Debug Commands
To debug the H-REAP disassociation and joins on the controller, use the standard
LWAPP/CAPWAP debugs outlined in next topic.
Following are the main debugs:
■ debug capwap/lwapp events
■ debug capwap/lwapp packet
The debugs to view the more advanced features of H-REAP are as follows:
■ debug hreap aaa {event I error} {enable I disable}: Enables or disables debugging of H-REAP backup RADIUS server events or errors.
■ debug hreap cckm {enable I disable}: Enables or disables debugging of H-REAP CCKM.
■ debug hreap group {enable I disable}: Enables or disables debugging of H-REAP groups.
■ debug pem state {enable I disable}: Enables or disables debugging of the policy manager state machine.
■ debug pem events {enable I disable}: Enables or disables debugging of policy manager events.
Although having console or Telnet access to the remote AP is not always an option, you can gain a wealth of knowledge from the debugs you can run on the AP.
The H-REAP AP debugs are as follows:
■ debug capwap reap: Displays general H-REAP activities.
■ debug capwap reap mgmt: Displays client authentication and association messages.
■ debug capwap reap load: Displays payload activities, which are useful when the H-REAP AP boots in standalone mode.
■ debug dot11 mgmt interface: Displays 802.11 management interface events.
■ debug dot11 mgmt msg: Displays 802.11 management messages.
■ debug dot11 mgmt ssid: Displays SSID management events.
■ debug dot11 mgmt state-machine: Displays the 802.11 state machine.
■ debug dot11 mgmt station: Displays client events.
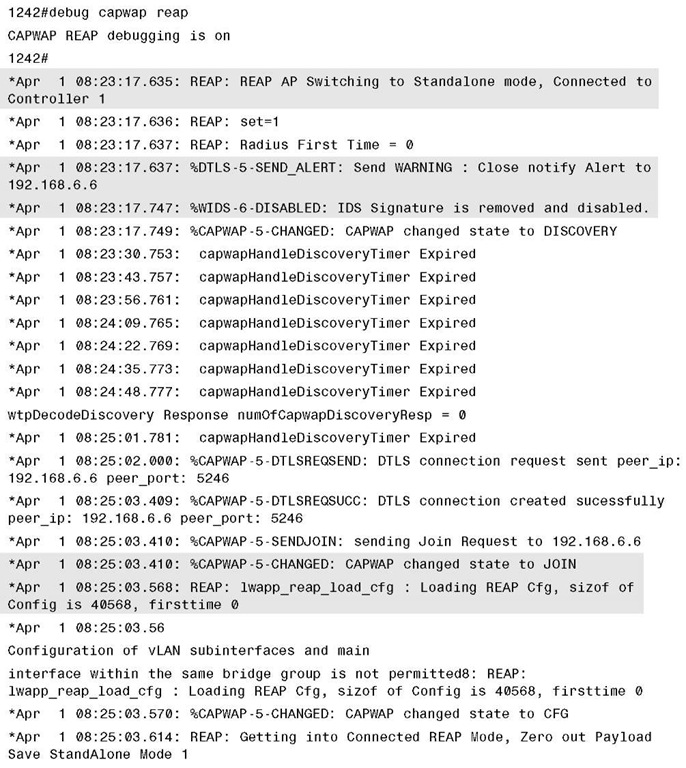
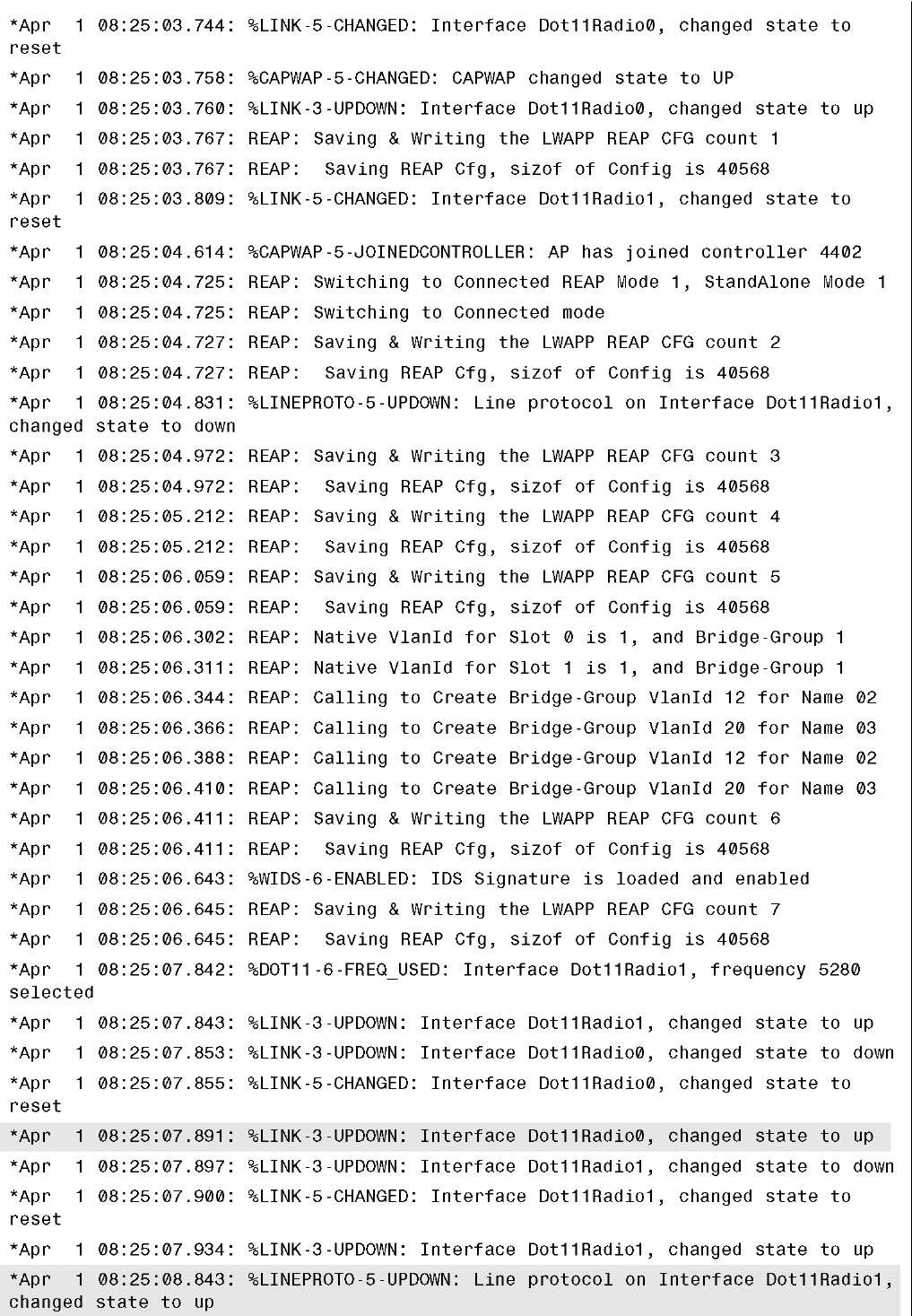
Example 13-15 shows the output from debug capwap reap. In this debug you can see the AP transition from connected to standalone mode. The AP sends a notification that it is closing the Datagram Transport Layer Security (DTLS) connection. When the controller is detected as being back up, the AP rejoins the controller, loads its configuration, and brings up its radios. Notice that the AP disables the IDS capability when it enters standalone mode.
