Information Technology Reference
In-Depth Information
Applications
of Dataology
Universal
Dataology
Life
Dataology
Behavior
Dataology
Data Acquisition
Data Exploration
Data Analysis
Data Awareness
Foundations
of Dataology
Data Experiment
Data Visualization
Data Camouflage
Data Mining
Data Sniffization
Data Perception
Data Audiblization
Data Cyclopedia
Data Integration
Data Taxonomy
Data Tangiblization
Data Management
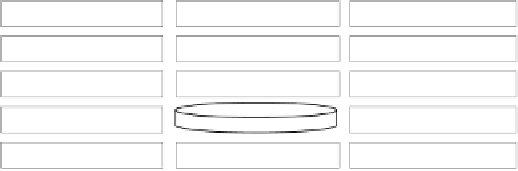
Fig. 4.
The framework of dataology
In addition, dataology needs to develop more new technologies:
- Data Experiment
Most of people consider that bioinformatics makes biological experiment to
become data computing. However, we believe that bioinformatics is more like
biological data experiment. For example, we have a gene sequence of SARS
virus in which “A”, “C”, “G” and “T” are represented as the points with
different colors. When we optionally change sequences or duplicate parts of
sequences (this just like to try to mix multiple reagents in chemical experi-
ments), we may find an “S” picture. If that is quite true, the result is very
valuable. Such cases also exist in other fields (e.g., brain informatics). This
means that data experiment technology will be on demand.
Data experiment is to use various known or unknown methods to deal
with a dataset in order to discover special features and laws. It focuses
on the randomness of methods and the unpredictability of results. This is
different from data mining in which the selection of methods is based on the
prospective results.
- Data Camouflage and Perception
The data camouflage is to camouflage the private data which are exposed in
the public. Different from data security (privacy protection, privacy mining),
data camouflage focuses it efforts on camouflaging the data in the public,
rather than storing data in a safe place to prevent invasion.
In the field of computer, a logion says, “garbage in garbage out”. However,
current problems are that we do not know which data are garbages, as well as
which data are the disguise of valuable data. How to obtain the valuable data
under this circumstance? This involves data perception which is to percept
the camouflaged data. It can be regarded as the reverse of data camouflage.