Information Technology Reference
In-Depth Information
In Fig. 4, we can see that OWASP Zed Attack Proxy attacks the target web appli-
cation with a relatively uniform and slow speed. The number of normal accesses and
recognized attacks in this case is small compared to the previous case. One feature
similar to Subgraph Vega is that this tool also attacks a small number of pages.
Fig. 5 shows us that Acunetix adopts an attack strategy which is more aggressive
than OWASP Zed Attack Proxy's, and somewhat similar to Subgraph Vega's, as
depicted in the number of alerts generated. The Acunetix attack process looks rather
regularly in time domain. Like the 2 previous tools, it also concentrates real attacks on
a small number of web pages.
Manual Attack by a Human
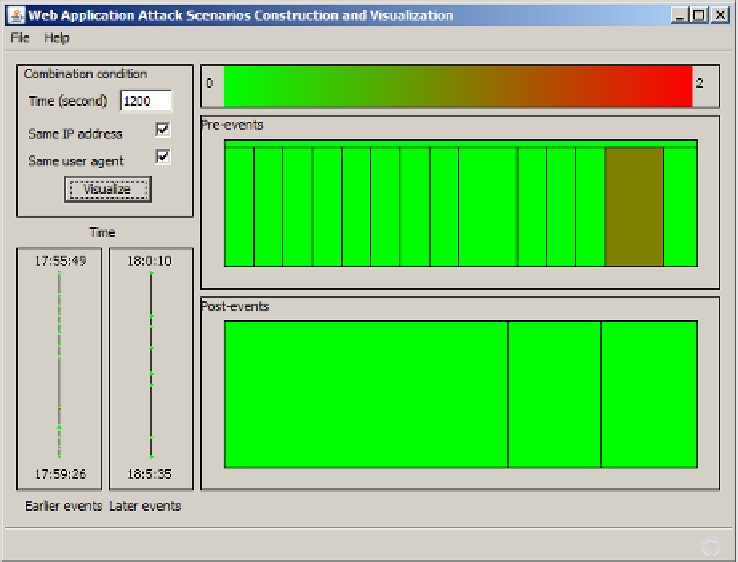
We invite a human security expert to research and attack the target web application.
We use different attack scenario construction parameters' values in this case because
it is clear that the time period between requests will be longer when the requests are
made by a human user. The visualization of the constructed attack scenario is dis-
played in Fig. 6. It is not surprised to see there is only a small number of normal ac-
cesses and attacks in Fig. 6. This result suggests that our technique is quite effective
in distinguishing between attacks by automatic tools and attacks by human users. But
we wonder about its capability in discriminating between attacks by an expert hacker
and attacks by a script kiddie.
Fig. 6.
Attack scenario constructed and visualized after a human person is invited to attack the
target web application
Search WWH ::

Custom Search