Cryptography Reference
In-Depth Information
period length is 101,405,850.
(It is interesting to note that
this length key would be
exhausted in
1
100
of a second on
an Internet backbone circuit
today.)
The relationship of this
machine to the Vernam
encryption system is not only
through the way in which a
lengthy binary sequence of
active pin settings in the rotors
is achieved by forming the
product of six much shorter
ones, but also in the way a sym-
bol of plaintext is encrypted
using the resulting key stream.
Just behind the rotors is a
“squirrel cage” consisting of
27 bars on each of which is a
pair of movable lugs. Either or
both of the lugs can be set in
a position to be engaged and
moved to the left on each step
by a diverter actuated by the
presence of an active pin on
the corresponding rotor. The
result is an effective gear wheel
in which the number of teeth is
determined by both the active
pin settings and the movable
lug settings. The number of
teeth set determines the cycli-
cal shift between one direct
alphabet (plaintext) ABC…
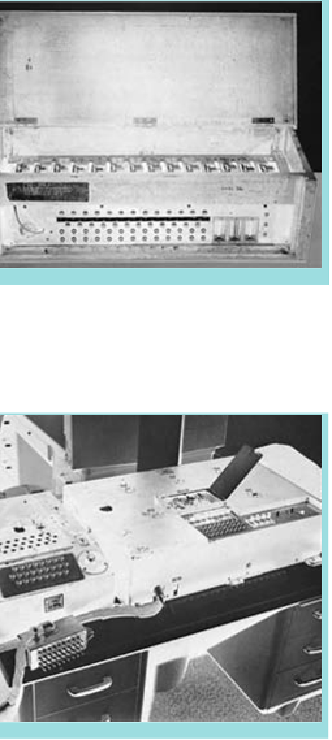
Although no Japanese Purple
cipher machines survived the war,
this is a functional analog of the
Japanese machine that was oper-
ational from 1939.
The Japanese Jade cipher machine
was a variant of the Purple cipher
machines in use during the war. It
differed primarily in that Japanese
kana characters could be typed
directly on the keyboard.