INTRODUCTION
Multicast technology is one-to-many communication, oppositely from the usual one-to-one (unicast) communication, which provides an efficient solution to create multiparty collaborative software by delivering the data flows on an appropriate distribution tree. The root of the distribution tree is the sender and its leaves are the receivers. Many Internet applications, such as distributed simulation, remote education, and videoconference require the underlayer network to support multicast communication.
The main problem of the multicasting is, however, how to construct and maintain the path, called delivery or distribution tree. There are solutions in different levels of the protocol stack, including datalink-layer, network-layer, and application-layer. Only the second and the third level multicast have practical importance; therefore we focus on these in the following.
The network-layer multicast is based on the Internet protocol (IP), which is why this kind of multicasting is called IP multicast. This technology is bandwidth conserving and reduces traffic by simultaneously disseminating a single stream of information to potentially thousands of corporate recipients. Multicast packets are replicated in the network at the point where paths are multiplied by multicast routing protocols, resulting in the most efficient delivery of data to multiple receivers. The main advantage of the multicasting is the smaller bandwidth usage than a normal unicast-based transmission.
The application-layer multicast (ALM) uses a different approach. In this technology, the multiplying nodes are host and the transmission is based on unicast. However, even the application-layer multicast has serious advantages over the pure unicast transmission, since in case of the traditional unicast, the sender has to create as many parallel data streams as receivers joined to the session. However, in case of ALM the sender has to serve a limited number of data streams, since the other group members as nodes also act as multiplication points. In such a way, they create a distribution tree.
BACKGROUND
The traditional unicast require the source to send more than one copy of the data, since there are point-to-point connections between the sender and each of the receivers. Even low-bandwidth applications can benefit from using multicast when there are thousands of receivers. High-bandwidth applications, such as video streaming, may require a large portion of the available network bandwidth for a single stream. In these applications, multicast is the only way to send to more than one receiver simultaneously.
The current Internet applications manage a large and widely distributed set of users, have multiple data streams that vary in content and media type, and make use of multiple unicast and multicast streams in a single session. Examples of these distributed, interactive applications include corporate communications, distance learning, video conferencing, stock quotes, software distribution, network news, collaborative visualization, distributed interactive simulations, and multiplayer games.
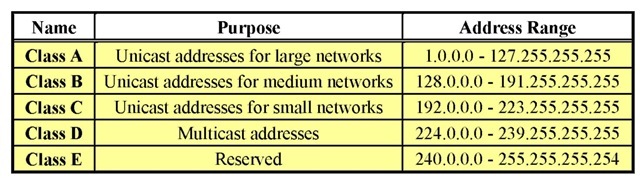
Table 1. The IP address ranges
THE IP MULTICAST APPROACH
Special IP-addresses are used in the IP-multicast, which do not belong to certain hosts, but define multicast channels. Table 1 presents the address ranges of the IP address space. The Class A, B and C are used for the traditional unicast communication; the Class D addresses are applicable for multicasting.
The first model of the IP-multicasting was proposed by Steve Deering in 1988 in his PhD dissertation, and its first standard was published in the RFC 1112 (Deering, 1989). The most important idea in Deering’s model for the multicasting is the so-called multicast group concept. Table 2 summarizes the main factors of this concept.
THE IP MULTICAST ROUTING
The first issue of multicast delivery is the communication between the host and the local router. The host does not have routing functionality; it uses a special signaling protocol, the Internet Group Management Protocol (IGMP), to let the local router know that the host became interested in the traffic of a certain multicast group.
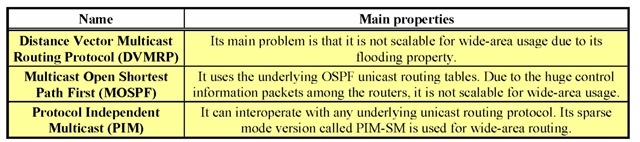
The multicast delivery in the inter-router area is based on the multicast-enable routers, which have multicast routing protocols in their protocol stack. The multicast routing protocols differ from each other according to the underlying unicast routing protocols used. Table 3 presents the most popular multicast routing protocols and their most important properties (Hosszu, 2001).
