Introduction
Forensic engineering is the application of engineering knowledge and principles in a legal context. While many practitioners will be involved in the investigation of engineering failures and the subsequent litigation, this article will discuss their contribution to other types of legal investigation. Forensic engineering covers the full gamut of engineering practise, from the investigation of a road traffic incident by a mechanical engineer to the recovery of data from a computer system by an electronic engineer. It is as broad a topic in its own right as forensic science.
The boundary between science and engineering is diffuse, although most people would have no difficulty in distinguishing between an engineer who designs car engines and the scientist who investigates flame propagation in compressed gases, despite the fact that their work might well be linked. The dictionary is little help; it defines engineering as:
The application of science for directly useful purposes.
The distinction becomes even more blurred when we try to differentiate between that most applied of sciences, forensic science, and forensic engineering. Is the practitioner investigating the behavior of skidding vehicles a physicist or a mechanical engineer? In reality we are discussing labels rather than content, and the crucial similarity is the application of technical and scientific knowledge to legal problems.
This article takes a broad look at how engineering disciplines are able to help the legal process, both criminal and civil. A number of forensic engineering topics have been dealt with in depth elsewhere in this topic and those articles provide an excellent way to start deepening your knowledge of particular areas.
Accident Investigation
The specialist role of the forensic engineer is most obvious in the investigation of accidents. These may be accidents, if that is the right word, involving any mode of transport; the workplace or machinery. The word ‘accident’ is unfortunate, as it suggests that the incident was unavoidable and no one’s fault; in many, if not all, cases the investigation will show that the incident was both avoidable and the result of the actions of one or more of the parties. In any event the investigator will have to combine the results of his or her own observations, measurements and tests with information from witnesses, automatic recording equipment, television monitors and the known behavior and performance of the vehicle, equipment or materials involved. For example, following a road traffic accident the forensic engineers may have information from the scene, witnesses, a tachograph (a form of recording speedometer) and traffic management cameras, plus the results of their own observations and measurements to consider. They must combine these into a coherent whole that gives proper weight to all the evidence and which ignores or distorts none of it.
The use of the word ‘accident’ to cover crashes and other transport disasters is interesting in itself. It normally implies an unexpected or unintended event. A large number of transport accidents, particularly on the roads, are the entirely predictable outcome of deliberately chosen behavior. There is nothing accidental about them at all and the trend towards referring to them as incidents or crashes is welcome. The phrase ‘dangerous occurrence’, which comes from health and safety regulations, is particularly apposite.
Engineering can help to provide answers in the investigation of these incidents in a number of ways; three of these are discussed in this section.
Mechanical engineering
A critical component in the investigation of an accident or other dangerous occurrence is the behavior of the systems involved. As a result, much time is spent in collecting and examining wreckage. Often great efforts will be made to recover wreckage from locations as inaccessible as the seabed (Fig. 1), or to collect and reassemble small pieces spread over a large area, as happens when an aircraft breaks up in the air. The interaction between a vehicle and terrain is another major source of information. As with all other scene examination, detailed observations need to be made and recorded. The initial investigation must be conducted with no preconceptions about what is important and what is not.
Examination of the wreckage can tell the forensic engineer the attitude of the vehicle as it crashed. For example, did the car strike the wall frontwards or backwards; or was the nose of the aircraft pitched up or down as it struck an obstacle? Other witness marks may indicate that parts of an aircraft broke off before the final impact, enabling the investigator to begin to establish a sequence of events. The nature and location of damage, coupled with contact traces such as smears of paint, will enable the investigator to deduce how two cars may have collided. The nature and extent of the damage to the vehicle is a function of the severity of the impact and it is possible to work backwards from the damage to an estimate of impact speed, or at least speed change on impact.
Marks left as the vehicle interacts with the terrain can provide a whole range of information (Fig. 2):
• Skid and scuff marks left by a car as it goes out of control can not only provide information about the movement of the vehicle but also enable its speed to be estimated.
• The gouges left by an aeroplane propeller can indicate that the engine was still under power as the plane struck the ground.
• Marks caused by the flanges of a wheel on the side or head of a rail will show where a train started to derail.
