Information Technology Reference
In-Depth Information
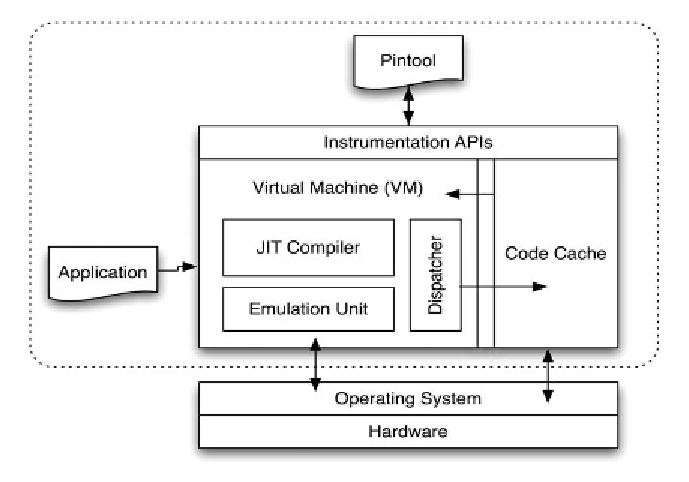
the same ISA as the underlying host. As shown
in Figure 5, the Pin system consists of:
idiosyncrasies of the underlying instruction set
and allows passing of context information, such
as register contents, to the injected code as param-
eters. Pin programs typically consist of analysis
and instrumentation elements. The basic building
blocks for defining instrumentation points are
machine instructions, basic blocks, procedures,
images, and applications. For example, the C++
code below shows the use of the Pin API to in-
strument the target code with trace functions each
time
sleep()
is invoked.
First, a replacement function is defined with
the same signature as the function that is being
replaced (in this example
sleep()
). (Box 7)
A callback function
ImageLoad()
is used to
intercept binary-image loads that are executed by
the target application. The Pin API can then be used
to obtain the function that will be replaced with
the new tracing/trampoline function. (Box 8)
The instrumentation function is “hooked” onto
image loads through
IMG _ AddInstrument-
Function()
as follows:
•
Instrumentation API, which is used to write
programs that perform dynamic interception
and replacement;
•
JIT Compiler, which compiles and instru-
ments the bytecode immediately before
execution;
•
Code cache, which caches translations be-
tween the target binary and the JIT compiled
code;
•
Emulation unit, which interprets instructions
that cannot be executed directly; and
•
Dispatcher, which retrieves and executes
code from the code cache.
To analyze a program's behavior (multithread-
ed or not), Pin users must write a program that
performs dynamic instrumentation. Pin provides
an API based on the ATOM API (Srivastava &
Eustace, 1994) that shields programmers from
Figure 5. The Pin software architecture
Search WWH ::

Custom Search