A virtual private network (VPN) provides the equivalent of a private packet-switched network over the public Internet.3 It involves establishing a series of PVCs that run over the Internet so that the network acts like a set of dedicated circuits over a private packet network.
Basic Architecture
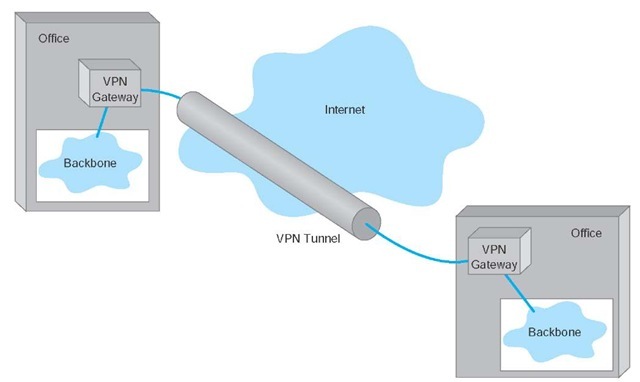
With a VPN, you first lease an Internet connection at whatever access rate and access technology you choose for each location you want to connect. For example, you might lease a T1 circuit from a common carrier that runs from your office to your Internet service provider (ISP). You pay the common carrier for the circuit and the ISP for Internet access. Then you connect a VPN gateway (a specially designed router or switch) to each Internet access circuit to provide access from your networks to the VPN. The VPN gateways enable you to create PVCs through the Internet that are called tunnels (Figure 9.12).
Figure 9.12 A virtual private network (VPN). ISP = Internet service provider
The VPN gateway at the sender takes the outgoing packet and encapsulates it with a protocol that is used to move it through the tunnel to the VPN gateway on the other side. The VPN gateway at the receiver strips off the VPN packet and delivers the packet to the destination network. The VPN is transparent to the users; it appears as though a traditional packet-switched network PVC is in use. The VPN is also transparent to the ISP and the Internet as a whole; there is simply a stream of Internet packets moving across the Internet. VPN software is commonly used on home computers or laptops to provide the same secure tunnels to people working from offsite.
VPNs operate either at layer 2 or layer 3. A layer-2 VPN uses the layer-2 packet (e.g., Ethernet) to select the VPN tunnel and encapsulates the entire packet, starting with the layer-2 packet. Layer-2 tunneling protocol (L2TP) is an example of a layer-2 VPN. A layer-3 VPN uses the layer-3 packet (e.g., IP) to select the VPN tunnel and encapsulates the entire packet, starting with the layer-3 packet; it discards the incoming layer-2 packet and generates an entirely new layer-2 packet at the destination. IPSec is an example of a layer-3 VPN.
The primary advantages of VPNs are low cost and flexibility. Because they use the Internet to carry messages, the major cost is Internet access, which is inexpensive compared with the cost of circuit-switched services, dedicated-circuit services, and packet-switched services from a common carrier. Likewise, anywhere you can establish Internet service, you can quickly put in a VPN.
There are two important disadvantages. First, traffic on the Internet is unpredictable. Sometimes packets travel quickly, but at other times, they take a long while to reach their destination. Although some VPN vendors advertise QoS capabilities, these apply only in the VPN devices themselves; on the Internet, a packet is a packet. Second, because the data travels on the Internet, security is always a concern. Most VPN networks encrypt the packet at the source VPN device before it enters the Internet and decrypt the packet at the destination VPN device.
VPN Types
Three types of VPNs are in common use: intranet VPN, extranet VPN, and access VPN. An intranet VPN provides virtual circuits between organization offices over the Internet. Figure 9.12 illustrates an intranet VPN. Each location has a VPN gateway that connects the location to another location through the Internet.
An extranet VPN is the same as an intranet VPN, except that the VPN connects several different organizations, often customers and suppliers, over the Internet.
