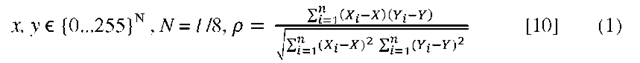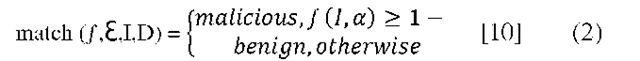Abstract
In multihop wireless sensor network (WSN) users or nodes are constantly entering and leaving the network. Classical techniques for network management and control are not conceived to efficiently face such challenges. New mechanisms are required, to work in a self-organized manner. The techniques found in nature promises WSN, to self-adapt the environmental changes and also self-protect itself from the malicious stuff. This paper introduces a biological inspired secure autonomous routing protocol (BIOSARP). The self-optimized routing protocol is enhanced with artificial Immune System (AIS) based autonomous security mechanism. It enhances WSN in securing itself from the abnormalities and most common WSN routing attacks. NS2 based simulation analysis and results of BIOSARP are presented. The comparison of proposed intelligent protocol with SAID and SRTLD security mechanisms for WSN is further exhibited, in terms of processing time and energy consumption.
Keywords: Artificial Immune system, Human Immune Blood Brain Barrier System, Human Immune System, Intelligence, Self-Optimization, Self-Security, Wireless Sensor Network.
Introduction
Wireless communication plays an important role in telecommunication sector and has huge importance for future research. The communication is making the world’s life easier with the development of sensing and monitoring systems. In these sensing and monitoring systems new gadgets and software advancement are frequently available to the end-user. In infrastructure less networks such as WSN, the deployment area may be out of human reach. The challenges such as growing complexity, unreachable maintenance and unsecure communication demand for mechanism that can maintain the features of WSN such as multihop routing in dynamically changing environmental in a complete autonomous mode. In order to address autonomous capability for multihop ad-hoc network, it has been visualize that self-organized and self-secure network application can fully realize the network operational objectives.
Probabilistic methods that provide scalability and preventability can be found in nature and adapted to technology. Towards this vision, it is observed that various biological principles are capable to overcome the above adaptability issues. The most well-known bio-inspired mechanism is the swarm intelligence (ANT Colony, Particle swarm), AIS and intercellular information exchange (Molecular biology)[1-4]. Many of AIS based algorithms, bee inspired algorithms such as BeeAdHoc [5], BiSNET/e [3] have been reported. However, self-healable security is still an open issue. Widespread acceptance and adaptation of these protocols in real world wireless networks would not be possible until their security aspects have thoroughly investigated [4]. [4] propose misbehaviour detection in nature inspired MANET protocol, BeeAdHoc.
This paper introduces the architecture for implementing Biological Inspired Secure Autonomous Routing Protocol (BIOSARP) consist an autonomous security management module on top of BIOARP [6].This paper is particularly on BIOSARP autonomous security module. The ACO based routing part BIOARP has been discussed in [6-8]. BIOSARP is based on the behaviour of human immune system (HIS). As HIS provides the complete security and protection to human body. The major aspect of HIS is to detect the anomalies by differentiating between self and non-self entities. The HIS security is used in the computer world with the name of artificial immune system (AIS).
General AIS algorithms are very complex and impracticable for WSN. The proposed AIS for BIOSARP algorithm is the extension of SRTLD [9] and SAID [10]. While implementing BIOSARP, the complexity factor is taken under consideration. Moreover, the blood brain barrier (BBB) system is enabled in BIOSARP in the initialization and learning period. These techniques will be accomplished by assigning each procedure to several groups of agents. These agents will work in a decentralized way to collect data and/or detect an event on individual nodes and carry data to the required destination. BIOSARP provides autonomous security, the mechanism overcomes the message alter, wormhole, sinkhole Sybil, selective forwarding and HELLO flood attacks.
The next section reviews the related research for self-security using AIS approaches. Section 3 describes the BIOSARP implementation. Section 4 shows the results and comparisons. The conclusion and future work are discussed in section 5.
