Information Technology Reference
In-Depth Information
Requestor
Controller
Policy
Base
Policy
Base
X-Profile
X-Profile
Policy
Exchange
Compliance Checker
Compliance Checker
Sequence
Prediction
Module
Sequence
Prediction
Module
Tree
Manager
Tree
Manager
Sequence
Cache
Sequence
Cache
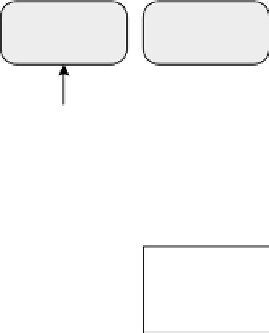
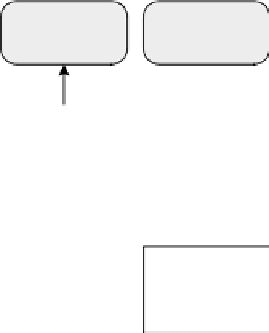
FIGURE 6.5: Trust-χ architecture [Bertino et al., 2004].
The system is also composed of a Policy Base, storing disclosure policies,
the χ-Profile associated with the party, a Tree Manager, storing the state of
the negotiation, and a Compliance Checker, to test policy satisfaction and
determine request replies. The Compliance Checker includes a credential ver-
ification module, which performs a validity check of the received credentials
in order to verify the document signature, check for credential revocation,
and discovery credential chain, if necessary. Finally, Trust-χ system has a
complementary module named Sequence prediction module, for caching and
managing previously used trust sequences.
6.5 FuzzyTrust
Based on a detailed analysis on the characteristics of eBay's transaction
data, Song et al. [Song et al., 2005] developed a FuzzyTrust prototype system
for evaluating peer reputation in P2P transactions. The FuzzyTrust is built
with a fuzzy logic inference technique (elaborated below). A salient and novel
feature of FuzzyTrust is that the system is capable of handling imprecise or
uncertain information collected from the peers.
To explain basic fuzzy concepts, let us consider the seller's local score in-





























Search WWH ::

Custom Search