Example 13-15 debug capwap reap Output
Example 13-15 debug capwap reap Output
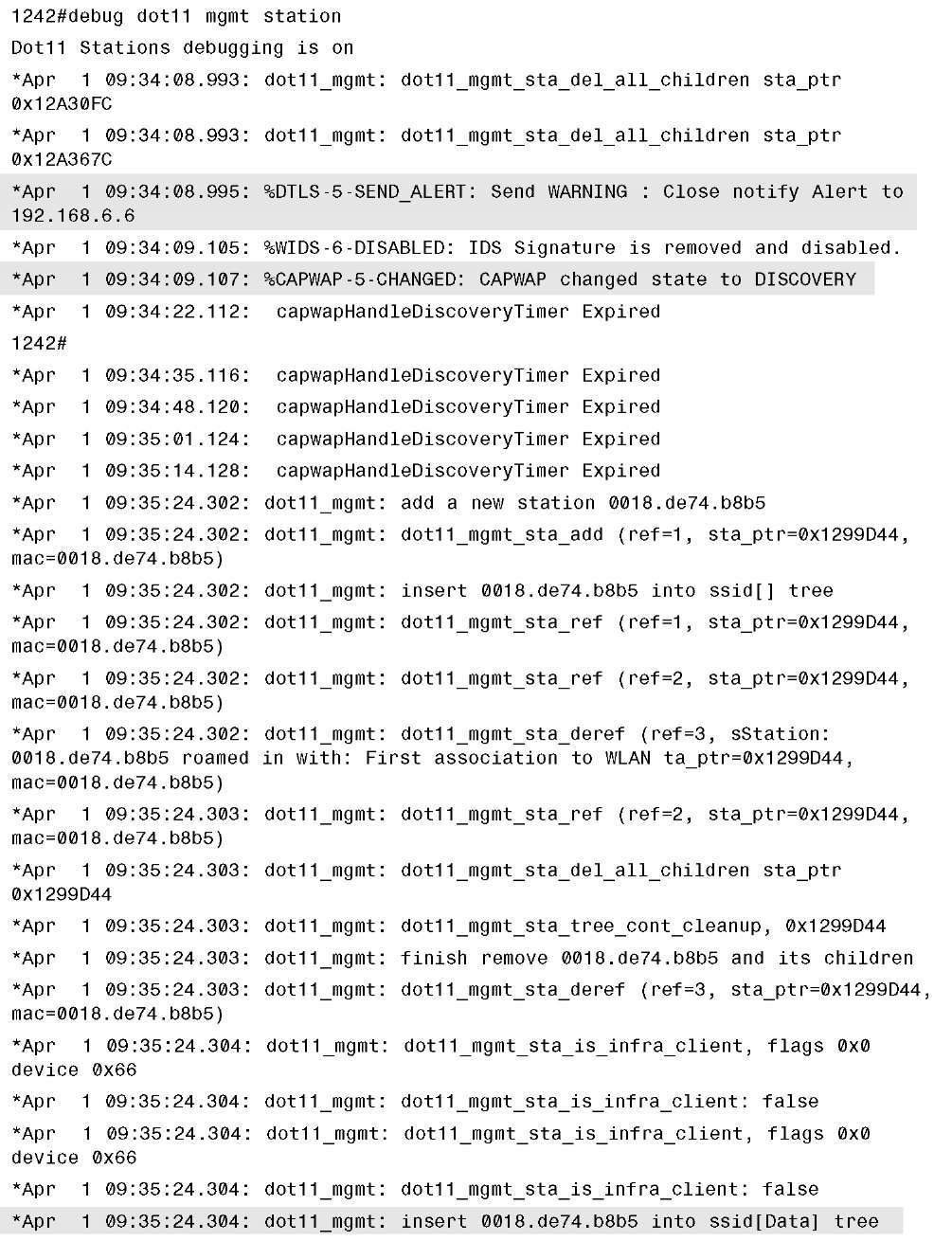
Example 13-16 shows the output from debug dot11 mgmt station, in which a client with MAC address 0018.de74.b8b5 is able to connect to a WLAN with SSID of data using WPA-PSK even though the AP just transitioned to standalone mode.
