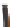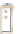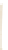Information Technology Reference
In-Depth Information
Client
(attacker's console)
Client
(attacker's console)
Handlers
Agents
Great number of request
in a short time interval
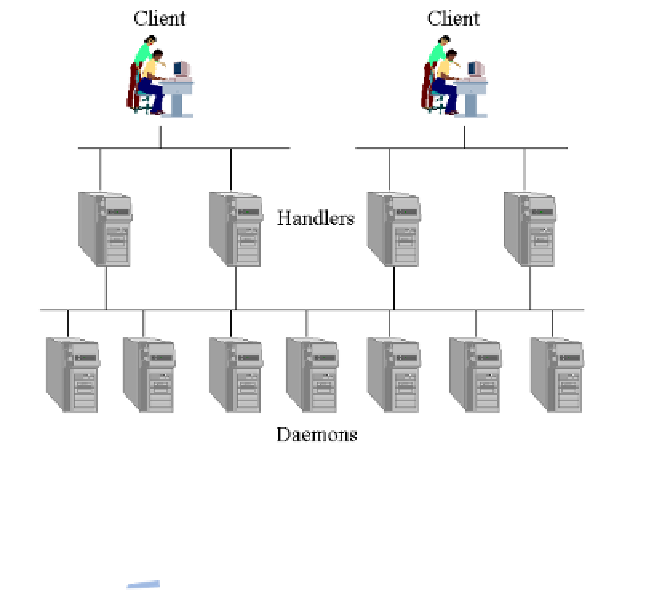
Figure 6: Structure of a DDoS attack.
a distributed mechanism, i.e. a very high number of programs that attackers
use, distributed on different computers and devices (often users do not
suspect to become 'tools' of the attackers) and synchronized by a few centres.
The architecture used was presumably of the type shown in Figure 6. The
agents are the programs that actually send random requests to the attacked
sites. These programs can be found on thousands of infected computers,
meaning that normal users do not know that their machine is running a secret
program of this type. The handler programs are the coordinators of agents: a
few hundred of these are used to control the attack. These programs are
secretly running on infected computers or on some machines of the attackers.
Finally, very few client programs are those of the real attackers, the console
through which starting the attack by sending appropriate messages to the
program handler, which in turn activate the agents. Since each handler can
typically manage up to 1024 agents and a client handler up to 1024, it is easy
to understand how the power of this structure is impressive and can be
controlled by very few attackers.