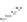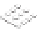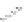Information Technology Reference
In-Depth Information
The hash determines the physical network adapter to use for communication. Different combi-
nations of source and destination IP addresses will, quite naturally, produce different hashes.
Based on the hash, then, this algorithm could allow a single VM to communicate over different
physical network adapters when communicating with different destinations, assuming that the
calculated hashes select a different physical NIC.
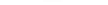
Figure 5.34
h e IP hash-based
policy is a more
scalable load-
balancing policy
that allows VMs to
use more than one
physical network
adapter when com-
municating with
multiple destina-
tion hosts.
192.168.4.100
192.168.4.150
ESXi host
vSwitch0
vSwitch1
Physical
switch
Physical
switch
192.168.2.100
192.168.2.101
192.168.2.102
192.168.2.103
Balancing for Large Data Transfers
A lthough the IP hash-based load-balancing policy can more evenly spread the transfer tra c for a
single VM, it does not provide a benefi t for large data transfers occurring between the same source
and destination systems. Because the source-destination hash will be the same for the duration of
the data load, it will fl ow through only a single physical network adapter.
Unless the physical hardware supports it, a vSwitch with the NIC teaming load-balancing
policy set to use the IP-based hash must have all physical network adapters connected to the