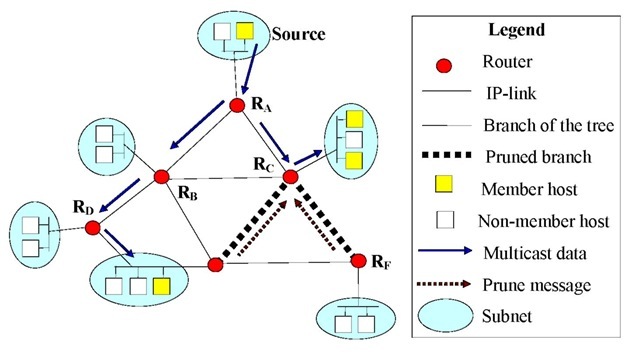
An important step in creating the delivery tree is to discover all the routers interested in the given multicast session. In case ofthe DVMRP (Waitzman, 1988), MOSPF (Moy, 1994) and dense mode version of the PIM multicast routing protocols, the routers periodically flood the whole network with a multicast data packet, forwarding it to every router (Adams et al., 2003). Routers not interested in that session send a prune message back to the source of the packet and so the following packets will not be forwarded to these. The flooding step generates a huge amount of unnecessary packets, which is acceptable in dense mode situation, where the majority of the routers are interested in a multicast delivery. This routing method is called flood-and-prune model, and its operation is demonstrated in Figure 1.
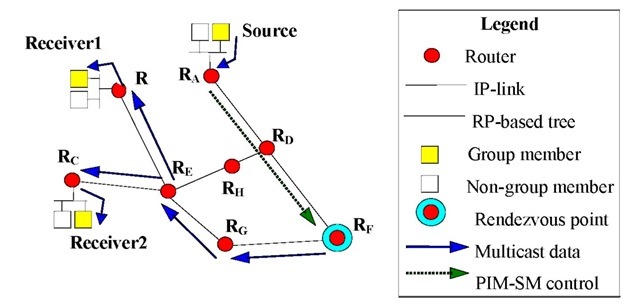
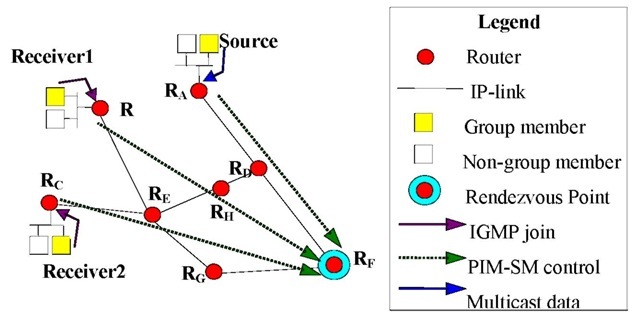
In the sparse mode case, where only a small fraction of the routers are interested in a multicast session, the periodically executed flooding means an unacceptable load in the inter-routing area. In such a situation that multicast routing protocols can efficiently operate, rendezvous points (RP) are used to join to a multicast session and in such a way that the periodical flooding phase is avoided. In case of the PIM-SM routing protocol (Fenner et al., 2004), if a host wants to send multicast traffic, it will send the data packets to its local router, and then it forwards the data to the RP, which is now a designated remote router. The other host interested in that multicast traffic will send an IGMP join message to its local router, in order to become a receiver. Then the local router will send a PIM-SM joint message to the RP. Figure 2 shows this mechanism, where two receivers join to the multicast session.
After completing the join phase, the RP continuously forwards the multicast traffic toward the local router of the receiver. The data from the source to the RP is an encapsulated unicast PIM-SM control message. Figure 3 demonstrates this phase.
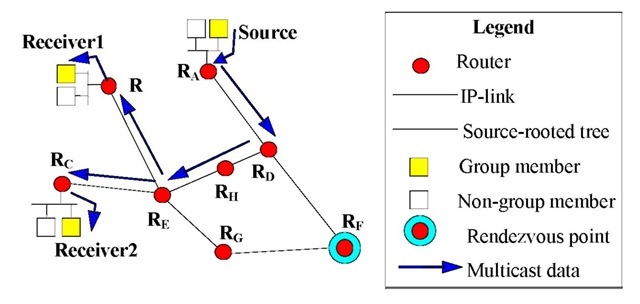
The root of such a delivery tree is the RP. A more optimized tree can be obtained, if the routers realize that a shorter path can be created between the source and the receiver. In this case the PIM-SM routers can switch over from the RP-rooted tree to the source-rooted tree. Figure 4 shows the created source-rooted tree.
Besides constructing the tree, its stability is also an important problem, since the routing protocol must upgrade at least a part of the tree whenever a member joins or leaves the multicast session (Van Mieghem & Janic,2002).
