Information Technology Reference
In-Depth Information
The new traces were created by executing in-
stances of these applications in parallel and merg-
ing them into one trace by using the timestamps
which we have added to each memory access.
The benchmarks which we have built are
defined herein below:
application gzip, executed in parallel.
Trace 6: Composed of two instances of the
•
application bzip2 and two instances of the
application apsi, executed in parallel.
Trace 7: Composed of two instances of the
•
application bzip2 and two instances of the
application crafty, executed in parallel.
Trace 8: Composed of two instances of the
•
Trace 1: Composed of four instances of the
•
application bzip2 executed in parallel.
Trace 2: Composed of four instances of the
application gzip and two instances of the
application apsi, executed in parallel.
Trace 9: Composed of two instances of the
•
application gzip executed in parallel.
Trace 3: Composed of four instances of the
•
•
application crafty and two instances of the
application apsi, executed in parallel.
Trace 10: Composed of two instances of
application apsi executed in parallel.
Trace 4: Composed of four instances of the
•
•
application crafty executed in parallel.
Trace 5: Composed of two instances of the
the application gzip and two instances of
the application crafty, executed in parallel.
Trace 11: Composed of the instances of
•
application bzip2 and two instances of the
•
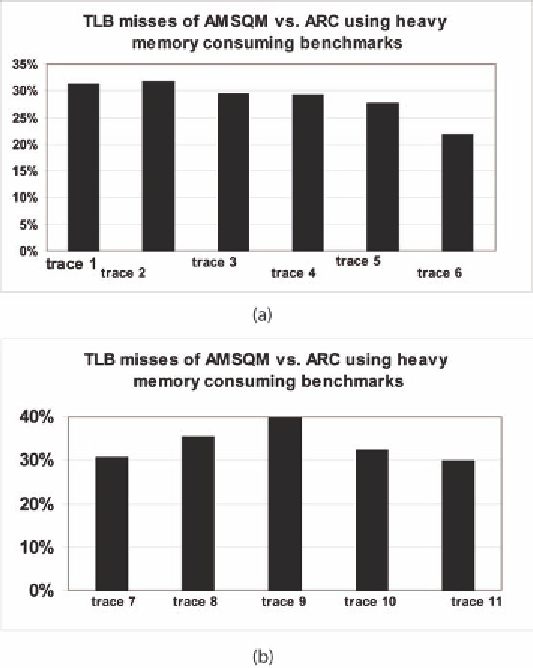
Figure 7. a. First group of heavy traces TLB misses; b. Second group of heavy traces TLB misses
Search WWH ::

Custom Search