Information Technology Reference
In-Depth Information
Super Peers
Responsible for
s Cluster
Super Peers
Responsible for
s Cluster
s Cluster
s Cluster
Peer
Peer
Storage
Super Peer
Storage
Super Peer
s Aggregators
s Aggregators
Network of Super Peers
Request for resource
Step 1:
Send a file
request
Request broadcast
Super nodes
check if
resource is
within their
clusters
Step 2:
Receive a list of
relevant peers
Reply for the possession of
resource
Reply forward
(Other peers possessing
resource will also reply)
Reply forward
Reply forward
s trust value
s trust value
s trust value
Calculate the global
trust values of replying
peers to find out the
most reputable peer(s)
Download of resource
Step 3:
Select a set of
peers
Rate peer ;
Send trust report
Trust report
Step 3:
Send vote
Trust report
Update s trust value
FIGURE 6.11: Example of secure trust aggregation in SuperTrust [Dim-
itriou et al., 2007].
Step 4: Send vote. Peer v rates the interaction it had with peer u. It first
encrypts the report with the public key of the u's aggregators. Doing
this allows encapsulating its rating for both peer u and its resource. The
peer then submits it to the designated super peer. The latter forwards
the encrypted vote to its neighbors. Upon reception of the trust report
for v, the aggregators fetch from the storage super peer v's previous en-
crypted ratings, update it using a homomorphic encryption scheme [Pail-
lier, 1999], and submit the aggregation result back to the storage Super
peer in order to guarantee the durability of the ratings in the system.
In turn, the storage super peer only stores the encrypted value that was
advertised by the majority of the aggregators. Here, we can see that such
a scheme protects against up to n/2 suspicious aggregators (where n is
























































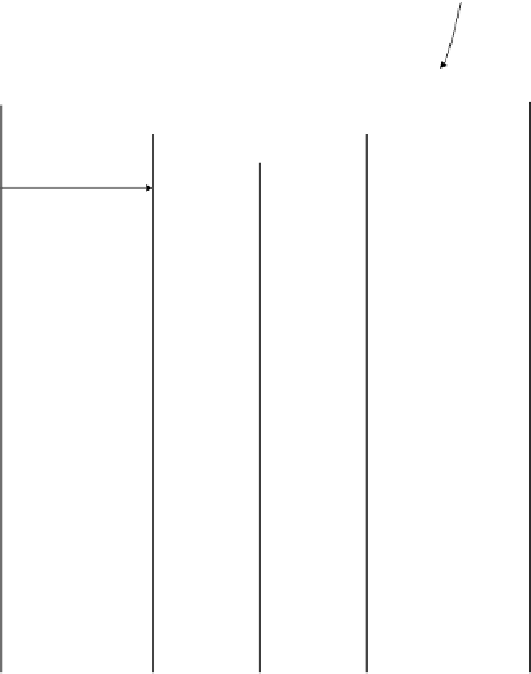

















Search WWH ::

Custom Search