Another serious routing problem of the IP-multicast is the inter-AS (autonomous system) multicast routing, since transmitting multicast traffic is not easy among the peering ASs. To overcome this limitation, different wide-area protocols are developed. The current practice is the usage of the protocol set MBGP/PIM-SM/MSDP; however, it has scalability problems, since it uses flooding to inform the receivers in the remote ASs about a local multicast source (Fenner & Meyer, 2003). The long-term solution may be MASC/MBGP/BGMP stack, which constructs a multicast tree from the ASs and avoids the flooding among them (Rajvaidya & Almeroth, 2003).
Table 2. Components of the multicast group concept
IP-style semantics: Similarly to the traditional (unicast) IP communication, a source can send data at any time; for this it does not have to join to the group of hosts.
Open groups: The source does not have to know the members of the groups for sending data and the receivers (members of the group) do not have to know the source.
Variable groups: The hosts can create, join to or leave any group at any time. The communication does not need any control center to coordinate the activity of the hosts.
Table 3. The widely used multicast routing protocols
From the viewpoint of the market-oriented applications, the Deering’s multicast model had to modify in order to be less vulnerable. For instance, a malicious sender can send noisy data to a multicast channel, which is used by other users. In order to avoid such an unwilling situation, the multicast concepts called source-specific multicast (SSM) were developed, where the host specifies not only the multicast group (class D) address sending an IGMP join message to the local router, but also the set of sources, from which it accepts multicast data (Almeroth et al., 2001). In this network the routers can also distinguish data streams having the same multicast address but originating from different sources, if they use SSM routing protocol such as the source-specific version of the PIM-SM, called PIM-SSM (Meyer et al., 2004).
THE CONNECTIONLESS AND CONNECTION ORIENTED TRANSMISSIONS
There are two basic types of communication; one is called connectionless, where the sender starts to send the data packets without any previous negotiation phase with the receiver. Such a method is used in the Internet, where the sender host or router forwards the IP packets without any delivery guarantees. The IP-multicast is similar to the conventional IP unicast communication from the point of view that quality of data transmission is non-reliable, the so-called best-effort. It means that there is not any guarantee for any parameter of the transmission, such as the delay, the error-free delivery, and so forth. Its reason is the connectionless property of the Internet protocol, where there is not any logical connection among the communicating entities in the network level. When a router sends data, it has no any knowledge if the other router receives that data properly or not.
Figure 1. Operation of a flood-and-prune multicast routing algorithm
Figure 2. The joining phase in the PIM-SM operation
The other communication form is connection oriented, where the sender and the receiver negotiate with some communication parameters such as the sending rate. An example of the connection oriented data transfer is the Transmission Control Protocol (TCP) that is used in the unicast to get reliable delivery. However, the TCP is not usable for multicasting, since the TCP receiver client acknowledges every packet, and in the case of a large number of receivers, this could cause serious congestion at the network link of the multicast source. That is why the multicast applications use the User Datagram Protocol (UDP) for transmission, which has no reliable mechanism.
METHODS TO INCREASE THE RELIABILITY OF THE MULTICAST
Since most of the multicast applications are media-related software, for example, media conference, voice distribution, shared whiteboard, or various collaborative media tools, they need more reliability than the best-effort delivery. In order to increase the reliability of multicast applications, additional multicast transport protocols are used to achieve the required level (Whetten & Taskale, 2000). Such a protocol is the NORM: NACK-Oriented Reliable Multicast Protocol (Adamson et al., 2004).
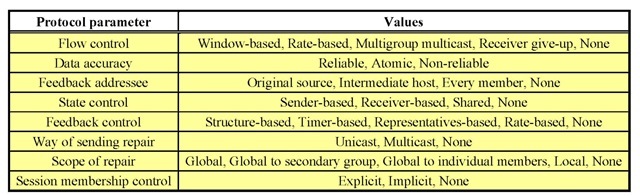
The multicast transport protocols have many different property attributes of the data delivery. These attributes can be represented by the protocol parameters. Each protocol parameter describes different reliability mechanisms for the same delivery attribute. Such a protocol parameter is, for instance, the repair method, which can get the values such as “retransmission,” “forward-error correction,” “interleaving,” or different ways of the “local receiver-based repairs”. Another parameter is the acknowledgement type, the possible values of which may be “tree-based,” “ring-based” or a “simple direct form”.
