply “because they can.” An electronic monitoring effort is often difficult to establish and maintain, so before an organizationbegins such an effort, there should be clear monitoring goals.
The popular press is filled with stories of employees frittering away time on the Internet (Swanson, 2002). In the beginning, employees were likely to spend unauthorized time on the Internet at pornography and gambling sites, but now news and online shopping are more likely outlets for cyberslacking (Reuters, 2002). This is quite the opposite of employers’ expectations when they implemented Internet connections.
Responding to these challenges, employers created acceptable use policies (AUPs). Some organizations already had AUPs implemented to keep out electronic games, and they simply modified those policies. Other organizations created new AUPs, which directly addressed the Internet’s productivity threat. AUPs are useless without enforcement, but in today’s litigious society it behooves accusers to be certain of transgressions before enforcing the policy. Monitoring tools create an irrefutable log of usage which can stand as legal evidence. Some employers hope the mere threat of punishment will keep employees from cyberslacking, often with some success (Urbaczewski & Jessup 2002). Listed next are some possible goals of a monitoring effort.
Increase Employee Productivity
The Internet was introduced into many organizations as a tool to increase employees’ efficiency. While traditional IT packages provided few opportunities for employees seeking to slouch on employer time, the Internet posed an entirely different situation. Computers now had the capability to be an electronic equivalent of a water cooler, break room, or smokers’ perch. To curb the potential problem of employees wasting time while appearing to be busy, an organization could implement a monitoring program which completely blocks and/or records the amount of time spent at non-work-related Internet sites. An alternative could be limiting access to frivilous sites to non-production hours only, such as during lunchtime.
Bandwidth Preservation
In some organizations, concerns are not productivity-based but rather that network bandwidth is being dominated by applications and instances not directly work related. An example might be listening to streaming audio or watching streaming video, both constant drains on bandwidth. People can also engage in excessive file transfers across networks which results in reduced network performance. Two possible solutions to this problem are to purchase more bandwidth or limit the usage of existing bandwidth, with monitoring programs aiding in the latter solution.
Legal Liability Reduction
Along with productivity and bandwidth usage, organizations are also concerned about Internet usage from the potential exposure it brings to legal liability (Langin, 2005). Consider the following fictitious scenarios:
• “Organization X today was sued for negligence, as an employee was running a child pornography server inside the corporate network.”
• “ABC corporation today was sued by a former employee who is now in treatment with Gambler’s Anonymous. He is charging that ABC, by placing an unrestricted Internet terminal on his desktop, essentially gave him unfettered access to the virtual casinos thriving on the Internet.”
• “Company B is defending itself today against a privacy lawsuit. It is charged that when an employee downloaded a file-sharing program, that program was equipped with a backdoor, which allowed malicious hackers entrance into Company B’s networks. These hackers then took thousands of credit card numbers and personal data from the databases…” (a similar real-world incident happened with employees of the state of Oregon in May 2006, where about 2,200 taxpayers had their personal information compromised due to spyware picked up on a laptop computer by a worker surfing pornographic sites during downtime (Keizer, 2006).
Organizational Secret Protection
As blogging has become a popular way of communicaitng in the 21st century, many companies have realized that it is easy for employees to write their ideas and opinions about circumstances at their corporations, often with embarrassing results for the employee and/or the employer. Google and Microsoft are two well-known examples of companies that have dealt harshly with non-approved blogging by their employees, and a scandalous sex-for-money-and-favors blog detailing the life of a staffer in a U.S. Senator’s office caused much embarrassment for those involved. Organizations may not want their internatl business practices or daily routines exposed to the outside world, so they use control of blog postings to keep this control. While their control over employee postings when not in the office may be murky, the organization may exert its right to keep this control during business hours.
Other possibilities like sexual harassment suits and industrial espionage make the legal risks mount. Organizations indeed may wish to monitor Internet connections to prevent any potential legal liabilities from allowing illegal activities to be conducted on their networks.
STRATEGIES AND TECHNIQUES FOR MONITORING
Different Monitoring Strategies
Once an organization decides it will monitor, it needs to know what to monitor. While Web pornography is probably the most reported off-topic use of the Internet in an organization, it is certainly not the only transgression that might come from an Ethernet card. Excessive personal email, filesharing, instant messaging, multimedia streaming, and usenet browsing and posting are among other ways that employees use the corporate Internet connection for personal enjoyment.
