Information Technology Reference
In-Depth Information
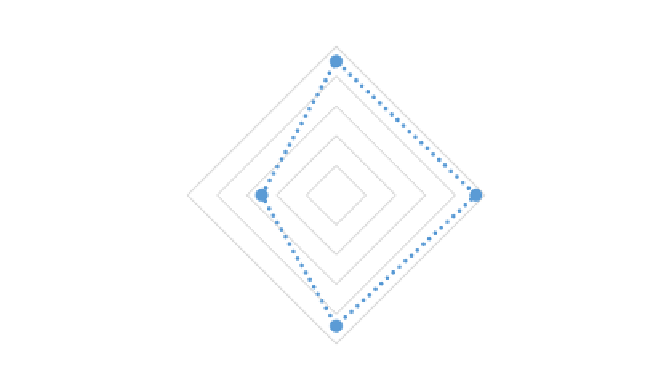
According to the results in Fig. 1, the organization meets the most of the
requirements about responsibilities (90%), management (94%) and information
security functions (88%). However, it was found that only half of the education and
training program requirements can be met with existing information security
approaches of the organization.
Responsibilities
100%
90%
80%
60%
40%
20%
94%
Education &
Training
Program
50%
Management
0%
88%
Information
Security
Fig. 1.
Information security approaches in terms of people in defense industry organization
According to the results demonstrated in Fig. 1, Information security experts stated
that only some units have employees for liaising with business units to identify any
new security requirements based on changes to the operations. It is also indicated that
most of the business unit managers and senior managers have specific programs in
place to comply with information security and privacy policies and standards.
Furthermore, results reflect that most of the information security functions were
actively engaged with other critical functions such as IT, Human Resources, etc. On
the other hand, education and training program requirements about information
security and privacy issues were only partially implemented by the organization.
6.4
Processes
Analyses on information security processes were considered under five titles by the
assessment tool. These titles are security technology strategy, policy development and
enforcement, information security and procedures, physical security, and security
program administration. In this context, the ratings related to the information security
processes in the defense industry organization are displayed in Fig. 2.

Search WWH ::

Custom Search