Successful investigation requires the forensic engineer to combine all sources of information to produce a comprehensive reconstruction of events. Thus, while impact damage alone does not allow the investigator to calculate the impact speed of a car, couple this with evidence about the post-impact movements of the vehicle obtained from tire marks and reliable information about impact speed may be obtained.

Figure 1 The fishing vessel Pescado was recovered from the sea off the south west coast of England to assist the Marine Accident Investigation Branch enquiry into the loss of the vessel and crew. Marine Accident Report 1/98 (1998), London DETR.
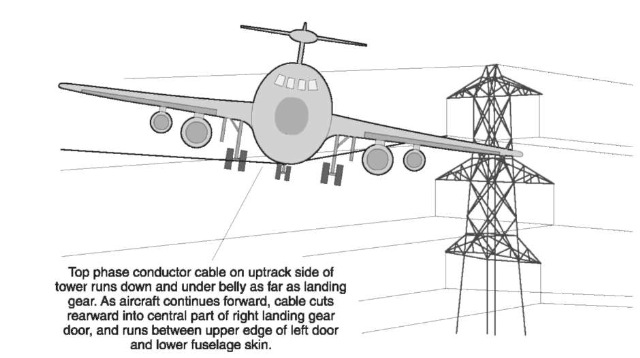
Figure 2 Witness marks on the underside of a Boeing 737 enabled investigators to deduce its attitude as it struck overhead electricity cables near Coventry, England on 21 December 1994. Air Accident Report 1/96 (1996). London: HMSO.
Defects and failures
Catastrophic failure of systems and components can precipitate an accident or other dangerous occurrence. Allegations of failure may be suggested as an explanation for an incident and it is critical that the forensic engineer is able to distinguish between post-accident failure and accident-induced damage. Road traffic incidents are a good example of where one or other party has claimed that a component failure was the cause – for example, a tire blowout – where careful examination has shown that the failure was a consequence and not a cause of the incident.
The type of failure that can precipitate an incident will depend on the type of transport. Thus, sudden engine failure is rarely a problem for a road vehicle but can of itself cause an aircraft to crash. As a result, considerable effort will be made to recover the engines and associated components from a crashed aircraft and subject them to meticulous examination. Fatigue failure of components is still causing aircraft accidents, and suggestion that fatigue may have played a part in an incident will result in a detailed review of the history of that component.
The system of air worthiness certificates and registration makes unauthorized modifications to aircraft unusual, if not impossible. Unfortunately, they contribute to a number of road traffic incidents every year. Modifications to the springs and dampers which cause unanticipated changes to the ride and handling of the car is one common form that can prevent the driver retaining control of the vehicle. Investigation of this kind of incident should extend beyond examination of the altered components to a practical investigation of their effect on the handling of the vehicle. Such tests must be conducted off the public road in an area where there is plenty of space for the driver to regain control of the vehicle.
Signaling and control systems
In an increasingly crowded world all modes of transport are controlled in some way. Controls can be as simple as a set of rules, such as are contained in national highway or driving codes. In controlled airspace, however, all movements of aircraft are monitored and directed by the air traffic controllers. Aircraft movements are controlled by a complex mix of verbal instructions and electronic surveillance. Signals are an alternative way of controlling movements; they may be as simple as a fixed STOP sign that instructs a motorist to stop at a junction, or as complex as the systems on some railways, which can detect and control the movements of trains.
Without reliable signaling and control the volume of traffic that can pass safely through the busiest parts of a transport network would be severely curtailed. Vehicle operators come to rely on the information the signaling and control system provides. Failure of the system in any way can have catastrophic effects. After any serious incident, part of the subsequent inquiry will be directed to the functioning of the signaling and control system. This can be a complex task, particularly when the system can alter and adapt to traffic conditions. For example, the automatic traffic signals controlling a complex road junction will have phases that are only activated when a particular set of circumstances apply. The engineer investigating the system needs to appreciate this and have sufficient reliable information to be able to trace the particular set of circumstances that obtained at the time of the incident.
Like many others, the weak link in signaling and control systems is all too often the humans operating it. Human failures have compromised the safety features built into railway signaling systems many times over the years, and even the highly structured environment of air traffic control does not eliminate human failing completely. In fact, much of the complexity of signaling and control systems is an attempt to eliminate scope for human failing.
