Information Technology Reference
In-Depth Information
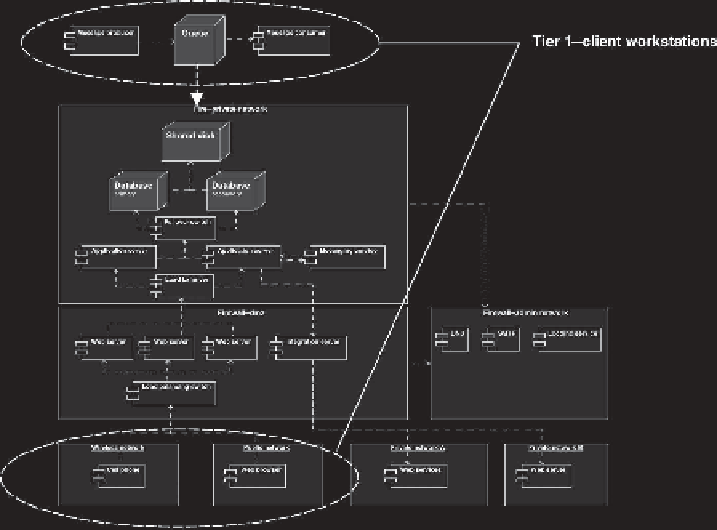
Figure 14.11
Tier 1 identification for a complex n-tier application
14.5 n-TIER APPLICATIONS
We return to the starting point of our discussion, the complex application in
Figure 14.1. We approach the test planning for this application by applying what
we have learned from the previous, increasingly complex applications. We start
by identifying the different testing tiers in the application with the develop-
ment team's assistance. Figures 14.11-14.14 show one such possible planning
approach.
Application components that seem to provide the input/output functionality
of the application to the external world are “lassoed” fi rst as seen in Figure 14.11.
These components and their activities will be included in the tier 1 test strategy
chessboard.
Application components that seem to provide the security layers between the
external world and the web services are “lassoed” next as seen in Figure 14.12. These
components and their activities will be included in the tier 2 test strategy chess-
board.
Application components that seem to provide the basic web service lay-
ers between the security layer and the application are “lassoed” next as seen in
Figure 14.13. These components and their activities will be included in the tier 3 test
strategy chessboard.
Search WWH ::

Custom Search