There are several different control mechanisms that an organization might use, generally grouped into one of two categories: managerial and technical. The managerial techniques for monitoring are similar to ways that monitoring of employees has been done for decades: walking around and keeping one’s eyes open. When a manager starts to wonder about an employee’s performance or collegiality, then the manager starts to pay more attention to that employee’s work habits.
Overall, however, the most popular means of monitoring employees is through technology. In many ways, this makes sense—a technical solution to a technological problem. Electronic monitoring operates like “big brother” (Zuboff, 1988), keeping a constant watchful eye on the network and its connected systems (or whatever subset of those systems/ hours that a manager may choose to watch). Records can then be kept and offered as later “proof” of an offender’s cyberslacking or lack thereof.
Electronic Monitoring Techniques
Logging at the Gateway
Many logging technologies are designed to capture and record packets as they enter and leave the organization, or at least the header information that indicates the sender, recipient, and content of the message. Gateway logging is useful in that it provides a central point of network control. However, it is difficult to accurately gauge how long an employee stares at a particular page, and if all that time he or she is actually staring at that page or if he or she has actually gone to lunch and returned later. Moreover, gateway logging can be defeated by the use of encryption tools like PGP (www.pgp.com, see McCullagh (2001) for a more detailed description of an FBI case with the Phildelphia organized crime ring), or even tools like Anonymizer.com that allows a person to surf the Web anonymously using their gateways and encryption tools. In cases where these technologies are used, a separate technology might also be needed.
Blocking: Keeping Productive Employees Productive
Sixty-five percent of companies (AMA, 2005) utilize blocking software to keep employees from visiting certain Web sites. Organizations may not even look at the logs to see who was trying to view these sites–rather it serves simply as a friendly reminder that these sites are not to be viewed on company time. While the software is never foolproof, and relays can be used to get around the blocking software, it reminds the employees of the policies and makes a policy violator’s defense of “I didn’t know I wasn’t supposed to do this” less believable. Akin to locking the doors on one’s car that will not stop a determined thief, it does make the owner’s intentions known and makes the target less appealing.
Spying at the Client
When gateway logging is insufficient, one can monitor and record connections directly at the source. A keystroke logging program can record everything that a person types on a computer, and many even include technologies to take screenshots or use the Web camera on the desk to prove that it was the person actually sitting at the computer and not someone who just walked up to the terminal.
Client sniffing programs are excellent at recording exactly what the user is doing with the computer at any given time. Many will record all the user’s keystrokes, mouse movements, and active windows, allowing the reconstruction of the entire computing session. Moreover, they can capture other undesirable activity, such as playing games and typing job application letters. However, these programs are not without their own faults. First of all, the manager must install the program on the user’s computer, which may not be as easy as it sounds, especially with laptop and other mobile computers. Second, the program must not be detectable (and thus deletable) by the monitored employees. Managers then must sift through mountains of captured data to determine if there is any untoward activity, or enough to warrant further investigation. However, products are available which meet the above concerns to varying degrees, and the next section will discuss some of those products.
Software Products for Controlling Internet Usage
As previously mentioned, there are various products available to serve as control mechanisms. They are grouped below into five categories. Note that software products come and go, and the availability of certain products and companies are subject to market forces. The categories themselves should remain stable for the time being, although who knows what the future may hold. For example, if this chapter was being written in 1999, there would likely be no section on file-sharing.
Web Monitoring Products
As the popular press articles have largely focused on employee cyberslacking as a problem with personal Web usage, a number of products have been created to help employers manage these problems. The software products are all customizable to some degree, but there are two main classifications of these products: those that monitor and record Web usage, and those that actively block access to certain Web sites deemed inappropriate. The listing below, which is not intended to be exhaustive, details several of these products.
Cybersitter (www.cybersitter.com), NetNanny (www. netnanny.com), and Bsafe Online (www.bsafehome.com) are three programs that are geared largely at individuals, as they are installed on the client and maintain logs of Web pages seen by the users. Websense (www.Websense.com) however, is designed to monitor the Web usage of an entire network. It runs near the firewall and logs all Web requests leaving the network. All of these programs can be configured to block and/or record access to certain Web sites. Some of these programs can be tailored to allow different access rules at different times of day. For example, an organization may wish to allow its employees to use the Internet for shopping and other personal entertainment before and after normal business hours and on the lunch hour but not during the work day.