Animation and simulation
Simulation is the use of a theoretical model of a system to reconstruct (or predict) events. Simulation techniques have been used in the design and development of all forms of transport but it is only with the advent of powerful personal computers that it has been a practical proposition to use simulation for the investigation of road traffic incidents. Of course, the very sophisticated flight simulators used for pilot training have been used to explore the behavior of an aircraft in an unusual flight regime as an aid to aircraft accident investigation for many years.
While simulation programs can produce purely numerical data, their great advantage is that this data can be used to generate an animated reconstruction of events. The use of animated output makes the result of the simulation much more accessible to nonspecialists and can be used to demonstrate the reconstructed events to a judge or jury. Animation is such a powerful tool for explaining a theory that the engineer using it must be careful to ensure that the medium does not become the message. Often a simple wire frame or polygonal model will suffice and has the advantage that the audience will never lose sight of the fact that they are watching a reconstruction. The other important fact that must never be overlooked is that the critical component of any animation is the underlying simulation model that has been used to generate it. Characters in animated cartoons regularly do physically impossible things; here the underlying model is not a reliable representation of reality.
Practical modeling systems are a compromise brought about by the limitations of the available computing power and the amount of data that can be collected. Thus CRASH III, which in one of several personal computer implementations is among the most widely used programs for modeling the behavior of colliding cars ignores inter-vehicle friction completely. This program assumes that the contact points on the two vehicles achieve a common velocity; it is quite unable to handle sideswipe impacts.
Full simulation of the behavior of motor vehicles requires a three-dimensional model with 16 degrees of freedom. This requires a great deal of computing power, and frequently more knowledge of events than can be obtained. An all encompassing simulation would require information about tire cornering characteristics, tire-road friction, steer angle, load, driving/braking forces, suspension and damping properties for each wheel – over 30 different parameters. PCCRASH, a somewhat simpler model, can be used to good effect in many cases. This will allow for lateral, longitudinal and yaw displacement and can allow for the effect of pitch and roll on dynamic weight distribution. Good results can be obtained using a simplified data set; thus, steer angle and tire-road friction can be entered for each wheel but damping forces and tire cornering characteristics can be ignored.
One of the most challenging simulation problems in transport accidents is modeling the behavior of the human body. Complex models of the human body have been used to reconstruct the behavior of victims in a crash. Different human simulation models were used to investigate the behavior of victims of a crash involving a Boeing 737 in central England in 1989 and a railway accident in London in 1991. The analysis of the latter, which involved a rush-hour train at a terminal station, also had some interesting human factors. Standing passengers were more likely to be seriously injured than those still seated, and passengers in the rush hour start moving towards the doors as the train pulls into the station, leaving them more vulnerable if it then collides with the buffers.
Ergonomics
Whether they are called accidents, incidents or dangerous occurrences, any investigator soon becomes aware of the importance of the human beings in the system. Around 90% of all road traffic incidents are the result of human failing in some way. Recognition that it was not enough to assign the cause of an incident to human error was first apparent in air accident investigation. One of the roots from which ergonomics eventually grew was research into the reasons for pilot error and what could be done to prevent it. However, concern with the effects of human failure and how it could be prevented was being expressed by the railway accident investigators in the nineteenth century. Simple reminders to signalmen not to change the signals, such as the mandatory presence of a member of a delayed locomotive’s crew in the cabin, were introduced before track circuits and signal interlocking prevented it happening.
This concern for why mistakes are made is still a common feature of enquiries into rail and air accidents. When a Royal Air Force war plane and a helicopter collided in clear weather, the accident report included a discussion of why ‘see and avoid’ was not necessarily a sound basis for collision prevention in conflicts with fast jet aircraft. One, all too common, cause of rail accidents in the United Kingdom is a signal passed at danger. The interesting question, of course, is why they happen:
• Are there problems with brakes on the train or do modern disk brakes require different techniques than the older clasp brakes?
• Are the signals faulty in some way or do the drivers fail to see that they are at danger until too late?
In the latter case, expectation plays a part in the driver’s failure to react. Frequently he or she will have been traveling under amber warning signals for some time and fails to register that the latest signal is now showing red for danger. The Railway Inspectorate, who investigate rail accidents in the United Kingdom, have returned to this subject several times and made a series of recommendations to minimize the impact of human factors on rail accidents.