An access VPN enables employees to access an organization’s networks from a remote location. Employees have access to the network and all the resources on it in the same way as employees physically located on the network. The user uses VPN software on his or her computer to connect to the VPN device at the office. The VPN gateway accepts the user’s log-in, establishes the tunnel, and the software begins forwarding packets over the Internet. An access VPN provides a less expensive connection than having a national toll-free phone number that connects directly into large sets of modems at the organization’s office. Compared with a typical ISP-based remote connection, the access VPN is a more secure connection than simply sending packets over the Internet. Figure 9.13 shows an access VPN.
How VPNs Work
When packets move across the Internet, they are much like postcards in the paper mail. Anyone can read what they contain. VPNs provide security by encapsulating (i.e., surrounding) packets in a separate, secure packet that is encrypted. No one can read the encapsulated data without knowing the password that is used to decrypt the packet (we explain how encryption works in next topic). Layer-2 and layer-3 VPNs work very similarly, except that layer-2 VPNs encapsulate the user’s data starting with the layer-2 packet (the Ethernet frame) while layer-3 VPNs encapsulate the user’s data starting with the layer-3 packet (the IP packet).
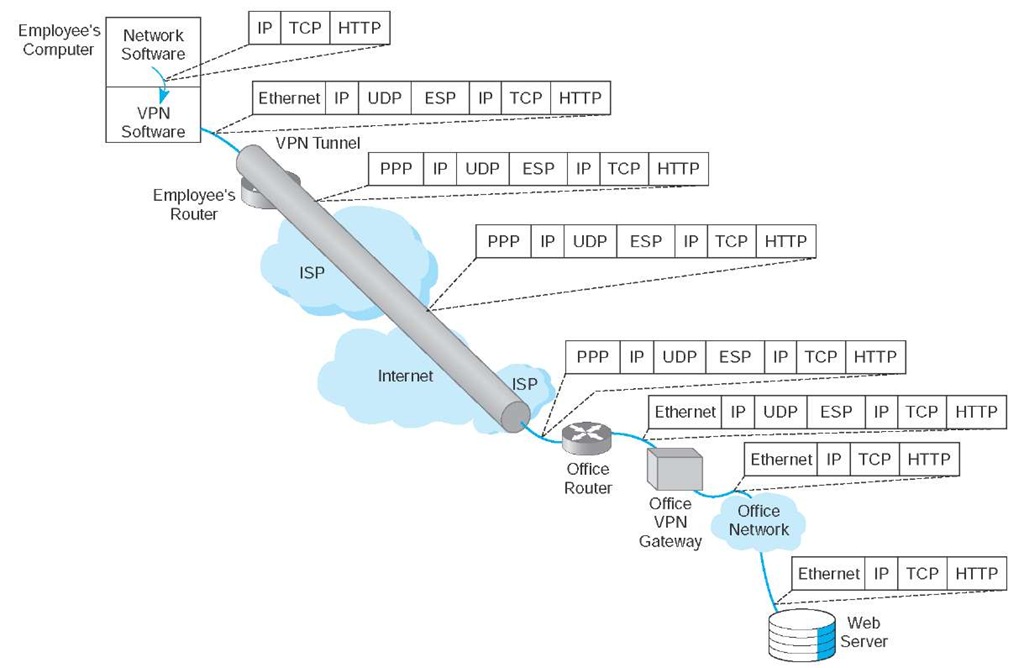
Figure 9.13 shows how a layer-3 access VPN using IPSec works. Suppose an employee is working at home with a LAN that uses a router to connect to the Internet via an Internet service provider (ISP) using DSL (we explain how DSL works in the next topic). When the employee wants to use the VPN, he or she starts the VPN software on his or her computer and uses it to login into the VPN gateway at the office. The VPN software creates a new "interface" on the employee’s computer that acts exactly like a separate connection into the Internet. Interfaces are usually hardware connections, but the VPN is a software interface, although the employee’s computer doesn’t know this—it’s just another interface. Computers can have multiple interfaces; a laptop computer often has two interfaces, one for Ethernet and one for wireless Wi-Fi.