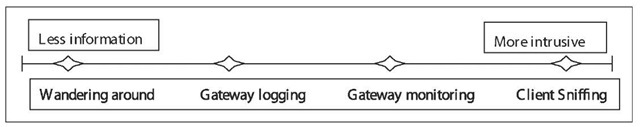
Figure 1. Monitoring strategies present a tradeoff between information and intrusiveness
E-Mail Monitoring Products
E-mail can easily be monitored by simply examining accounts for incoming mail or logging the actions of the simple mail transport protocol (SMTP) server for outgoing mail. These logs are often difficult to read, especially with large volumes of mail and users.A series ofproducts can assist in parsing the logs or searching for users or keywords, like MIMESweeper (www.mimesweeper.com) and message inspector (www. cyberguard. com). Encrypted e-mail can present its own challenges, and additional policies may be necessary regarding the use of strong encryption in an organization.
Monitoring e-mail sent through popular Web-based providers like Yahoo! or Hotmail can be difficult as well, because the message never passes through the SMTP servers for the organization, nor does the organization have direct control over users’ mailboxes. Monitoring these types of mail services is usually done through a general monitoring tool, as listed in another section below.
File-Sharing Monitoring Products
File-sharing has a history of waxing and waning between one of the easiest applications to monitor to one of the toughest. Users of file-sharing services often try to devise ways to run their services around and through corporate attempts to halt them. Other problems were created by users demanding that they be allowed to use these programs, especially at high-profile universities like Yale and Indiana. In those cases, something had to be done to limit the amount of bandwidth these services could use, because other legitimate traffic was being delayed. A number of hardware and software solutions cropped up to aid network managers in their quest to reduce or eliminate file-sharing traffic.
On the software side, it was previously mentioned that already existing firewalls can be configured to block traffic on certain TCP (OSI layer 4) ports. Other programs, like DynaComm I:scan (http://www.futuresoft.com/products/an-tispyware/overview), are designed to examine the packets at the application layer (OSI layer 7) to determine the type of packet and whether or not to block it. Hardware solutions like Packeteer (www.packeteer.com) plug into the network to control the amount of bandwidth available to certain applications. Packeteer has been most popular at colleges and universities, which in general do not want to be accused of censorship or limiting access to resources, but still have to deal with bandwidth concerns amongst thousands of users.
Instant Messaging (IM) Monitoring Products
IM’s “fire-and forget” nature made it one of the toughest applications to monitor for a long time. The problem was exacerbated because the employers generally did not control the IM servers or the clients. In 2002 applications were created which successfully monitor IM applications and content, implemented largely to comply with certain US Securities and Exchange Commission (SEC) requirements on keeping logs of all transactions between brokerage houses and their customers. Enterprise IM applications continue today with the likes of AIM Pro, an AOL and WebEx IM program designed for deployment within the organization and subject to its controls. IM is usually not monitored to conserve bandwidth, but it can become a productivity drain similar to e-mail.
Facetime (www.facetime.com) is probably the leader in monitoring organizational IM. The Facetime product can record all IM activity, important in SEC-regulated businesses and government agencies with freedom of information requirements. Vericept (www.vericept.com) also has all-purpose monitoring capabilities, but focuses largely on monitoring, blocking and recording IM activity. Organizations looking to block and monitor IM and communicate securely using encryption might turn to Compliancer Hub (www.communicatorinc.com).
General Monitoring (Spying at the Client) Tools
There are a series of more powerful, less-specific tools available for almost total user monitoring, classified as general monitoring tools. These tools are installed at the client and can create a record of almost everything a user does with the computer. Records can be written to a network database or even e-mailed to another account.
Spector CNE (www.spectorsoft.com) and Track4Win (www.track4win.com) are sniffing programs designed for enterprise monitoring. There are also many programs targeted at individuals, including Pearl Echo (www.pearlsw.com) and eBlaster (http://www.spectorsoft.com). Managers are often surprised at the sheer amount of data these programs provide, quite often more than a manager really wants to know. One should carefully consider the implications before implementing a general monitoring tool. Employees may react strongly to such total monitoring.
