Information Technology Reference
In-Depth Information
5.2
Experiment Scenarios
Using Automatic Tools
We use 3 web application vulnerability scanners, including Subgraph Vega [20],
OWASP Zed Attack Proxy [21], and Acunetix Web Vulnerability Scanner [22], to
attack the target web application. Among them, Subgraph Vega and OWASP Zed
Attack Proxy are open source, while Acunetix Web Vulnerability Scanner is commer-
cial, but it has a trial edition that can be used freely.
After using these tools to scan and attack the target web application, we randomly
select an alert that is generated during the attacking process and construct a related
attack scenario from it. Because we want to highlight both event sequences happen
before and after the selected alert, the selected alert is chosen so that it is not among
the ones generated too early or too late in the overall attacking process. We also set
the attack scenario construction parameters to the same values for all these 3 cases to
compare the 3 results more objectively. The visualization results of the attacks by
Subgraph Vega, OWASP Zed Attack Proxy, and Acunetix Web Vulnerability Scan-
ner are shown in Fig. 3, Fig. 4, and Fig. 5 respectively.
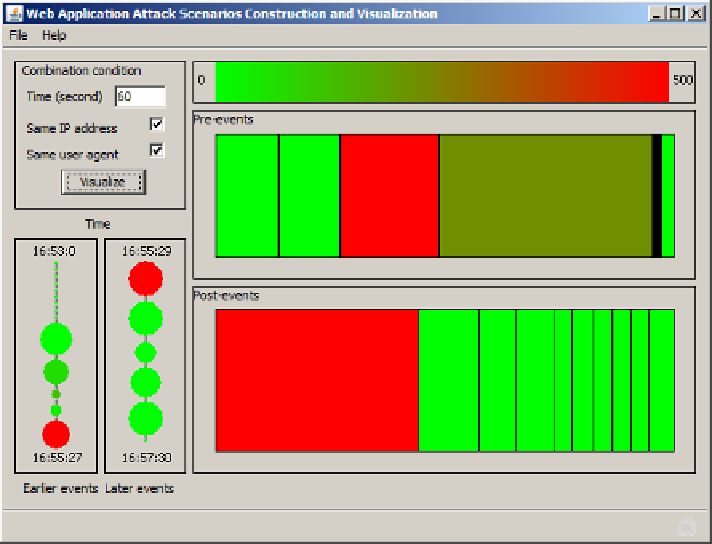
In Fig. 3, we can see that most of the attacks by Subgraph Vega happen around the
selected alert, and these attacks in turn are preceded and followed by lots of other
normal events, as shown in the time-oriented coordinate system. The attacks happen
on a small number of web pages, as shown in the space-oriented coordinate system.
Fig. 3.
Attack scenario constructed and visualized after running Subgraph Vega to attack the
target web application
Search WWH ::

Custom Search