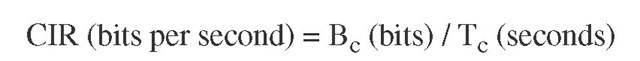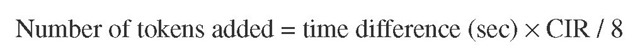Traffic shaping and policing are two different mechanisms for traffic conditioning. Both mechanisms measure the rate of different traffic classes against a policy or SLA. SLA stands for service level agreement, and it is usually set up between an enterprise and a service provider with regard to bandwidth, traffic rates, reliability, availability, QoS, and billing matters. Traffic shaping usually buffers the traffic that is in excess of the policy/agreement. Policing either drops the excess traffic or changes its marking to a lower level (re-marking). Therefore, traffic shaping is applied on an interface in the outbound direction, but traffic policing can be applied in either the inbound or outbound direction. These traffic-conditioning mechanisms are often deployed at network edge.
Because traffic policing merely drops or re-marks excess traffic, it does not impose delay to the conforming (non-excess) traffic. If the excess traffic is dropped, it has to be retransmitted. Traffic policing can re-mark and transmit excess traffic instead of dropping it. Traffic shaping buffers excess traffic and releases it steadily based on the policy specifications. Traffic shaping comes in many variations, including class-based traffic shaping, FRTS, generic traffic shaping (GTS). Cisco IOS traffic-shaping tools do not provide the means for re-marking traffic.
The main purposes for traffic policing are as follows:
■ To limit the traffic rate to a value less than the physical access rate—This is called enforcing subrate access. When the customer pays for an access rate (for example, 1.544 Mbps) that is less than the physical access rate (for example, 155.52 Mbps) between customer and service provider facilities, the provider uses rate limiting (policing) to enforce the subrate value.
■ To limit the traffic rate for each traffic class—When an enterprise and service provider have an SLA that states the maximum rate for each traffic class (or marking), the provider uses traffic policing to enforce that SLA (at the edge).
■ To re-mark traffic—Traffic is usually re-marked if it exceeds the rate specified in the SLA. Cisco IOS traffic policing allows you to mark and re-mark Layer 2 and Layer 3 protocol data units (PDU) such as IP precedence, IP DiffServ Codepoint (DSCP), Ethernet 802.1Q/p class of service (CoS), Frame Relay DE, and so on.
Following are the main purposes for traffic shaping:
■ To slow down the rate of traffic being sent to another site through a WAN service such as Frame Relay or ATM—If the remote site or the carrier network becomes congested, the sending device is usually notified (such as by Frame Relay backward explicit congestion notification, or BECN), and it can buffer the traffic and drop its sending rate until the network condition improves. Different access rates at two sites connected via a wide area service is a common situation called asymmetric circuit end access bandwidth. However, sometimes the receiving end becomes congested and the senders have to slow down through shaping not due to asymmetric bandwidths, but because many sites send traffic to a single site at once; this is called aggregation.
■ To comply with the subscribed rate—A customer must apply traffic shaping to the traffic being sent to the service provider WAN (FR or ATM) or Metro Ethernet networks.
■ To send different traffic classes at different rates—If an SLA specifies a particular maximum rate for each traffic class (with specific markings), the sender must perform class-based traffic shaping to prevent traffic from being dropped or re-marked.
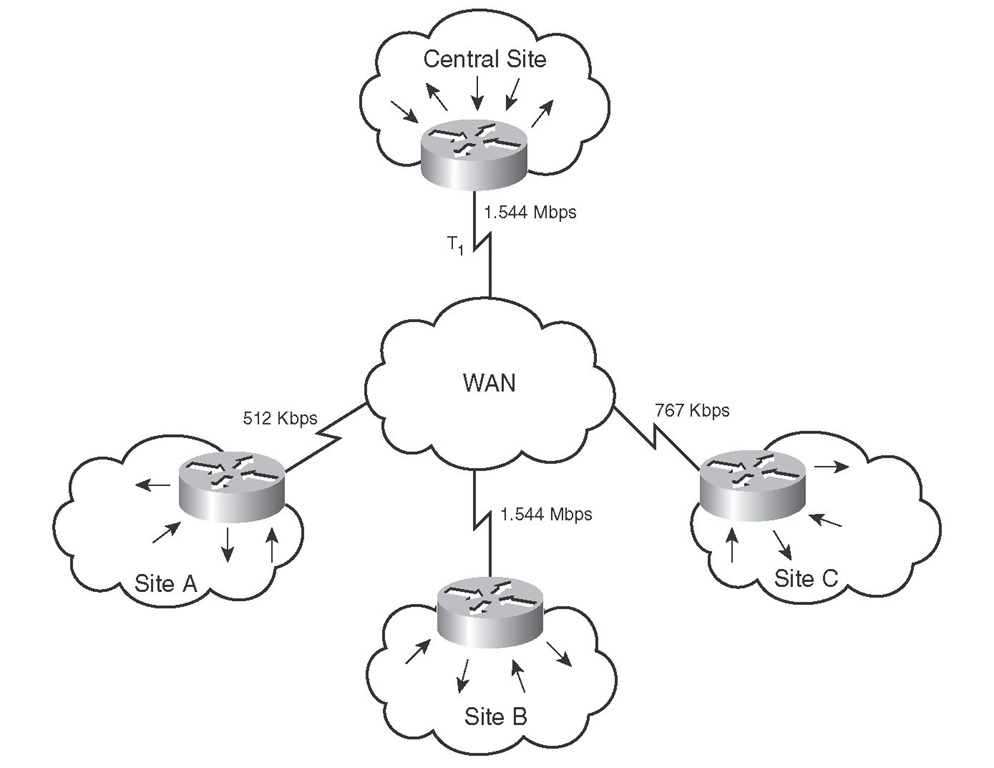