Example 13-16 debug dot11 mgmt station Output
Example 13-16 debug dot11 mgmt station Output
To troubleshoot backup RADIUS authentication and other events on the AP when it is in standalone mode, use the same IOS-based debugs you would use on an autonomous AP.
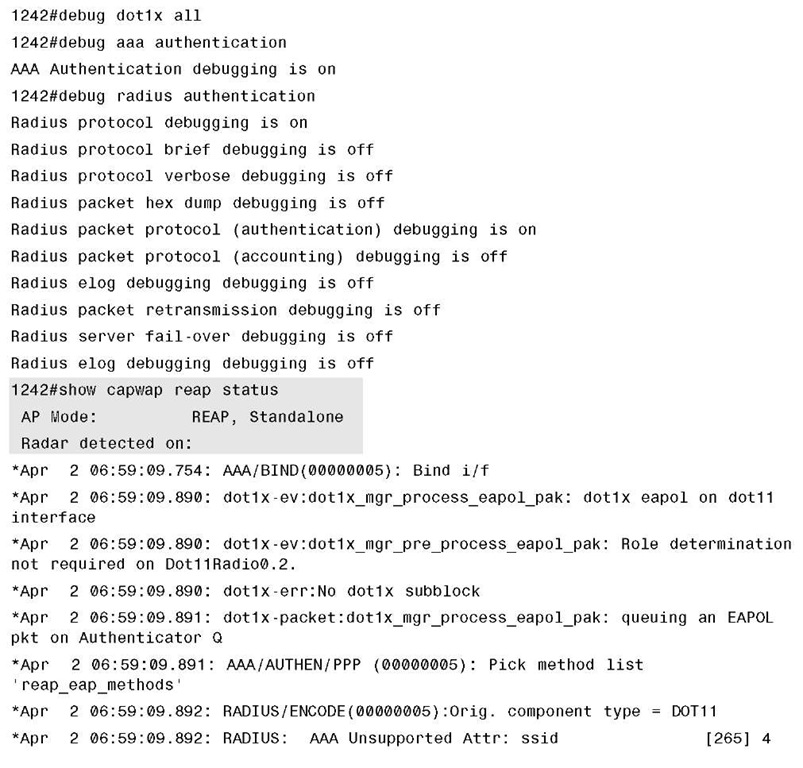
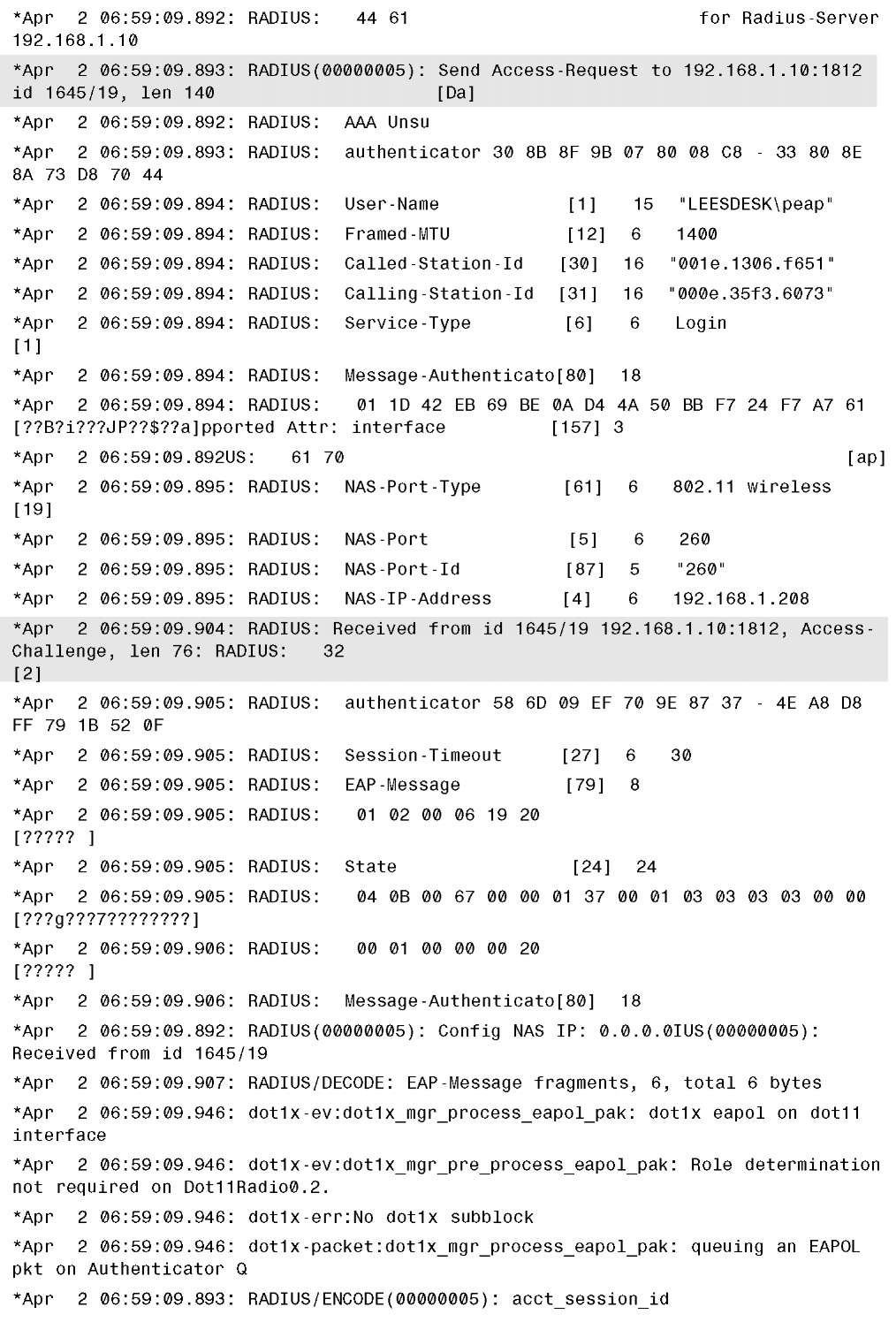
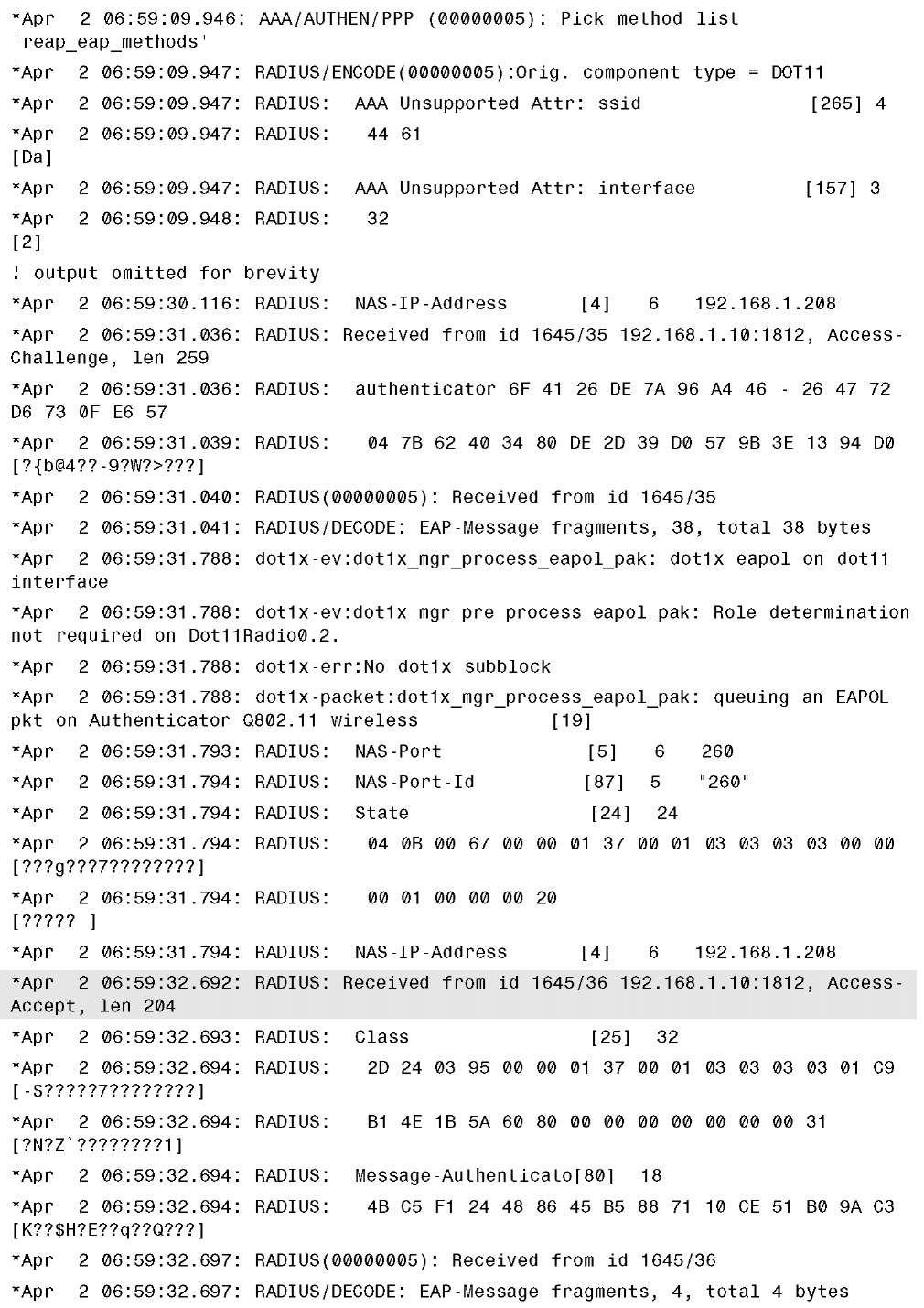
