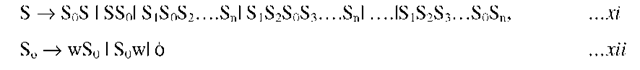Abstract
Numerous applications are envisioned with the proliferation of mobile usage in this decade. Third party billing system for subscription is one of them. Third party billing system needs acquisition of data from both users’ handset and base satiation of the service providers. Trustworthiness and Synchronization are the characteristics that need to be ensured of the third party billing system. A scheme, Multiple Authorizations by Multiple Owners (MAMO) is proposed in this work to address trustworthiness of the third party billing system. Along with a billing framework is designed to overcome synchronization problem during acquisition of data from multiple sources. MAMO is illustrated for trustworthiness of the third party billing system in this proposed work. But it could be practiced in many applications e.g. collaborative working environment of document editing for protecting alternation of data without permission of author by non-authors within a file. Although the billing framework is illustrated for synchronization of data during acquisition of data from two sources, it could be extended to synchronization among multiple sources too.
Keywords: Authorization, Ownership, collaborative, Read only, Add Beginning, Add End.
Introduction
Third party billing is increasingly being popular across the globe in many services including mobile billing system. Information like call duration as recorded in the base station is of course the primary quotient to compute the bill. Another aspect of billing is the availability of the network especially for post-paid connection. Monthly rental needs to be charged based on the availability of the network. Thus if network gets unavailable; the rental needs to be adjusted. In third party billing, such information is sent as text data to the third party billing section by the base station of the service provider.
However, factors like the signal strength as perceived in the mobile devices could be significant especially when many calls were made during short period of time to a particular phone number. Such data is to be collected from the log of the mobile device. The final billing is done after reconciliation of the data from the subscriber’s hand set and that from the base station of the service provider.
However, there is always a chance to distort the primary information intentionally or unintentionally. This may affect the consistency and trustworthiness of the business process. In order to maintain the credibility of the third party billing system, one need to ensure that whatever information is sent by the base station or the subscriber is not altered. However, new information needs to be added for bill generation, payment and other housekeeping jobs.
This work is proposed to addresses that allows multiple authorizations for different sections of a text document using a mechanism namely MAMO. A section which is authored by an author only has an access right for alternation. This is to ensure that the integrity of the data is maintained as set by owners in different source points of the mobile network and sent to third party billing section for reconciliation before billing or rebate.
MAMO could also be envisioned in collaborative text editing environment.
This paper commence with the brief summary of the work, following the introduction section. Then related works are summarized just immediate below this paragraph. In the next section our proposed work MAMO is presented with different type of authorizations and then followed by the formulation of the solution. In the next section implementation of MAMO is done. Implementation comprises of software requirements, and diagrams. Finally conclusion is drawn of this work following the future scope of work. This paper ends with the reference section.
A secure, private communication channel is always in demand to share data with others. A large majority of the applications use techniques like cryptography or, watermarking, steganography have been deployed for secret writing or covered writing respectively for different applications. The performance of loose and high coupling was evaluated to build hybrid network for 3G by [2]. Interestingly low response time, jitter and end to end delay was experienced with the loose coupling that definitely effects billing. The video call billing was proposed using an embedded watermarking technique by [3]. Each video sequence is transmitted by the embedded watermark to trace the network noise which is evaluated at the recipient end. Learning of new services in 3G environments has been proposed to be quickening by the usage of AJAX in [4]. A third party billing system has been proposed by [5]. Context has been enveloped to compute the real time billing. [6] proposes a content based billing was proposed by the least common multiple capacity algorithm in 3G environment. The performance result outperforms its contemporary. A different aspect of multi grade services was analyzed in IP multimedia subsystem to provide flexible charging scheme with QoS provisioning in [7]. Watermarking, a means of hiding copyright data within images, are becoming necessary components of commercial multimedia applications that are subject to illegal use [9]. Internet is overwhelmed by the digital assets like image, audio etc. In [9], a fragile watermarking scheme has been proposed that detects and locates even minor tampering applied to the image with full recovery of original work. Steganography [10] covers data within audio or video file. A radically different approach, cantered on natively representing text in fully-fledged databases, and incorporating all necessary collaboration support is presented in [1]. The concept and architecture of a pervasive document editing including management system has been discussed in [11]. Database techniques and real-time updating are used to do collaborative work on multiple devices. COSARR combines a shared word-processor, chat-boxes and private access to internal and external information resources to facilitate collaborative distance writing [12]. However, multiple authorizations in synchronous writing involving multiple users have not been considered in either of [1, 11, or 12].
