Cryptography Reference
In-Depth Information
The plaintext is now large enough so that when squared modulo
n
, we obtain a residue
2
. An attacker is now forced to compute the modular square root.
different from
P
Java Algorithm
I have written methods to encrypt and decrypt using Rabin. To ensure
only the correct message is returned out of the four possible roots obtained in the decryp-
tion phase, I add 4 bytes of redundancy to the beginning of each block; that is, before a
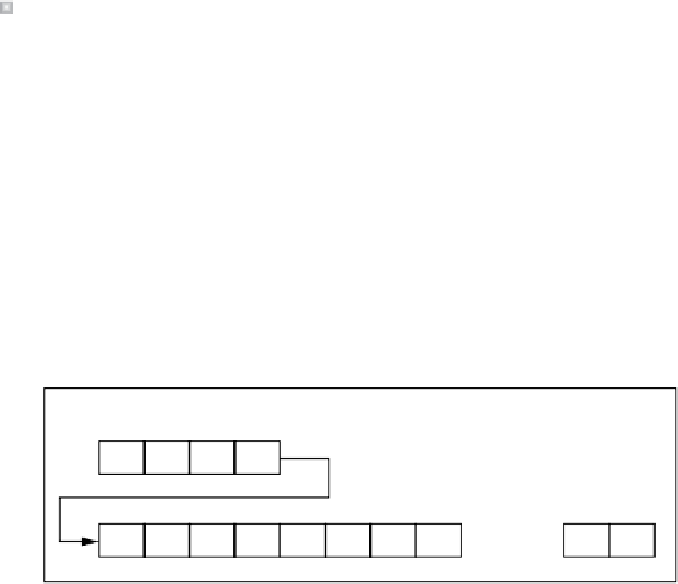
block is encrypted, the first 4 bytes of the blocks are repeated at the front. (See Figure 10.2.)
Then, to protect against attacks commonly used on Rabin ciphers, I add 4 bytes of salt
to the head of each block before encrypting it. This means a different ciphertext will be pro-
duced each time the message is encrypted. (See Figure 10.3.)
Of course, after decrypting, the receiver knows these bytes are simply random data, and
throws them out.
I also use PKCS#5 padding, and so that the addition of redundancy and salt does not
further restrict the block size, I do not include it in the padding. Thus, the maximum plain-
text block size (including salt and redundancy) is 255 + 8 = 263 bytes. (See Figure 10.4.)
FIGURE 10.2
Repeat first 4 bytes
HI
!
............
HI
!
HOW
FIGURE 10.3
Random Data
$%
@
&
............
HI
!
HI
!
FIGURE 10.4
Message + Padding
255
Salt
4
Redundancy
4
263 bytes





Search WWH ::

Custom Search