For example, in Example 13-17, which shows the output from debug dot1x all, debug aaa authentication, and debug radius authentication, you see a client with MAC address 000e.35f3.6073 authenticate using Protected Extensible Authentication Protocol (PEAP) to a backup RADIUS server while the AP is in standalone mode.
Example 13-17 debug dot1x all, debug aaa all, and debug radius authentication Command Output on H-REAP AP in Standalone Mode
Example 13-17 debug dot1x all, debug aaa all, and debug radius authentication Command Output on H-REAP AP in Standalone Mode
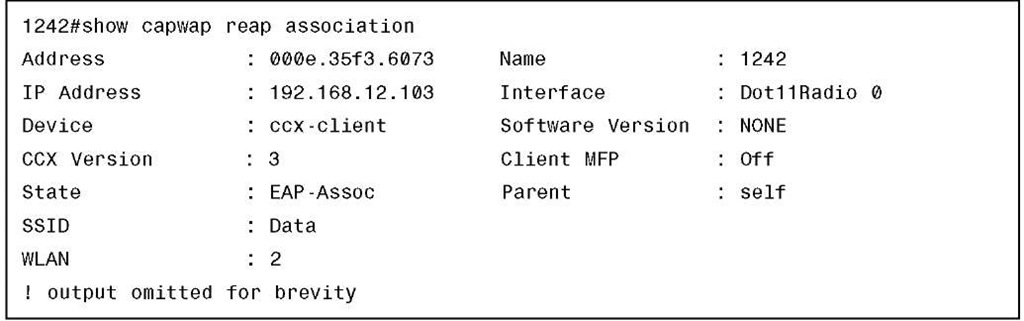
After completing authentication, you can see the client is successfully authenticated on the AP, as demonstrated in Example 13-18.