Other related important works include classification of text blocks of bibliographic items which compose understanding thesaurus [13]. This method includes incompletely recognized text distantly and utilizes it for reference. It improves the efficiency of digital library. Internet based collaborative writing tool with comparison results are shown in [14]. The Xaxis proposes a framework for web-based collaborative application in an Air Force dealing with dynamic mission re-planning [15]. A developing platform is proposed for collaborative e-commerce on which awareness is the key for users to learn all sorts of information about people and system in this environment [16]. It presents the analysis of traits of awareness information in collaborative e-commerce environment. An analysis method based on rules for software trustworthiness is proposed in [17]. It mainly focused on the trustworthiness of software component and lifecycle process. The trustworthy resource extraction rules, analyzing rules and synthesis rules was discussed.
Our investigation reveals that there is no proposal in the literature till date to impose multiple authorizations on different segments by multiple owners within a document.
MAMO – Multiple Authorizations by Multiple Owners
A trusted third party billing framework has been proposed based on securing the key parameters for billing using a novel, manifold authorization technique called Multiple Authorizations by Multiple Owners (MAMO). Each of the multiple messages is authorized by the author of the message.
Data would be acquired from the base station as well as mobile handset by the third party billing section. Appropriate authorization of the data will be set priory by both the service provider (base station) and handset. Such authorization will remain enforced until and unless the author (owner) itself changes it.
Message from the base station is considered as primary source for billing. Authorized data would reach via a message from the base station and handset too. Associated massages will be reconciled at the third party billing section.
Different types of authorizations of MAMO are defined as below:
• Read Only - The segment cannot be modified by any users.
• Add Beginning - Text may be added only at the begging of the segment but nowhere else by any users. Existing text of the segment can not be modified.
• Add End - Text may be added only at the end of the segment but nowhere else by any users. Again existing text of the segment can not be modified.
• Add without Altered - Text may be added anywhere of the segment but existing text cannot be modified by any users.
• Add with Altered - Existing text may be modified as well as new text could be added by the users.
Now the challenge is how to implement these authorizations and along with its ownership? The following segment is elaborately discussed with these issues.
The proposed Multiple Authorizations by Multiple Owners (MAMO) methodology is described with a formal representation using the help of theory of automata. Consider the grammar
where
Vn is a finite, nonempty set whose elements are called variables, X is the set of alphabet | set of punctuation symbol | set of integers | (where ^ implies Null),P is a production rule that impose the authorization by the owner of the segment, and S is called the start symbol of Vn.
In this context, the start symbol is implied as section with any granularities (a word, or line or paragraph, or entire document) on which authorization mode is embodied by owner. The authorization mode is checked before accessing the section. If imposed authorization mode is satisfied then user can only access the document. Access privileges are according to the authorization mode for example if owner specifies Add Beginning on the fragment, user can only add text before the fragment but nowhere else. The authorization mode is formulated by a set of production rules set by the owner. Now rules for different authorization mode are specified below:
Read only mode is formulated by the following rules:
Add Beginning mode is formulated by the following rules:
where w is any string that in![]() implies Null.
implies Null.
Add End mode is formulated by the following rules:
Add without alter mode is formulated by the following rules:
Add with alter mode is formulated by the following rules:
where Si denotes any of Si, S2, … , Sn
Billing Frameworks
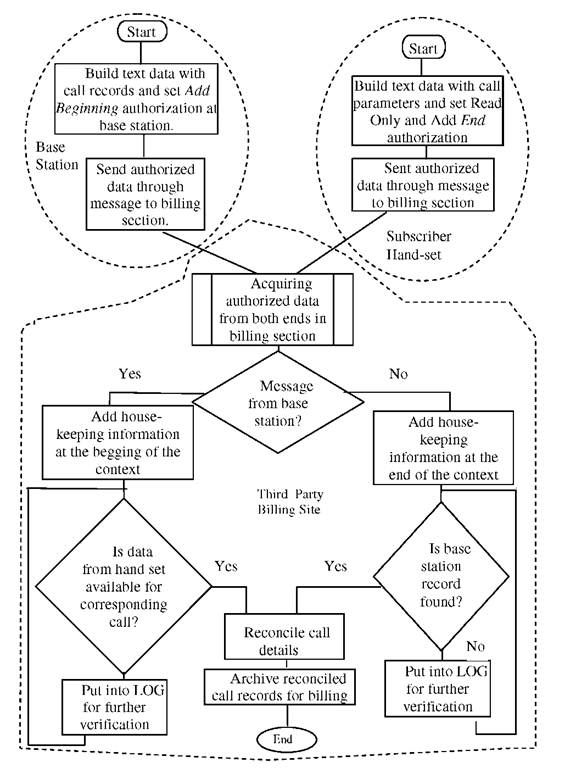
The proposed trusted third party billing mechanism is illustrated with the help of a block diagram in figure 1. Data regarding a call of base-station and subscribers’ hand set need to be acquisitioned by the third party billing section through messages. Before sending predefined authorization is imposed on concerned data within a message by the base station as well as subscribers’ hand-set.
