Cryptography Reference
In-Depth Information
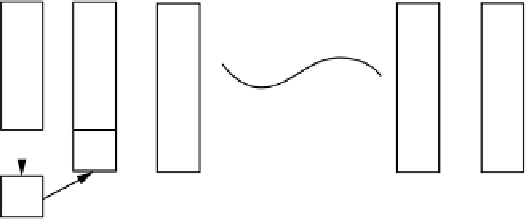
FIGURE 16.9
Sender A
Receiver B
Ex - Encipher with x's
public info
DX - Decipher with x's
private info
EB
DB
P
C
C
P
xmit
h(P)
hash function = h
Accept msg iff
these match
DA
EB
DB
EA
h(P)
xmit
We deal with this very simply: we compute a digest for the plaintext message, then
append it to the message. This larger message is then encrypted, and sent. The decryptor
checks that the tail end of the decrypted message is the digest of the data that precedes it.
Without knowledge of the secret key, it is highly unlikely that an adversary can construct a
message that decrypts to a message having this special structure; that is, with the tail of the
message being a perfect digest of the rest of the data. (See Figure 16.10.)
Note here that we cannot attach a digest to a message in this way if we are using a pub-
lic key system, and encrypting using only the recipient's public information. It should be
obvious why this is so.
16.7
SIGNING WITH ELGAMAL
The ElGamal signature scheme was specifically intended to work with digests. Suppose a
sender, say A, is using the public key (
p
,
g
,
y
), and the private key
a
, where
p
is a large, safe
FIGURE 16.10
E - enciphering
transformation
D - deciphering
transformation
h - hash function
Sender
Receiver
E
D
P
P
P
C
C
xmit
h
h(P)
X
h(P)
Accept msg iff X = h(P)

















Search WWH ::

Custom Search