The human component in a safety-critical engineering system is often the weak link. While human failure is an explanation for an incident, it is not an adequate diagnosis. If the event is not to be repeated, the forensic engineer needs to understand why the failure occurred and what can be done to prevent a repetition. If humans do not learn from experience they are destined to repeat their mistakes.
Electronic Engineering
The all pervasive nature of information technology and computers means that electronic engineers will become involved in all types of investigation. The hardware on which modern signaling and control systems rely will be based on microprocessors and stored programs, and the skills of the software or electronic engineer will be as important as those of the mechanical engineer when investigating an incident involving such systems. Electronic and computer engineers have a particular contribution to make to the investigation when computers are involved or where electronic images are a potential source of evidence.
Computers
The advances in computer systems and telecommunications technologies have created increased opportunities for criminals to conduct their business. Such activities are often referred to as ‘computer crimes’ and encompass the three ways in which computers can be used for criminal purposes:
• When the computer may be the target of a crime. The criminal’s aim is to cause damage to a computer system and its data.
• When the computer may be an ‘instrument’ used during an offence. For example, a computer can be used to carry out traditional crimes, such as fraud or theft, or may be used to produce illegal copies of credit cards while others may be used in the illegal cloning of mobile phones.
• When the computer is incidental to some other offence but is significant because it may be found during a scene examination and contain evidence of that, or other, criminal activity, and therefore has an ‘intelligence’ value.
The popular image of the computer criminal is of someone who breaks or ‘hacks’ into a computer system remotely and alters it to his or her advantage. In practice, however, a great many of these crimes are committed by people with legitimate access to the system.
Every examination of computers will be different because the computer media, its structure, the purpose of the examination, the elements of the crime and the type of information are different for each investigation. However, successful investigations require a good understanding of ‘target’ systems and the security measures in place, such as:
• How access to the system(s) is controlled:
-whether physically by use of barriers or locked doors, etc.
-logically by the use of passwords and user IDs -a combination of these.
• What sort of audit trails are maintained.
• If different levels of access are established:
-what rights are associated with these
- who controls access
- who might be able to change access levels.
In theory, with this type of inquiry, access to the computer system and associated records will be provided by the owner or system manager. In practice, establishing who had access to the system at any particularly important time, what their access rights were and how these may have been exceeded will require a great deal of careful research and effort. Still one of the most common, and simplest, ways of gaining unauthorized access to computer systems is by obtaining the user ID and password of a colleague. This does not make the investigation process any easier.
While many aspects of these computer crime investigations will revolve around determining access levels and opportunities available to individuals, an entirely different set of skills is required in order to conduct a forensic examination of the computer systems themselves. Examiners will need to be prepared to examine anything from a personal organizer to a highly sophisticated and networked personal computer. In addition to being able to handle this range of hardware, they will also need to understand the particular operating systems in use on these systems and a variety of software packages that can be used to store and manipulate data. Knowledge of security aspects built into these products and how these can be circumvented is also essential to allow a comprehensive examination to be carried out.
Data held on a computer system are no different to information or text contained on a document. For this reason evidence that is to be based on a computer or on computer media is subject to the same rules and laws that apply to the documentary evidence. The doctrine of documentary evidence may be explained thus: ‘The onus is on the prosecution to show to the Court that the evidence produced is no more or less than when it was first taken into the possession of police.’
When faced with a computer system that may contain vital information, the investigator should think carefully before doing anything that might affect the integrity of the data on the system and compromise the subsequent forensic examination process. Operating systems and other software frequently alter and add to the contents of the computer systems storage space. This is an automatic process without the user necessarily being aware that the data have been changed. Ideally, therefore, a copy should be made of the entire target computer system on to media that can be retained for examination and subsequent use in court. A number of recognized copying devices are available for this purpose. As always, a full record of all work carried out during the examination must be maintained.
The protection of individual files on computer systems can be achieved in a number of ways. At its simplest, the owner of the file relies on the overall security of the system; however, once access has been obtained the file can be easily read. At the other extreme, a wide range of sophisticated encryption software is available which can be used to protect the information. In certain circumstances some routines can monitor the way in which the computer system is started and, if it detects any differences, will disable the system or even delete its contents. It should be noted that deletion of files can, in some circumstances, be reversed; however, recovering lost data is more difficult than protecting or preserving it in the first place.