Messages are acquired and reconciled into one message by the third party billing site. First the message is checked to determine from which source it has come. After determining the type of the received message housekeeping information is added conforming to predefined authorization as per MAMO. Then associated message of the same call is searched in the following step. If the associated message is found both messages are reconciled into one. Otherwise, received message is put into the log for further processing.
When associated message is arrived late compared to its counterpart into the billing site an interruption is occurred to get the already received message from the concerned log. Then do the same as mentioned in the above paragraph.
If the associated message is not received within subscription period a policy decision need to be specified that would be transparent to all the parties.
Human intervention is minimized in this framework. Addition and alternation within received message and reconciled message are allowed only as per MAMO. Reconciled message is archived for billing.
Implementation
The following characteristics are envisioned on implementation of MAMO to build it professionally acceptable.
• Imperceptible- MAMO (rules) is invisible to users and owners. Thus rules need to be mapped by invisible characters that are not shown in the editor.
• Compatibility -Compatibility of authorization modes are shown in table 1.
• Robustness – Rules should not be distorted by text processing functionalities. If any rule is distorted by text processing functionalities, then editor is unable to open the segment and consequently a semantic message is thrown.
• Protection - Extraneous data are embedded with rules and then encryption is performed. The encrypted rules are inserted into the document.
Fig. 1. Block diagram of the billing mechanism
Table 1. Compatibility of Authorization Modes
|
Authorization |
Read |
Add |
Add |
Add |
Add |
|
Modes |
only |
Beginning |
End |
without |
with |
|
|
|
|
|
alter |
alter |
|
Read only |
- |
Yes |
Yes |
No |
No |
|
Add Beginning |
Yes |
- |
Yes |
Yes |
No |
|
Add End |
Yes |
Yes |
- |
Yes |
No |
|
Add without alter |
No |
Yes |
Yes |
- |
No |
|
Add with alter |
No |
Yes |
Yes |
No |
- |
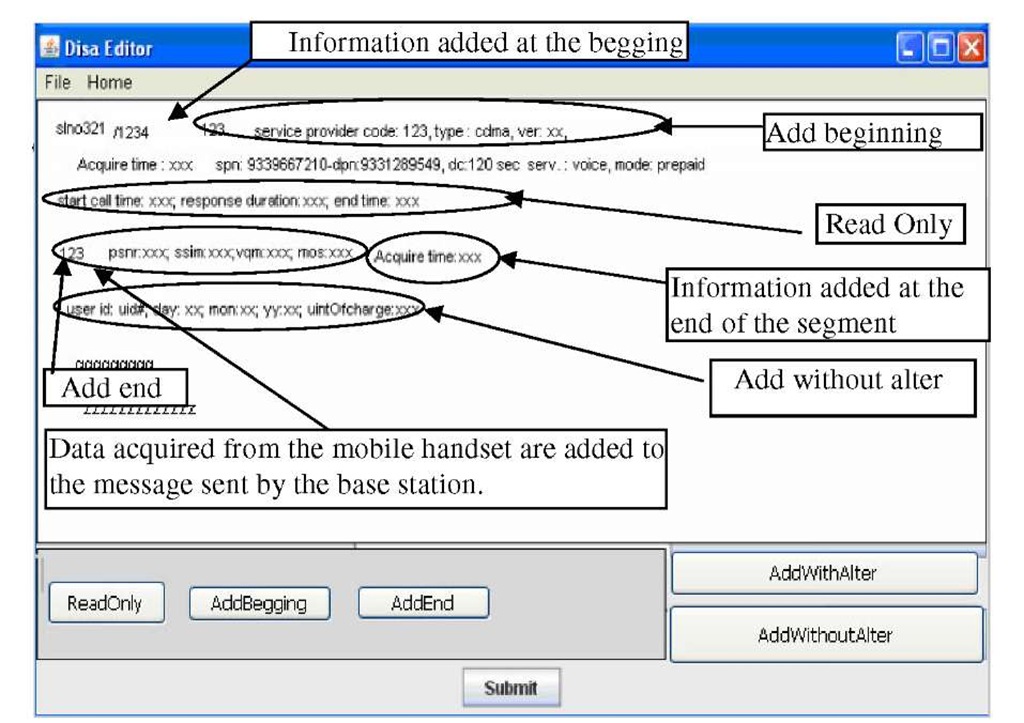
The Application has been simulated in Java environment. Rich text format is taken as message format and netBeans 6.5 is used as an IDE on Microsoft platform. Different authorizations on multiple messages in a single file are shown in figure 2. Authorization is imposed either on a line or a paragraph, or a set of paragraphs.