Related Research
Wireless sensor nodes are mostly deployed in the unprotected/hostile environment. Therefore, it is easier for WSN to suffer with a number of attacks, due to sensor nodes resource constraints and vulnerabilities. These attacks involve signal jamming and eavesdropping, tempering, spoofing, resource exhaustion, altered or replayed routing information, selective forwarding, sinkhole attacks, Sybil attacks, wormhole attacks, flooding attacks and etc [11]. Many papers have proposed prevention countermeasures of these attacks and the majority of them are based on encryption and authentication. These prevention measures in WSN can reduce intrusion to some extent. In this case, intrusion detection system (IDS) can work as second secure defence of WSN to further reduce attacks and insulate attackers.
Overview of AIS Based Security in WSN
Overview of AIS based Security in WSN: In [10], the authors have proposed SAID with three-logic-layer architecture. SAID adopt the merits of local, distributive & cooperative IDS and is self-adaptive for intrusion detection of resource-constraint WSN. Knowledge base is deployed base station where the complex algorithm for agent evolution can be computed and intrusion rules can be stored.
Overview of Keying Based Security in WSN
Due to the factor of initialization phase, WSN need security mechanism to be in operation before the network deployment. As stated in [12] Node cloning attacks can be mounted only during deployment since a cloned node cannot initiate the protocol with success. It can be successfully connected only by acting as a responding node. Recent progress in implementation of elliptic curve cryptography (ECC) on sensors proves public key cryptography (PKC) is now feasible for resource constrained sensors [13]. The performance of PKC based security schemes is still not well investigated due to the special hardware characteristics.
In [9] the author presents the security enhancement which uses encryption and decryption with authentication of the packet header to supplement secure packet transfer. SRTLD solves the problem of producing real random number problem using random generator function encrypted with mathematical function. The output of random function is used to encrypt specific header fields in the packet such as source, destination addresses and packet ID. In this mechanism they assume that each sensor node is static, aware of its location and the sink is a trusted computing base. Security in natural inspired routing protocols is still an open issue [4].
BIOSARP Security Architecture and Methodology
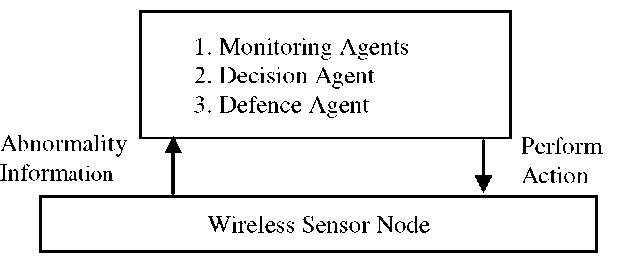
BIOARP is enriched with an autonomous security management; preliminary work is illustrated in [14]. We have divided the jobs among the agents. Agent works on two-layered architecture, agent layer on the top and wireless sensor network on bottom as shown in Figure 1.
Fig. 1. Two layer BIOSARP Self-Security Architecture
The autonomous security module cooperates with the routing management, neighbour management and power management modules to provide secure autonomous routing protocol for WSN. Whenever the neighbour table is checked to select the optimal node, the neighbouring node behaviour is monitored in the routing management. As soon as the abnormal behaviour is detected, the information is passed to security management module. The security module then matches the neighbouring node characteristics with the given threshold. If any neighbouring node mismatches, the security module classifies it as non-self and remove entry from neighbour table.
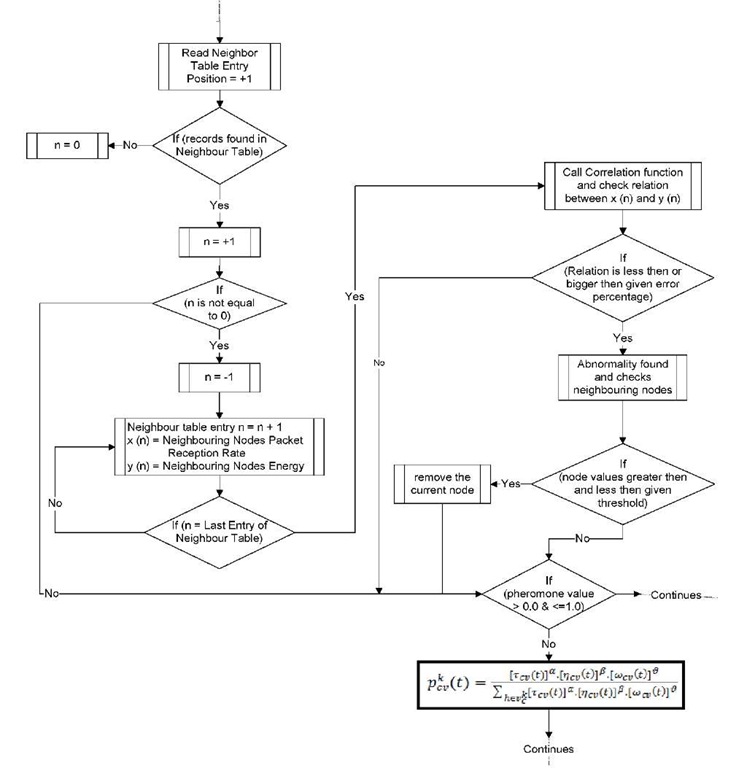
The flow of the system is elaborated with the help of flowchart as shown in Figure 2. Whenever routing management module wants to select the next best node, the monitoring agent checks the behaviour of neighbouring nodes. First, the numbers of records are counted in neighbour table. If no record is found the checking process is deferred until the neighbours are discovered. Otherwise, the behaviour checking continues with the initialization of variables as shown in Table 1.