Digital imaging
Digital imaging and the processing of digital images can be used to address a number of problems. As digital images do not require development or printing they are available immediately. At its simplest, this means that the photographer can modify the conditions to produce a satisfactory image before leaving the location of the incident. Moreover, a digital image of a fingermark or shoeprint can be sent electronically from the scene to the laboratory for comparison and identification before the inquiry team leave the scene of the incident.
One of the great advantages of a digital image is the ease with which it can be manipulated to improve the clarity. While this might involve something like contrast enhancement, which can also be done photographically, techniques such as deblurring, sharpening or background subtraction require manipulation of a digital image. The ease with which a digital image may be modified brings its own dangers. It is vital that the original image is retained unaltered; all changes should be made to a copy and a complete audit trail of everything done maintained. Parliament in the United Kingdom was sufficiently concerned about the scope for unscrupulous manipulation of digital images that a select committee was formed to address the whole issue of digital images as evidence.
Video cameras are widely used to monitor public areas for both crime prevention and traffic control purposes. Inevitably this means that criminal activity will be recorded on video tape. The quality of these images and the viewpoint from which they are taken make identification of suspects or what they are carrying difficult. Careful enhancement of the image may allow a person or his or her property to be identified.
The effects of perspective and parallax can give a false impression of the height or build of someone caught on these cameras. Geometric methods can be applied to the digital image to extract length and height information without a detailed knowledge of the optical characteristics of the camera used. Simple rectification programs can be used to prepare complete plans of a scene from a digital image, although, for these to work, at least one measurement in the photographed scene is required. If several images are available a three-dimensional representation of the scene can be produced. By using these techniques the movement of an object through the camera’s field of view can be followed. If the time lapse between successive images is known, speed can be determined, which has obvious applications when investigating road traffic incidents.
The widespread use of surveillance cameras and the increasing power and sophistication of digital imaging techniques means that a great deal of evidential material will become available to the criminal justice system. Solving the problems associated with facial recognition will become essential if this mass of material is to be evaluated effectively. As has already been demonstrated with speed enforcement cameras, the resulting information has to be handled with sensitivity if the ‘Big Brother’ image of video surveillance is not to swamp its power as a crime prevention, reduction and investigation tool.
Fire Engineering
The investigation of fires is dealt with in detail elsewhere but it as an area of forensic engineering where an interdisplinary approach will pay dividends. Understanding the events that have given to rise to a fire, from an examination of the burnt-out remains of a building or vehicle, may involve chemists, physicists and engineers. Careful investigation of the fire scene is an essential part of the process, and the successful fire investigator will combine the practical investigative and problem-solving skills of an engineer with the ability to synthesize information from a wide variety of sources.
The basic process in fire investigation is to establish the point at which the fire originated and then deduce from the available evidence how the fire started. Before this process can begin, the investigator needs to gain safe access to the scene. Since the fire can disrupt both the structural stability of a building and its electrical supply, and produce noxious combustion products, a pause for reflection to decide upon a safe approach before commencing work should be standard procedure. The process of investigation to determine the origin and cause of the fire can then start and be brought safely to a successful conclusion.
Where the development and spread of the fire needs to be established, computer simulation and model tests can be used. Both of these approaches were used to assist in the investigation of a very serious fire at King’s Cross underground station, London, where they: ‘first drew attention to an important and unsuspected phenomenon in the form of the trench effect.’ (Fig. 3).
Conclusion
Forensic engineering has applications over a wide and increasing range of criminal and civil investigations; for example, the pervasive spread of computers and surveillance cameras means that electronic, computer and software engineering will become an important part of the investigation of many serious crimes. The skills and techniques that are used to investigate transport accidents can be of value in a range of investigations, not only those where a motor vehicle has been used as a weapon in an assault. Falls, nonaccidental injuries and stabbing are all areas in which forensic engineers have contributed to an investigation.

Figure 3 Fire tests on scale models of the escalator troughs at Kings Cross were conducted by the Health and Safety Executive at Buxton to demonstrate how the flames lay low in the trough with a jet of flame at the top – the ‘trench effect’. Investigation into the Kings Cross Underground Fire, Desmond Fennell QC Cmm 499 HMSO London (1988).
