Information Technology Reference
In-Depth Information
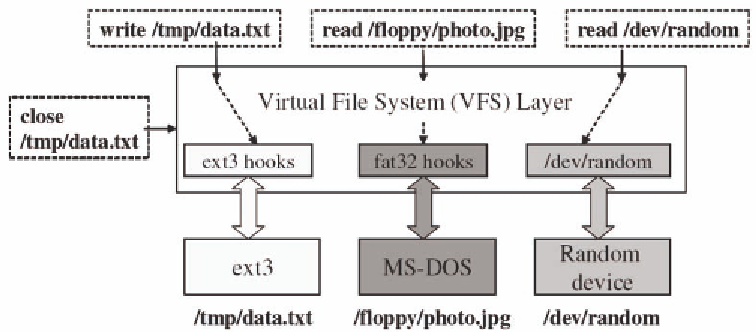
Figure 6. File and device hooks in the Linux virtual file system (vfs) layer
these data structures are located in memory, the
attack module replaces the genuine function
provided by the character devices with the attack
function. The attack function for reading from
the device simply returns a zero when bytes are
requested. After the attack, every read from the
device returns a zero.
Impact:
All security functions within the
kernel and other security applications rely on
the PRNG to supply pseudo random numbers.
This attack stealthily compromises the security
of the system, without raising any suspicions
from the user.
in a global linked list called formats. The binary
handler, specific to a given binary format, is also
supplied when a new format is registered.
A new process is created on the system, the
kernel creates the process address space, sets up
credentials and in calls the function
search_bi-
nary_handler
, which is responsible for loading the
binary image of the process from the executable
file. This function iterates through the formats list
to look for an appropriate handler for the binary
that it is attempting to load. As it traverses this list,
it invokes each handler in it. If a handler returns
an error code ENOEXEC, the kernel considers
the next handler on the list; it continues to do
so until it finds a handler that returns the code
SUCCESS.
This attack works by inserting a new binary
format in the formats list and supplying the kernel
with a malicious handler that returns the error code
ENOEXEC each time it is invoked. Because the
new handler is inserted at the head of the
formats
list, the malicious handler is executed each time
a new process is executed.
Impact:
The attacker is able to successfully
invoke malicious code each time a new process
is created on the system.
adding a new binary format
The goal of this attack is to invoke malicious
code each time a new process is created on the
system (Shellcode, 2006). While rootkits typically
achieve this form of hooking by modifying kernel
control data, such as the system call table, this
attack works by inserting a new binary format
into the system.
Attack.
This attack operates by introducing a
new binary format into the list of formats supported
by the system. The handler provided to support this
format is malicious in nature. The binary formats
supported by a system are maintained by the kernel
Search WWH ::

Custom Search