After initialization the correlation coefficient function is called which determines the relationship difference between x and y arrays. The correlation coefficient is a statistical function as shown by Equation 1 to calculate the relation between two groups of same entity. The statistical matching rule produces a number between -1 and 1 that relates how similar the two input sequences are.
If the relation is having less or equal difference according to the given error rate, the process jumps to the selection criteria. Else, if the variation goes beyond detection agent is called to thoroughly check entry-by-entry in the current neighbour table. In the inspection, if any neighbouring nodes characteristics exceed the given threshold, the particular neighbour node is categorized as non-self by the decision agent. The decision based on the Equation 2 to classify node as self or non-self. After classification, the defence agent removes the non-self neighbouring nodes from the neighbouring table. Onwards ACO based routing procedure continues with pkij(t) as explained in [6].
where, I = Input string, D = Decision Agent’s matching String, f = Matching Function, £ = Matching Threshold.
Table 1. Security Parameters
Fig. 2. Flow Chart of BIOSARP Autonomous Security Management
BIOSARP is additionally enhanced with BBB system that secures WSN communication even in the initialization and learning phase. BBB is based on packet encryption and decryption, the work done on SRTLD [9]. In addition, the output of random generator function is used to encrypt specific header fields in the packet such as source, destination addresses and packet ID.
Results and Comparisons
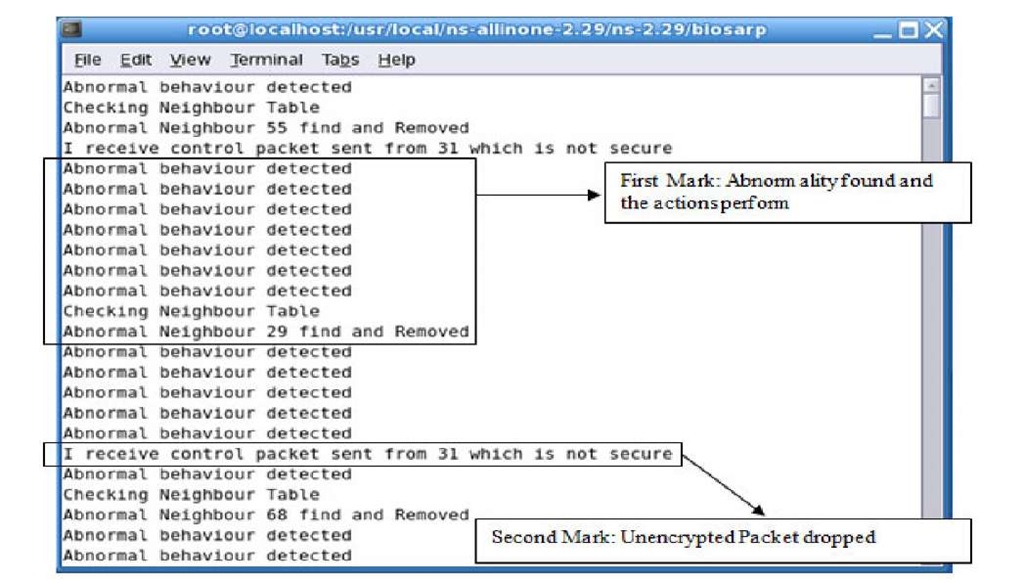
In the simulation study, NS-2 simulator is used to develop BIOSARP functional modules. Figure 3 shows the countermeasures against abnormalities found in WSN.