FUTURE TRENDS
Seeking the Recommended Fit between Goals and Monitoring Solutions
If productivity is a major concern, one might begin with a passive but comprehensive logging tool. Cyberslacking canbe easily seen and measured, but it is done unobtrusively. When an employee’s productivity falls, as observed traditionally, the technical data showing cyberslacking are available. This can be used for implementing positive disciplinary measures, or for supporting a termination. Periodically and when a situation occurs, employees should be reminded of the organization’s policy about personal Internet usage and resulting enforcement actions. This is not to embarrass potential offending parties, but rather to keep the policy salient.
If legal liability is the major concern, minimally intrusive means can also be used for the monitoring and recording of transmitted data. In December 2002, five major Wall Street brokerage houses were fined $1.65 million for not keeping e-mails the required two years. An organization can avoid these types of penalties by simply logging and maintaining records of Internet traffic without any review, except on an as required basis. The RIAA and other entertainment industry groups in early 2003 began warning organizations to actively ensure that their employees were not using company networks to access copyrighted music and video files, lest the companies themselves be held liable. The RIAA has been supplying offenders’ IP addresses and access times to companies and universities, idenitfying individuals who may have traded in music and video files. In the end, a company pursuing this strategy would be more concerned with record-keeping than record-reviewing.
An organization pursuing the third goal, bandwidth preservation can likely use the least passive of all monitoring tools–simply observing bandwidth usage spikes where they occur, and witnessing their relationship to organizational goals. A firm that sees bandwidth constantly full with apparently work-related material may want to investigate adding additional bandwidth resources. At the same time, organizations that suddenly block or “throttle” access to popular Internet destinations known for non-work related information will likely solve many problems. Employees are more likely to realize that they need to get to work or identify another means of entertainment than they are to complain and cause a ruckus over no longer being able to access these sites at all or at high speeds.
CONCLUSION
This chapter has detailed several types of control mechnisms. It has listed goals for monitoring, applications to monitor, and means of accomplishing the monitoring. Furthermore, it lists names of actual tools that can be used to accomplish the monitoring. What this chapter so far has not discussed is the viability and consequences of the monitoring.
In a series of studies, it was found (not surprisingly) that Internet monitoring indeed has a significant positive effect on keeping employees on task (Urbaczewski et al., 2002). However, it was also found that monitored employees were more likely to turnover and less likely to participate in other organizational activities. Could this happen in all organizations? Possibly, but the key to remember when establishing monitoring is: Make the monitoring strategy fit the corporate culture.
Some organizations have a culture where monitoring of most (if not all) activities is simply expected. These industries generally include those handling cash or financially-related transactions (e.g., banks, casinos) or deal with physical and/or national security (CIA, FBI, R&D labs, etc.). In these cases, monitoring fits the culture, and if the organization is already monitoring employees in other ways, it also makes sense to monitor computer systems.
Other organizations have cultures which generally detest monitoring. Some industries, like publishing, academia, and other “civil liberties” organizations do not generally monitor their employees, as their foundations are centered on freedom of speech and the unfettered search for the truth. The introduction of monitoring in these industries will likely result in a culture clash between employees and management (Simmers, 2002).
The question then becomes “how does one then reap the benefits of monitoring without angering employees and creating unwanted stress in the organization?” Valli (2004) argues for provisions that enforce policies while at the same time not destroying the atmosphere of trust and fairness. Communication of the control mechanisms to the employees, with a clear understanding of how it supports corporate goals and principles, is key. Explicit statements of who will be monitored, what will be monitored, and when monitoring will occur should also be communicated to the employees, largely through AUPs.
KEY TERMS
Acceptable Use Policy (AUP): A policy created in an organization to outline the permitted and restricted uses of the company’s networks and computer systems.
Bandwidth: Colloquially, the amount of network capacity available for a connection.
Blocking: A means of disallowing access to Internet content and services by restricting access at the corporate gateway.
Cyberslacking: The process of using the Internet to waste time during a workday, similar to how an employee might spend time in a colleague’s office or on the telephone.
Logging: Creating a record of all employee Internet usage.
OSI Layer 4: The transport layer of a network connection, which provides service differentiation and connection management. From the open systems interconnect model.
OSI Layer 7: The application layer of a network connection. It describes how applications work with the network operating system. From the open systems interconnect model.