Cryptography Reference
In-Depth Information
this problem, but here we will cover a different solution. It has some advantages over CBC,
but can only be used for a secret key cipher.
14.5
CIPHER FEEDBACK MODE (CFB)
Like CBC, CFB uses an initialization vector (IV) to start the encryption and decryption.
What may seem strange is that only the encryption transformation is used for both encryp-
tion and decryption; the decryption key is never needed. (This makes CFB unsuitable for
public key ciphers, of course.)
Suppose the cipher maps
m
-bit blocks to
n
-bit blocks, where
m
≤
n
. Let
E
k
(
x
) denote the
encipherment of
x
using the secret encryption key
k
. The IV is an
m
-bit quantity that need
not be secret. Let
r
be a positive integer not exceeding
n
, and divide the plaintext message
into
r
-bit blocks,
x
1
,
x
2
, . . . ,
x
w
. We proceed as follows:
1.
Let
I
1
= IV
2.
For
i
from 1 through
w
do:
a) Let
U
i
=
E
k
(
I
i
).
b) Let
t
i
be the
r
least significant bits of
U
i
. (Suppose the least significant bits are to the
right.)
c) Let
c
i
=
x
i
t
i
.
d) Shift
I
i
toward the left
r
bit positions, and append
c
i
; assign this value to
I
i
+1
.
The ciphertext is the set of
r
-bit blocks
c
1
,
c
2
, . . . ,
c
w
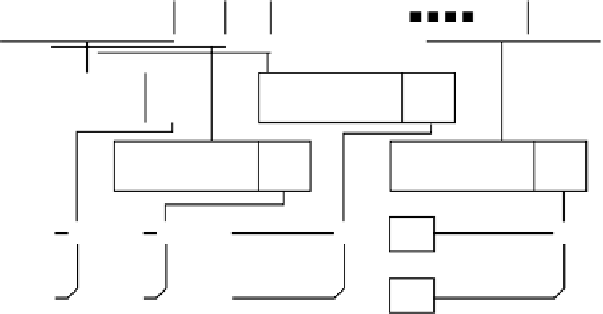
. Figure 14.1 is a diagram of the CFB
mode of operation.
To decrypt, we go through nearly the same process, with only the ciphertext blocks and
plaintext blocks exchanging roles in step 2.(c).
FIGURE 14.1
IV = initialization vector
E = encryption transformation
Cipher Feedback Mode - CFB
m
r
r
r
IV
c(1)
c(2)
c(w-1)
E
r
E
r
E
t(1)
t(3)
E
r
r
t(2)
t(w)
+
+
+
+
x(1)
x(2)
x(3)
x(w)
c(1)
c(2)
c(3)
c(w)



Search WWH ::

Custom Search