Information Technology Reference
In-Depth Information
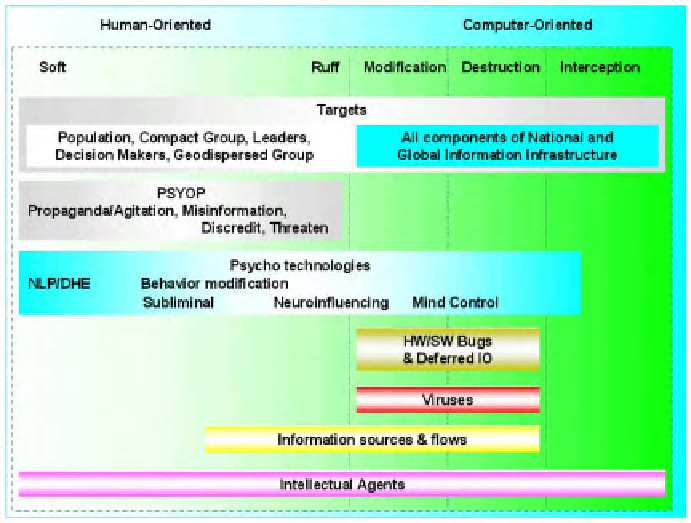
Fig. 5. IO under construction
Moreover, viruses or worms similar to 'Code Red', 'Nimda' or 'Slammer' represent a
first stage of virus war only. No doubt we will clash with something similar to the 'ICE',
described in Gibson's "Neuromancer" (ICE - from Intrusion Countermeasures
Electronics) on the next stages of future cyberwar.
We have defined the control superiority above which can be used to explain the
possibilities of pre-arranged intrusions into adversary information sources and
information flows to control them according to an attacker's purposes both from inside
and from outside.
These IO's can be carried out by means of violating conditions of confidentiality,
authentication, access control and non-repudiation for information entities involved in
communications, which usually are interpreted as IO-oriented in the destruction of the
integrity of information resources. But such an understanding will confine us to a
dependency on obsolete ICT and distort a modern understanding of the future
development of information operations. In this connection we can cite the thought by Mr.
John Arquilla
4
: “when we think about 'cyber', we need to reflect on the Greek root -
'kybernan', which means to control or to govern." It is a very pertinent and timely
reminder of 'grassroots'.
We have to avoid possible stumbles and adjust a relatively old understanding of
intrusion in our classification; otherwise we will constantly be getting into a loop. For
this purpose we attract a conception of an intellectual agent, not as a part of the
conception of the Semantic Web, but as an information object synthesizing within itself
the possibilities of viruses and artificial intelligence. The intellectual agents theoretically
have potential capabilities to be independent from any kind of information infrastructure,
Search WWH ::

Custom Search