Cryptography Reference
In-Depth Information
641194989852455577634720396702065575387017714394831539504200403961645096
728072726095322023421112943523393879161424144304336692169642791406419470
91918468321515459948865 (mod
p
)
and
w
g
d
(
P
)
438908365050492172112141159266916014689430122622767850409990603339138565
278995621692689044958914233869339458908488816024934068379856100514306151
641194989852455577634720396702065575387017714394831539504200403961645096
728072726095322023421112943523393879161424144304336692169642791406419470
91918468321515459948865.
B takes note of the fact that
v
and
w
are equal, and accepts the signature.
Storing Passwords or Passphrases as Digests
A system administrator has a
peculiar problem. She must store the passwords or passphrases of all her users, so that she
can compare these entries to the entered passwords when a user attempts a login. However,
she must be able to protect these passwords, so unauthorized users cannot obtain them. Ide-
ally, it would be best if the system administrator herself could not obtain the passwords.
Cryptographically secure digest functions provide a solution. A user's password is not
stored, but rather, a digest of the password is stored. When a user attempts a login, a digest
of the password is taken, then compared against this user's entry in a table. If an adversary
somehow obtains the hashed password list, it does him little good if the digest function is
a good one; that is, it will be nearly impossible for him to obtain any particular password
from its digest. Even the system administrator does not know any particular password; only
the user who created it knows (assuming he or she didn't forget it). Various operating sys-
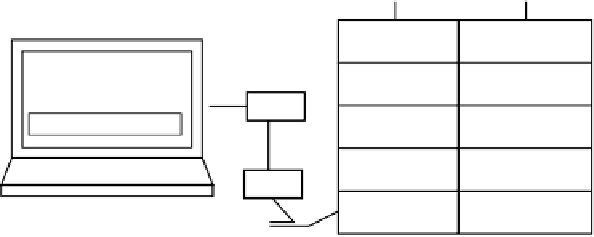
tems grant access based on such an idea; Figure 16.11 illustrates this process:
16.8
ATTACKS ON DIGEST FUNCTIONS
There are various approaches to defeating a digest function. To defeat a digest function,
one must be able to produce a bogus message, say
P
, which hashes to the same value as
Figure 16.11
hashed password
user
User 5 login:
h(P(1))
1 - Billy
Tutti:
Enter password:
h(P(2))
2 - Kenton
X
h(P(3))
3 - Mandy
***********
h
h(P(4))
4 - Seth
h(X)
h(P(5))
5 -Tutti
Allow login iff h(X) = h(P(5))




Search WWH ::

Custom Search