Figure 5-6 shows an enterprise that has a central site and three remote sites connected using Frame Relay virtual circuits. All the access rates at these sites are different. If the central site sends traffic at 1.544 Mbps (T1) to site A, then site A, which has a 512-Kbps access rate, will have congestion and possibly drops. To avoid that, the central site can shape the traffic being sent to site A. The rate mismatch between the central site and site A is an example of an asymmetric bandwidth situation. What will happen if sites A, B, and C simultaneously send traffic to the central site? In that case, if all remote sites send traffic at their maximum access rates, congestion will result, this time at the central site; that is because the aggregate traffic from the remote sites exceeds the access rate at the central site.
Figure 5-6 Speed Mismatch and Aggregation Require Traffic Shaping
Where does traffic shaping and traffic policing usually take place? The CE devices can perform policing on the interfaces facing inside their site and enforce traffic rates. For instance, bulk traffic such as file-transfer over the WAN can be limited to a specific rate. Service providers usually perform policing on the edge device of their network on the interface receiving or sending traffic to the customer devices. Traffic shaping is often performed on the customer edge (CE) device, outbound on the interface sending traffic to remote sites over the provider backbone.
Traffic shaping and policing similarities and differences are as follows:
■ Both traffic shaping and traffic policing measure traffic; sometimes, different traffic classes are measured separately.
■ Policing can be applied to the inbound and outbound traffic (with respect to an interface), but traffic shaping applies only to outbound traffic.
■ Shaping buffers excess traffic and sends it according to a preconfigured rate, whereas policing drops or re-marks excess traffic.
■ Shaping requires memory for buffering excess traffic, which creates variable delay and jitter. Policing does not require extra memory, and it does not impose variable delay.
■ If policing drops packets, certain flow types such as TCP-based flows will resend dropped traffic. Non-TCP traffic might resend a lot more traffic than just the dropped ones.
■ Policing can re-mark traffic, but traffic shaping does not re-mark traffic.
■ Traffic shaping can be configured based on network conditions and signals, but policing does not respond to network conditions and signals.
Measuring Traffic Rates
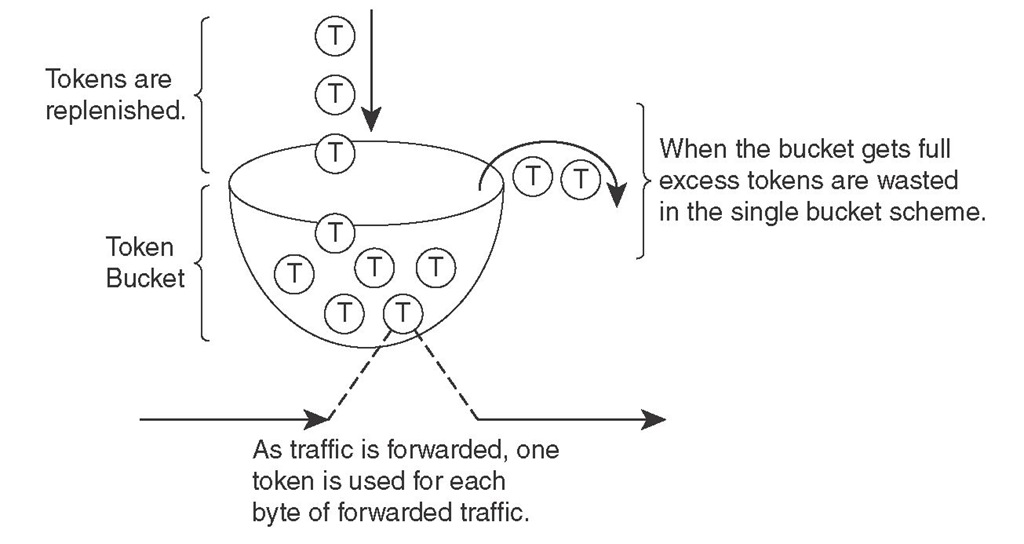
The operating systems on Cisco devices measure traffic rates using a bucket and token scheme. The token and bucket scheme has a few variations: single bucket with single rate, dual bucket with single rate, and dual bucket with dual rates. The Cisco ONT course covers only the single bucket with single rate model. To transmit one byte of data, the bucket must have one token. Tokens are put into the bucket at the rate equivalent to the SLA rate; for example, for a Frame Relay virtual circuit, the committed information rate (CIR) is used as the guide to replenish tokens in the bucket. If the size of data to be transmitted (in bytes) is smaller than the number of tokens, the traffic is called conforming; when traffic conforms, as many tokens as the size of data are removed from the bucket, and the conform action, which is usually forward data, is performed. If the size of data to be transmitted (in bytes) is larger than the number of tokens, the traffic is called exceeding. In the exceed situation, tokens are not removed from the bucket, but the action performed (exceed action) is either buffer and send data later (in the case of shaping) or drop or mark data (in the case of policing).