Figure 3. The data transmission among the hosts and the PIM-SM routers
Figure 4. The data transmission through the source-rooted tree
The various applications have different reliability requirements, and therefore these protocol parameters should be optimized in order to create the multicast transport protocol best suited for a given application. However, applying any appropriate mathematical optimization method, at the selection of the protocol parameters mentioned previously, a linearly independent (in other words, orthogonal) set of parameters must be applied. To do this a hyperspace of the parameters is created where all transport protocol corresponds to one point of this space. The optimization procedure means to find the most suitable point in this space to provide the best performances of multicast. The possible values of protocol parameters (which are the types of various mechanisms as the components of these) are the realizations of the protocol functionalities. A quasi-orthogonal subset of the protocol parameters and their possible values are presented in Table 4. These parameters represent the well-known reliable mechanisms of the transport protocols.
To carry out a correct optimization procedure on the appropriately selected protocol parameters, a well usable simulation program should be applied in order to obtain statistically confident results for multicast data transfer. Using an appropriate simulator, the optimized transport protocol can be synthesized for a given media application, satisfying the requirements. That means that by a mathematical method an optimal point in the hyperspace of the protocol parameters can be found.
THE APPLICATION-LAYER MULTICAST TECHNOLOGY
The application-layer multicast (ALM) is also called host-multicast, since the nodes are responsible for the multicast delivery, not the routers. The main difference between the host-multicast and the IP-multicast is that in the case of the ALM, the hosts use unicast between them and the multiplication points of the tree are the hosts themselves, not the routers, as in the IP-multicast (Banerjee et al., 2002; Castro, 2002; Zhang et al., 2002). Table 5 compares the properties of the host-multicast and the IP-multicast.
Table 4. The selected set of the protocol parameters
ALM is a new approach to providing multicast services to group applications. In this peer-to-peer (P2P) architecture, members organize themselves into an overlay topology for data delivery that adapts to the changing network conditions and group dynamics. P2P systems are distributed virtual networks that operate without centralized control. To find a particular piece of data within the network, P2P systems explicitly or implicitly provide a lookup mechanism that matches a given string (called a key) to one or more network nodes responsible for the value associated with that key.
Some of the ALM schemes can take advantage of IP-multicast support where available. However, such additional IP-layer capabilities are not essential for these protocols, and therefore they can be easily deployed in the Internet today. Current Internet P2P applications typically provide lookup functions using time-to-live (TTL) scope controlled flooding procedures. With this approach, the querying node wraps the query in a single message and sends it to all known neighbors. The neighbors check these to see if they are able to reply to the query by matching it to keys in their internal database. If they find a match, they send a response; otherwise, they forward the query to their own neighbors and increase the message’s hop count. If the hop count becomes higher than the TTL limit, the forwarding will be cancelled. The TTL value thus determines a boundary for the query that controls its propagation.
THE THEMATIC MULTICAST CONCEPT (TMC)
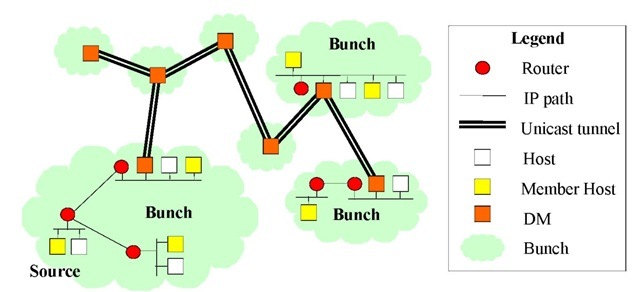
As an example of the current searching works in the field of ALM, a novel concept of modeling relative density of members is the bunched mode. The bunched mode means a typical multicast scenario where many interested hosts are in certain institutes relatively far from each other. The members of a multicast group are locally in dense mode; however, these spots are far from each other, with their situation globally being similar to the sparse mode. This situation is typical when the collaborative media application has a special topic. That is why this model of communication is called thematic multicast concept (TMC). A typical TMC scenario is shown in Figure 5.
The group-member hosts in a bunch locally elect the designated members (DM). The DM calculates the shortest unicast IP tunnels among them. They exchange their IP addresses and shortest unicast paths among them. In such a way, all of them know all possible shortest unicast paths and calculate the same topology of the inter-bunch IP tunnels. This application-level routing mechanism, called shortest tunnel first (STF), is similar to the MOSPF routing in the network level. The MOSPF routers exchange the link-state information, but in the case of STF, the DMs exchange the path information to every other one, since there are UDP/IP paths to every other DM.