Fig. 3. NS-2 showing the Abnormality and actions taken against certain nodes
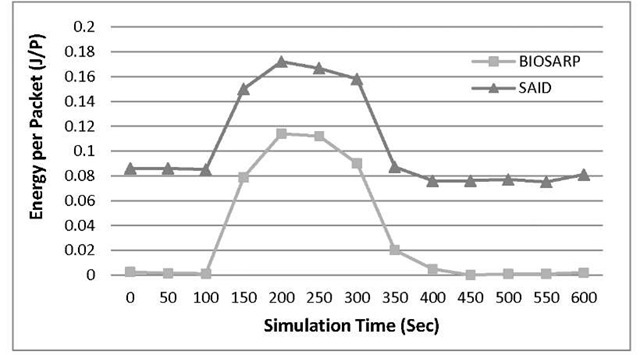
The simulation scenario is maintained as in [10] for BIOSARP and SAID comparison. When network has suffered attack by 10 malicious nodes, the power consumption value increased. Once the AIS self-security measure starts functioning, the energy consummation starts to reduce. And as soon as the malicious nodes stop attacking, the power consumption comes to the normal situation as observe at 450th sec in Figure 4.
Fig. 4. BIOSARP & SAID Comparison in terms of Energy
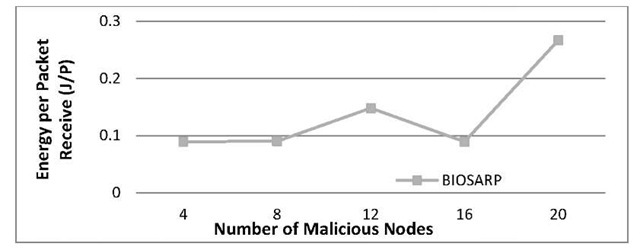
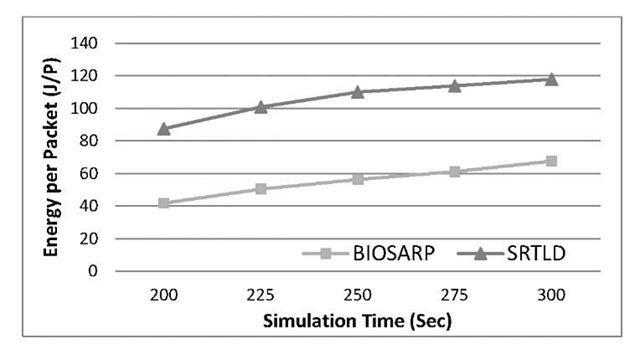
Figure 5 shows the performance of BIOSARP as the number of compromised node increases from 4 to 20. In Figure 5, the power consumption increases as the number of compromised nodes increases in order to overcome the routing hole problem. Figure 6 shows the comparison of BIOSARP with SRTLD in terms on energy consumption. WSN simulator consists of 121 nodes are distributed in 80m x 80m region. Nodes numbered as 120, 110, 100 and 90 are the source nodes, node 0 is the sink node and 29, 25, 31 and 36 are adversary nodes.
Fig. 5. Influence of increasing compromised nodes in network performance in terms of power consumption
Fig. 6. Performance Comparisons between BIOSARP and SRTLD in Terms of Energy Consumption against Simulation Time
Conclusion
A biological inspired secure autonomous routing protocol is proposed named as BIOSARP for WSNs. The article elaborates the security process of finding the abnormality based on AIS. BIOSARP consumes 6% less energy as compared to SAID. In simulation BIOSARP consumes 48% less power than SRTLD. The result shows that BIOSARP outperforms SRTLD due to the several reasons. First is BIOSARP provides preventive measure using AIS that can detect abnormalities before real attacks happen. Thus additional attacks including, acknowledgement spoofing attack, altered attack, replayed routing information attack and sybil attack can be further mitigated. Other reasons include the less rediscoveries and replies in neighbour discovery, thus reduces power consumption and processing power.
Our immediate future work will involve building and testing the architecture by the implementation of proposed system in the real WSN test bed.