Database Reference
In-Depth Information
Firewall Settings
Because your databases are located in places you physically can't get to or control, Microsoft has
implemented a mechanism to help protect your data. This protection mechanism is the SQL Azure
firewall, which prevents restricted access to all your databases until you physically specify which
computers have permission. Access to your SQL Azure databases is based on the originating IP address
that makes a request.
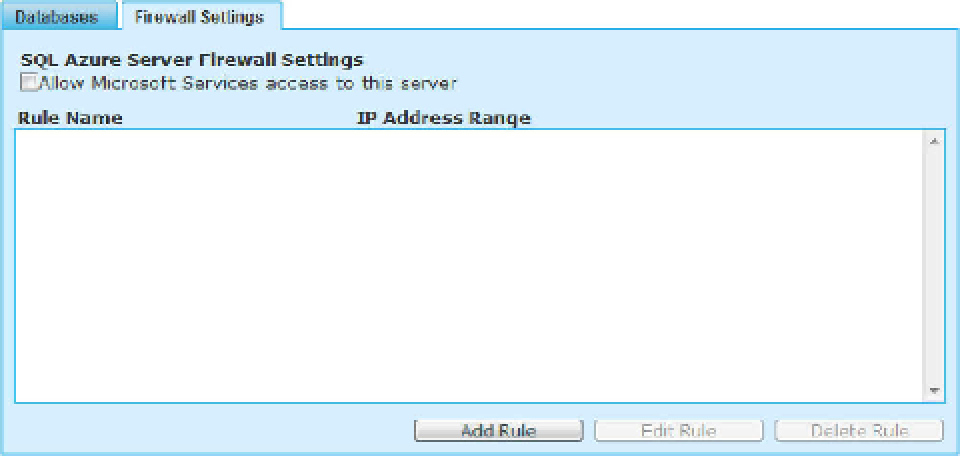
To grant access to your SQL Azure databases, you specify a range of acceptable IP addresses in the
Server Administration portal on the Firewall Settings tab, shown in Figure 3-5. IP address ranges are
defined by rules that allow you to specify multiple firewall setting entries. For example, you can define
an IP address range for your home as well as one for your office. If you attend a conference, you can
define an additional rule and IP address that let you connect from that specific location. Also notice the
“Allow Microsoft Services access to this server” check box on the Firewall Settings tab; it allows internal
communication between Windows Azure services and SQL Azure databases.
Figure 3-5
. Firewall Settings tab
To add a firewall rule, click the Add Rule button on the Firewall Settings tab to display the Add
Firewall Rule dialog, shown in Figure 3-6. You're asked to specify the rule name and the IP address
range. Firewall rule names must be unique, and there is no limit to the number of rules you can have.
Entering the IP Range is simple because the dialog tells you what your IP address is. Figure 3-6 uses
the same value for the range's start and ending values to indicate that only the single specified address
should be allowed to access the database. You can enter a range of IP address if you want multiple
computers to access SQL Azure.
After you've entered your firewall rule information, click the Submit button. Your new rule is added
to the Firewall Settings tab, as shown in Figure 3-7. As the note in Figure 3-6 states, it may be up to 5
minutes before your rule takes effect and you can connect to SQL Azure (although I have never had it
take more than 1 minute to take affect). After that, you can edit and delete the rule.