Graphics Programs Reference
In-Depth Information
Spoofing is the first step in sniffing packets on a switched network. The
other two interesting details are found in ARP. First, when an ARP reply comes
in with an IP address that already exists in the ARP cache, the receiving system
will overwrite the prior MAC address information with the new information
found in the reply (unless that entry in the ARP cache was explicitly marked
as permanent). Second, no state information about the ARP traffic is kept,
since this would require additional memory and would complicate a protocol
that is meant to be simple. This means systems will accept an ARP reply even
if they didn't send out an ARP request.
These three details, when exploited properly, allow an attacker to sniff
network traffic on a switched network using a technique known as
ARP
redirection
. The attacker sends spoofed ARP replies to certain devices that cause
the ARP cache entries to be overwritten with the attacker's data. This tech-
nique is called
ARP cache poisoning
. In order to sniff network traffic between
two points,
A
and
B
, the attacker needs to poison the ARP cache of
A
to
cause
A
to believe that
B
's IP address is at the attacker's MAC address, and
also poison the ARP cache of
B
to cause
B
to believe that
A
's IP address is also
at the attacker's MAC address. Then the attacker's machine simply needs to
forward these packets to their appropriate final destinations. After that, all
of the traffic between
A
and
B
still gets delivered, but it all flows through the
attacker's machine, as shown here.
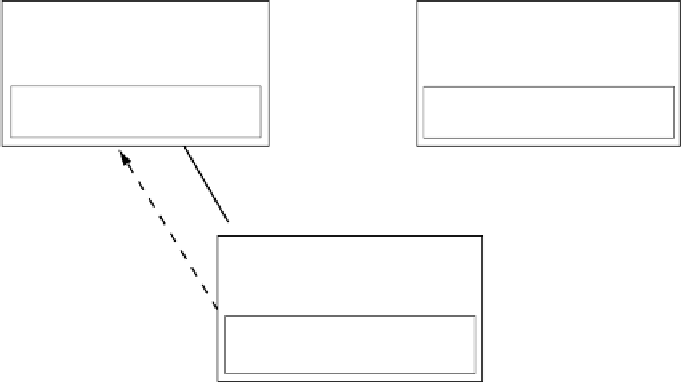
System A
IP: 192.168.0.100
MAC:
00:00:00:AA:AA:AA
System B
IP: 192.168.0.200
MAC:
00:00:00:BB:BB:BB
Internal ARP cache
192.168.0.200 at
00:00:00:FA:CA:DE
Internal ARP cache
192.168.0.100 at
00:00:00:FA:CA:DE
Attacker system
IP: 192.168.0.137
MAC:
00:00:00:FA:CA:DE
Traffic to A
Traffic to B
Internal ARP cache
192.168.0.100 at
00:00:00:AA:AA:AA
192.168.0.22 at
00:00:00:BB:BB:BB
Since
A
and
B
are wrapping their own Ethernet headers on their packets
based on their respective ARP caches,
A
's IP traffic meant for
B
is actually sent
to the attacker's MAC address, and vice versa. The switch only filters traffic
based on MAC address, so the switch will work as it's designed to, sending
A
's
and
B
's IP traffic, destined for the attacker's MAC address, to the attacker's
port. Then the attacker rewraps the IP packets with the proper Ethernet
headers and sends them back to the switch, where they are finally routed to
their proper destination. The switch works properly; it's the victim machines
that are tricked into redirecting their traffic through the attacker's machine.