The VPN gateway at the office is also as a router and a DCHP server. The VPN gateway assigns an IP address to the VPN interface on the employee’s computer that is an IP address in a subnet managed by the VPN gateway. For example, if the VPN gateway has an IP address of 156.56.198.1 and managed the 156.56.198.x subnet, it would assign an IP address in this subnet domain (e.g., 156.56.198.55).
Figure 9.13 Using VPN Software
The employee’s computer now thinks it has two connections to the Internet: The traditional interface that has the computer’s usual IP address and the VPN interface that has an IP address assigned by the VPN gateway. The VPN software on the employee’s computer makes the VPN interface the default interface for all network traffic to and from the Internet, which ensures that all messages leaving the employee’s computer flow through the VPN interface to the VPN gateway at the office.
Suppose the employee sends an HTTP request to a Web server at the office (or somewhere else on the Internet). The Web browser software will create an HTTP packet which is passed to the TCP software (which adds a TCP segment), and this in turn is passed to the IP software managing the VPN interface. The IP software creates the IP packet using the source IP address assigned by the VPN gateway. Normally, the IP software would then pass the IP packet to the Ethernet software that manages the Ethernet interface into the employee’s LAN, but since the IP packet is being sent out the VPN interface, the IP packet is passed to the VPN software managing the VPN interface. Figure 9.13 shows the message as it leaves the network software and is passed to the VPN for transmission: an HTTP packet, surrounded by a TCP segment, surrounded by an IP packet.
The VPN software receives the IP packet, encrypts it, and encapsulates it (and its contents: the TCP segment and the HTTP packet) with an Encapsulating Security Payload (ESP) packet using IPSec encryption. The contents of the ESP packet (the IP packet, the TCP segment and the HTTP packet) are encrypted so that no one except the VPN gateway at the office can read them. You can think of the IPSec packet as an application layer packet whose destination is the office VPN gateway. How do we send an application layer packet over the Internet? Well, we pass it to the TCP software, which is exactly what the VPN software does.
The VPN software passes the ESP packet (and its encrypted contents) to the employee’s computer normal Internet interface for transmission. This interface has been sitting around waiting for transmissions, but since the VPN interface is defined as the primary interface to use, it has received no messages to transfer except those from the VPN software.
This interface treats the ESP packet as an application layer packet that needs to be sent to the VPN gateway at the office. It attaches a transport layer packet (a UDP datagram in this case, not a TCP segment). It then passes the ESP packet to the IP software which creates an IP packet with an IP destination address of the VPN gateway at the office and a source IP of the employee’s computer’s normal Internet interface. It passes this IP packet to the Ethernet software, which adds an Ethernet frame and transmits it to the employee’s router.
The employee’s router receives the Ethernet frame, strips off the frame, and reads the IP packet. It sees that the packet needs to be sent to the VPN gateway at the office, which means sending the packet to the Employee’s ISP over the DSL circuit. Since DSL uses PPP as its layer-2 protocol, it adds a PPP frame and sends the packet over the DSL circuit to the ISP.
The router at the ISP strips off the PPP frame and reads the IP packet, which it uses to route the packet through the Internet. As the packet moves over the Internet, the layer-2 frame changes at each hop, depending on the circuit in use. For example, if the ISP uses a T3 circuit, then the ISP creates an appropriate layer-2 frame to move the packet over the T3 circuit (which usually is a PPP frame).
The packet travels from the Internet to the ISP that connects the office to the Internet and arrives at the office’s router. This router will strip off the incoming layer-2 frame (suppose the office uses a T-3 connection with PPP as shown in the figure), read the IP packet, and create an Ethernet frame that will send the packet to the office VPN gateway. The VPN gateway will strip off the Ethernet frame, read the IP packet, strip it off, read the UDP datagram, strip it off, and hand the ESP packet to its VPN software. The VPN gateway’s software will decrypt the ESP packet, and deen capsulate the IP packet (and the TCP segment and HTTP packet it contains) from the ESP packet. The VPN gateway now has the IP packet (and the TCP segment and HTTP packet) that was originally created by the software on the employee’s computer. The VPN gateway reads this IP packet and creates an Ethernet frame to send it on the next hop to its destination and transmits it into the office network, where it ultimately reaches the Web server. On this last leg of the journey after it leaves the VPN gateway, the packet is not encrypted and can be read like a normal packet on the Internet.