FUTURE TRENDS
Due to the increasing bandwidth, the users send more and more media content through the Internet. The collaborative applications also have strong demands. Therefore the multicast as a communication model will be used in the future. The choice between the IP multicast and the application-layer multicast, however, remains an open question. The most important advantage of the IP multicast is the reliable operation of the intermediate nodes, oppositely to the easy deployment of the ALM. The networking applications, which have a limited number of users, will prefer the ALM as multicasting technology; however, the stable, long-term applications with a number of users (e.g., media streaming) will prefer the IP multicast due to its more reliable nature. Another side of the problem is that independently from the usage rate of the IP multicast, its sophisticated routing and transporting methods are adapted in the ALM, too.
Table 5. Comparing the properties of the host- and the IP-multicast
Deployment cost: The IP-multicast requires additional knowledge in the routers to the basic unicast communication and extra work from the administrators of the routers; the ALM needs the traditional unicast IP infrastructure, only.
Flexibility: The host- and the IP-multicast are flexible, and it is easy to change the topology of the multicast tree.
Speed of delivery: The ALM theoretically cannot be more optimal than the IP-multicast tree, in such a way that the delivery of the ALM has higher delay than the IP-multicast. Robustness: In case of the ALM, the hosts are responsible to maintain the tree; in case of the IP-multicast, the routers define the tree. Since the routers operate safely, non-stop, but the user can switch off a host anytime, in such a way the IP-multicast is more robust.
Figure 5. A typical TMC scenario
In the future, new applications as well as methods will emerge in the field of multicasting in order to more efficiently use the existing network.
CONCLUSION
The emerging media applications use multicast technology to efficiently deliver large media data to the receivers. The fundamentals of the network-level IP-multicast and the application-level host-multicast are presented. The main fields of research are the wide-area routing and the reliable multicast transport protocols in the IP-multicast, and a novel application-level routing protocol and communication concept in the host-multicast. The advantages and the drawbacks of the two basic multicast technologies are compared. Selecting the most beneficial technology to apply depends on the requirements of the actual media application.
KEY TERMS
ALM (Application-Layer Multicast): A novel multicast technology that does not require any additional protocol in the network routers, since it uses the traditional unicast IP transmission.
Application-Level Multicast: Alternative name of the application-layer multicast.
AS (Autonomous System): A network where the main routers are in common administration. The Internet is composed of peering ASs.
Host-Multicast: Alternative name of the ALM.
IETF (Internet Engineering Task Force): A voluntary association for developing Internet standards.
IP-Multicast: Network-level multicast technology, which uses the special Class-D IP-address range. It requires multicast routing protocols in the network routers.
Multicast Routing Protocol: In order to forward the multicast packets, the routers have to create multicast routing tables using multicast routing protocols.
Multicast Transport Protocol: To improve the reliability of the multicast delivery, special transport protocols are used in addition to the widely used unreliable UDP.
Reliability: The improved quality of data transmission; different types of reliability exist, including data accuracy or real-time delivery.
RFC (Request for Comments): The IETF publish them as de facto standards of the Internet.
TTL (Time-to-Live): A field in the IP packet header. Its value is the allowed hop-count, the number of routers, which can forward the packet before delivery or dropping out.
Unicast: The one-to-one communication way, where only one host transfers data with another host. In the traditional IP the unicast is applied.
Deployment Cost: The IP-multicast requires additional knowledge in the routers to the basic unicast communication and extra work from the administrators of the routers; the ALM needs the traditional unicast IP infrastructure, only.
Flexibility: The host- and the IP-multicast are flexible, and it is easy to change the topology of the multicast tree.
Speed of Delivery: The ALM theoretically cannot be more optimal than the IP-multicast tree, in such a way that the delivery of the ALM has higher delay than the IP-multicast.
Robustness: In case of the ALM, the hosts are responsible to maintain the tree; in case of the IP-multicast, the routers define the tree. Since the routers operate safely, non-stop, but the user can switch off a host anytime, in such a way the IP-multicast is more robust.
IP-Style Semantics: Similarly to the traditional (unicast) IP communication, a source can send data at any time; for this it does not have to join to the group of hosts.
Open Groups: The source does not have to know the members of the groups for sending data and the receivers (members of the group) do not have to know the source.
Variable Groups: The hosts can create,join to or leave any group at any time. The communication does not need any control center to coordinate the activity of the hosts.