Figure 5-7 shows that tokens are dropped into the bucket based on an SLA rate; it also shows that if the bucket becomes full, excess tokens spill and are wasted in the single bucket model. Furthermore, Figure 5-7 shows that when traffic is forwarded one token is needed for each byte of data.
Figure 5-7 Single Bucket, Single Rate Token Bucket Scheme
It is important to know the definitions and relationships between the parameters within the token bucket scheme. CIR stands for committed information rate, Bc stands for committed burst, and Tc stands for committed time interval. The relationship between these parameters is as follows:
Instead of continuously dropping tokens into the bucket, and when the bucket is full, discarding the just-added tokens, the operating system adds tokens to the buckets only when there is traffic activity. Every time a packet arrives, the operating system computes the time difference between the arrival time of the new packet and the arrival time of the last packet, and for the time difference computed, it adds the appropriate number of tokens according to this formula:
The time difference between the current packet arrival time and the previous packet arrival time is computed in seconds and then multiplied by CIR (which is expressed in bits per seconds) to compute the number of bits. Then the result is divided by eight to compute the number of bytes. The number of bytes computed indicates the number of tokens that should have been added to the token bucket during the time between the arrival of the last packet and the arrival of the current packet. The computed number of tokens is added to the bucket right away. The total number of tokens (bytes) in the bucket cannot exceed the Bc value. Any extra tokens are discarded and therefore wasted. Administrators usually specify the CIR and Bc values and let the system compute the Tc value automatically. The larger the Bc value, the larger burst of data that is possible; with a large Bc value, the bucket saves more tokens.
Cisco IOS Policing and Shaping Mechanisms
Cisco IOS offers class-based traffic policing. Using modular QoS command-line interface (MQC), class-based traffic policing is applied to a class within a policy map with the police command. As stated in the previous section, Cisco IOS offers different Token Bucket schemes for policing: single bucket/single rate, dual bucket/single rate, and dual bucket/dual rate. Furthermore, multiaction policing—meaning taking multiple actions when traffic conforms, exceeds, or violates—is also supported by class-based traffic policing. In addition to Cisco routers, class-based traffic policing is available on some Cisco Catalyst switches.
Cisco IOS also offers class-based traffic shaping. Using MQC, class-based traffic shaping is applied to a class within a policy map. When used in combination with CBWFQ, class-based traffic shaping controls the upper limit of the outgoing traffic rate for a class, while the bandwidth statement guarantees the minimum bandwidth or rate for that class.
Frame Relay traffic shaping controls Frame Relay traffic only and can be applied to a Frame Relay subinterface or Frame Relay DLCI. Whereas Frame relay traffic shaping supports Frame Relay fragmentation and interleaving (FRF.12), class-based traffic shaping does not. On the other hand, both class-based traffic shaping and Frame Relay traffic shaping interact with and support Frame Relay network congestion signals such as BECN and forward explicit congestion notification (FECN). A router that is receiving BECNs shapes its outgoing Frame Relay traffic to a lower rate. If it receives FECNs, even if it has no traffic for the other end, it sends test frames with the BECN bit set to inform the other end to slow down.
Enterprises apply traffic policing at the access and distribution layers to control traffic entering the core or leaving the campus toward the WAN circuits. Most enterprises apply traffic shaping on the interfaces of the edge devices connected to WAN service. Traffic shaping is useful when speed mismatch or aggregation occurs and you want to avoid congestion and drops. Service providers apply traffic policing on the interfaces of the edge devices receiving traffic from customers; this helps them meter different traffic class rates against the SLA rates. Service providers also apply traffic shaping on the edge devices, sending traffic to customer sites.