The return path from the Web server back to the employee’s computer is very similar. The Web server will process the HTTP request packet and create an HTTP response packet which it sends back to the employee’s computer. The source address on the IP packet that the Web server received was the IP address associated with the VPN interface on the employee’s computer, so the Web server uses this address as the destination IP address. This packet is therefore routed back to the VPN gateway, because the subnet for this IP address is defined as being in the subnet that the VPN gateway manages. Once again, the return packet is not encrypted on this part of the journey.
When the packet arrives at the VPN gateway, it looks up the VPN IP address in its table and sees the usual IP address of the computer associated with that VPN address. The VPN gateway creates an ESP packet and encrypts the IP packet from the Web server (and the TCP segment and HTTP packet it contains). It then treats the ESP packet as a application layer packet that needs to be sent to the VPN software on the employee’s computer; it passes it to its TCP software for a UDP datagram, then to its IP software for an IP packet, and then to its Ethernet software for an Ethernet frame and transmission back through the VPN tunnel.
When the packet eventually reaches the employee’s computer, it comes in the normal Internet interface and eventually reaches the TCP software that strips off the UDP datagram. The TCP software sees that the ESP packet inside the UDP datagram is destined for the VPN software (remember that TCP port numbers are used to identify to which application layer software a packet should go). The VPN software removes the ESP packet and passes the IP packet it contains to the IP software, which in turn strips off the IP packet, and passes the TCP segment it contains to the TCP software, which strips off the TCP segments and passes the HTTP packet it contains to the Web browser.
Cisco’s Metro Ethernet VPN
MANAGEMENT FOCUS
The Cisco Systems Inc. offices in San Jose, California, used a VPN network over the Internet through four SONET OC-3 links provided by different common carriers (the next topic discusses the Internet in more detail). Cisco needed more capacity, so when one of the common carriers decided to discontinue its SONET services, Cisco decided to move to metro Ethernet for some of its Internet connection.
Cisco replaced one OC-3 with a 200 Mbps metro Ethernet circuit from AT&T. AT&T installed two parallel 1 Gbps fiber optic circuits from the Cisco office into the AT&T network in San Jose. Only one circuit is in use; the other is a backup in case the first circuit fails.
The circuit connects into the AT&T network through an edge switch whose job is to add MPLS tags to the incoming frames to route them through the AT&T network to their destination. Although the circuit is capable of supporting 1 Gbps of data, this switch limits the circuit capacity to ensure that the circuit does not use more than the 200 Mbps of data that Cisco has contracted for. Cisco’s router into the AT&T network is also configured to only enable 200 Mps of data on this circuit. If Cisco needs more capacity, it can change its contract with AT&T and Cisco, and AT&T will change the capacity setting on their switch and router.
The circuit has proven to be very reliable and now provides 200Mbps at a lower cost than the previous OC-3 circuit. Cisco plans to convert the remaining OC-3 circuits to metro Ethernet in the coming years.
Energy Sciences Network
MANAGEMENT FOCUS
The Energy Sciences Network serves the U.S. Department of Energy and the thousands of corporate and university scientists doing research for it. It is one of the fastest wide area networks in the world because its users, researching high energy physics, human genomics, and climate modeling, routinely move terabyte-sized files across the network.
The current network uses a mixture of very high speed optical Ethernet services as well as high speed ATM, and moderate speed T3 circuits (see Figure 9.14). The Network has always been an early adopter of new technologies, so the San Francisco ring, currently running at 20 Gbps, will upgrade to 100 Gbps Ethernet within the next 2 years as it becomes available. Likewise, the older ATM portions of the network will gradually move to faster Ethernet services.