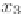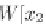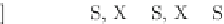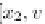Information Technology Reference
In-Depth Information
Fig. 6.3
Locking in the presence of partial rollbacks. Rolled-back segments of the transaction are
shown
indented
. The columns on the
right
show the modes of locks held by the transaction on key
x
i
, i D 1; 2; 3, at each action
We assume that the good practice of transaction programming referred to at the
end of Sect.
5.4
has been followed, so that a write action following a completed
partial rollback never uses information read by a read action included in the rolled-
back action sequence. The write action WŒx
2
;
v
2
;
w
0
2
uses information read by
RŒx
2
;
u
2
, which does not belong to the partial rollback to savepoint P
2
. The write
action WŒx
2
;
u
2
;
w
00
2
in turn uses information read by RŒx
2
;
u
2
performed after the
partial rollback to savepoint P
1
. Thus, we conclude that no unrepeatable read can
occur that would violate the integrity of the database.
t
The following theorem states how the read-write locking protocol prevents
isolation anomalies.
Theorem 6.4
Let
H
be a history of transactions in the read-write model. Then
H
is permitted by the read-write locking protocol if and only if
H
contains neither
dirty writes nor dirty reads nor any unrepeatable reads by read actions not included
in partially rolled-back action sequences.
Proof
That none of the anomalies mentioned appear in a history permitted by
the read-write locking protocol follows from the following observations: (1)
commit-duration X locks prevent dirty writes, (2) commit-duration X locks and
short-duration S locks prevent dirty reads, and (3) short-duration X locks and