A message contains different type of information in different parts, referred as sections in the rest of this document. Different access rights may be imposed on different sections by multiple sources. The source may be log information of the handset or calls details of the base station. As for example, call duration, source address, destination address, and network availability are acquired from the base station are all read only in nature. However, data could be added before all this information maintaining the read only authorization. Data on signal strength, signal to noise ratio etc are acquired from the handset also read only type located in another section of the message/file. But, data may be added at the end of this information.
Little information needs to be added for housekeeping purposes by the third party and will be located in a third section of the message (see figure 2). All the fields here are assumed for the sake of explaining the concept. Based on the applications and the agreement of services the exact content of the messages would be determined.
Exception Handling: A few typical questions on failure scenarios may occur. A couple of these may be considered.
What will happen if handset message reach before the base station message?
Or, what happen if handset message is lost?
A solution to the first problem could be that handset message will be put into the log book for further verification. In the second scenario, a fresh request for the data from handset may be initiated depending upon the terms and conditions for connection. However, as the primary billing parameters are already available; bill may still be generated without reconciliation with handset message.
Result
The experiment is simulated in Java environment. The numbers of mobile calls within a range of time are generated in random order. The range of time is fixed to ten minutes.
Fig. 2. Instance of a sample message for reconciliation
A random number is assigned at the beginning of every message. The random number is same in both base station message and handset message for every unique call. That random number is matched in both messages for determining whether they belong to the same phone call. Reconciliation is done on matched messages. The reconciled message is kept in a file for further usage. The average file size and memory usage of the reconciled message is shown in table 2.
Table 2. Average Memory Usage and Average Message Size
|
No. of Messages in unit time |
Average File Size in KB |
Average Memory Usage in |
|
|
|
KB |
|
1000 |
8.56 |
289.85 |
|
5000 |
51.5 |
283.75 |
|
10000 |
105 |
279.6 |
|
15000 |
168 |
272.55 |
|
20000 |
232 |
215.95 |
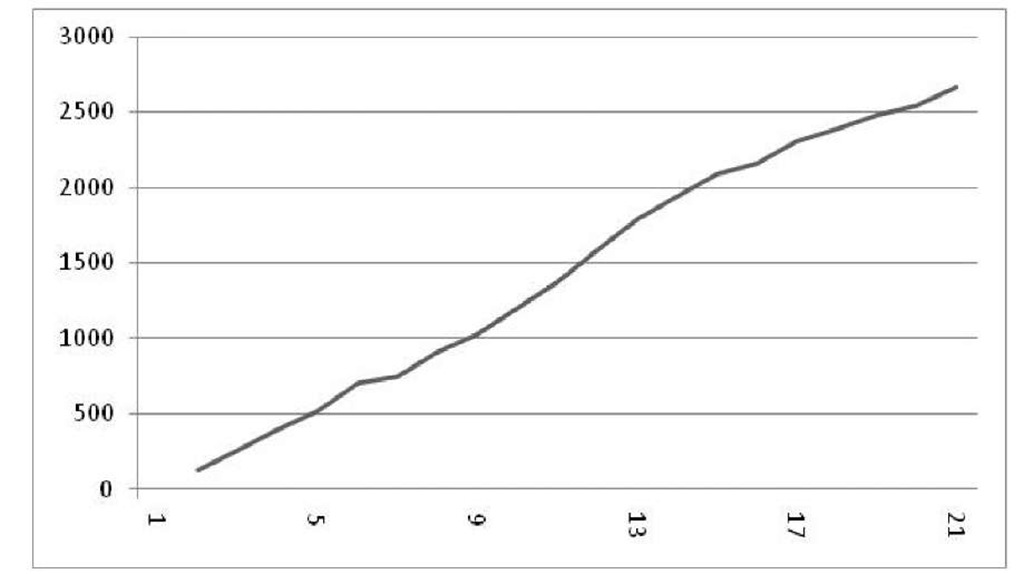
The file size is varied because it is assumed that different hardware and software configurations of the handset may keep different and variable length data. The reconciliation time is jotted down in figure 3.
Fig. 3. Y-axis implies average reconciliation time in nanosecond. X-axis implies number of messages in thousand.
The numbers of messages are generated in random order within ten minutes of time duration. Number of messages is implied by the number of phone calls made during that period. Here number of messages implies either the number of messages in the base station or subscribers’ handsets for simplicity. Total number of messages is basically double the number of calls held during the stipulated time. The performance of the billing framework grows linearly by the increasing number of phone calls. Total number of phone calls at a time within a cell of the mobile network is constant. The performance of the simulated billing framework is satisfactory for processing that constant number of phone calls at a time. Although in the real life situation input/output cost, traversal cost through network are much higher than our simulation work.
Conclusions
The trustworthiness of the billing system is ensured by MAMO for which reputation of the business process would be improved. MAMO is also identified as a feature within collaborative working environment.