Example 13-18 show capwap reap association Command Output for a Backup RADIUS Client
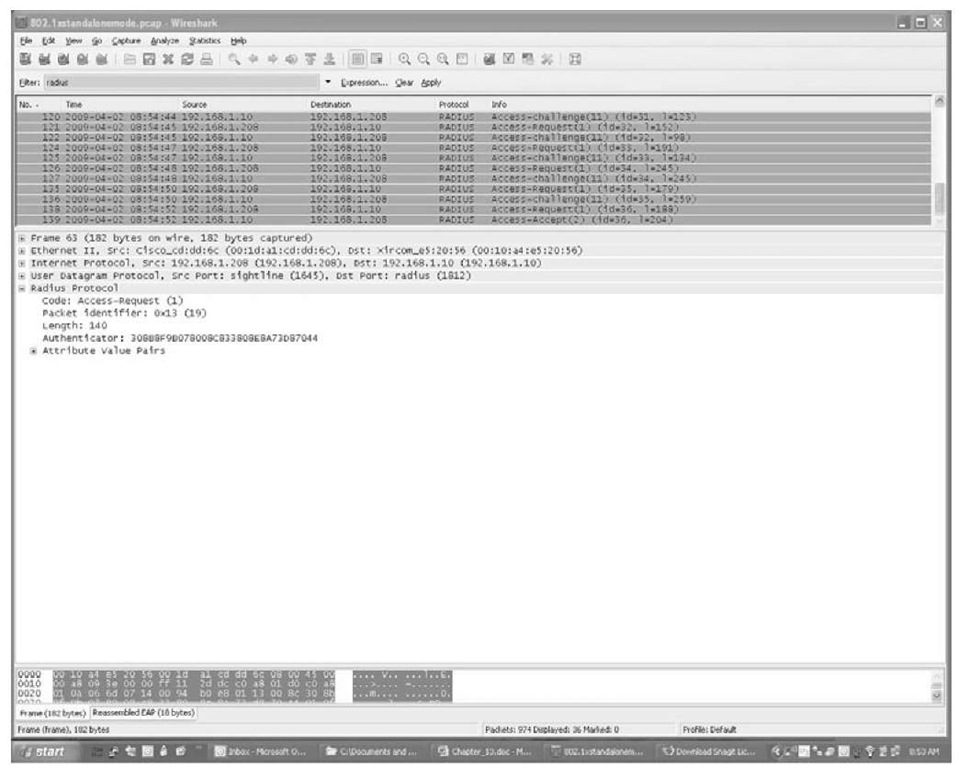
A packet capture from the H-REAP switch port shows the RADIUS request being sent directly from the AP. Figure 13-13 shows the RADIUS process and the Access-Accept from the RADIUS server.
Figure 13-13 Backup RADIUS 802.1x Authentication
As you can see in the figure, the RADIUS packets are bridged directly to the local network from the AP and are not encapsulated in an LWAPP/CAPWAP tunnel.
Summary
The H-REAP feature available with the wireless LAN controllers is a robust and flexible solution for providing wireless network access for small, remote satellite offices. When using H-REAP local switching, after the wireless clients pass authentication, the client traffic is bridged directly onto the local network by the AP. Understanding how the traffic flows and what authentication method, static WEP, WPA1/2-PSK, 802.1x, and so on that you want to use will dictate what local network resources you will need to configure and have available while the AP is in both connected and standalone mode. H-REAP helps you save money by allowing wireless access at these smaller locations without having to purchase a dedicated controller. This solution also helps save precious WAN bandwidth as only LWAPP/CAPWAP control traffic and not client data is tunneled across the network link to the controller.