Information Technology Reference
In-Depth Information
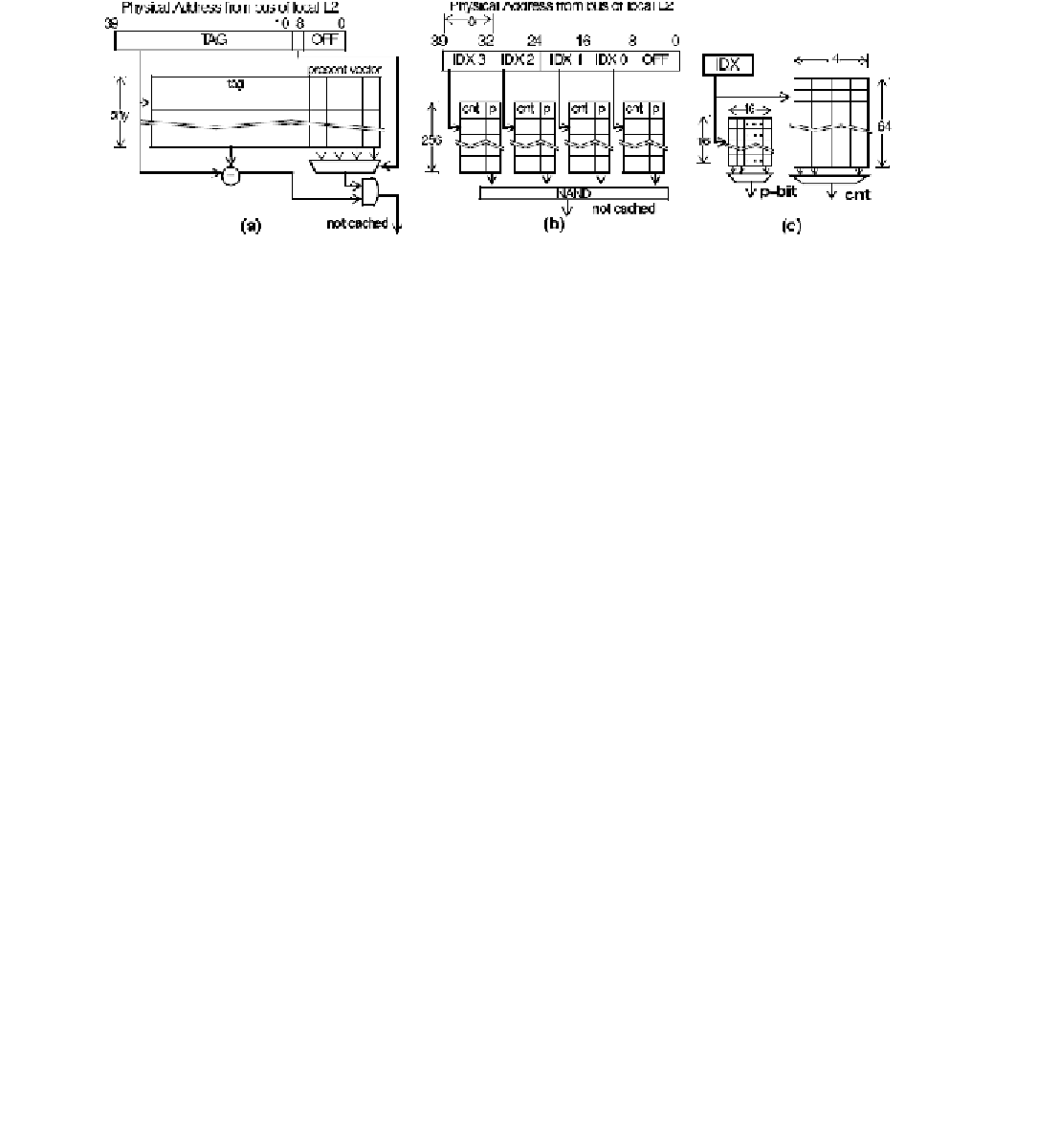
FIGURE 4.32:
Bloom filters for Snoops: Include-Jetty and Exclude-Jetty. Reproduced from [
171
].
Copyright 2001 IEEE.
sooner and the cache access can be avoided altogether. In the Decaying Bloom filters this early
detection of misses works very well (when the Bloom filters indicate that there is no live line in
any
of the ways of the cache) giving the technique an advantage over competing way prediction
schemes [
131
].
4.9.6 Coherence Protocols
Cache coherence protocols on bus-based multiprocessors work by having each cache snoop
on every bus transaction. This guarantees that if any cache has a copy of the data referenced
in the bus transaction, it will also participate in the coherence actions for the data. The very
nature of snooping is premised on everyone listening in on the broadcast bus simultaneously,
which implies that caches snoop the bus even if they have nothing to do with a particular bus
transaction. This brings to mind the parallel access of all the ways of a set-associative cache
knowing full well that all but one will miss. However, the distributed nature of cache coherence
and the fact that parallel snooping is needed for correctness and not simply for performance
make its power optimization an interesting problem.
Moshovos, Memik, Falsafi, and Choudhary proposed the first technique to deal with
this problem [
171
]. Their solution is based on small local filters called
Jettys
. These filters sit
between the bus and the L2s and discard most of the unneeded snooping. However, in contrast
to way-prediction, mispredictions are not allowed in snoop filtering.
Snoop filtering only works
if it can be established with absolute certainty that the snooped address is not cached locally in the L2
.
Preventing a snoop to
cached
data is a correctness issue. The Moshovos et al. proposal ensures
correctness by using variants of Bloom filters [
30
] to eliminate snoops that are
guaranteed
to be
irrelevant to the contents of the local cache.
Three different approaches are proposed. The first approach is the exclude-Jetty. It is a
small tag-cache which is used to indicate
what is not cached
in the L2. It does this by observing
Search WWH ::

Custom Search