Information Technology Reference
In-Depth Information
Hubs and Repeaters
Repeaters operate in the physical layer of the OSI model. They basically repeat the data (bits)
from one port to all other ports. Hubs are repeaters with many ports that were created to
concentrate the wiring into a communication closet. These devices are not aware of frames or
packets; they amplify the signal and send out all ports. Repeaters do not delineate broadcast or
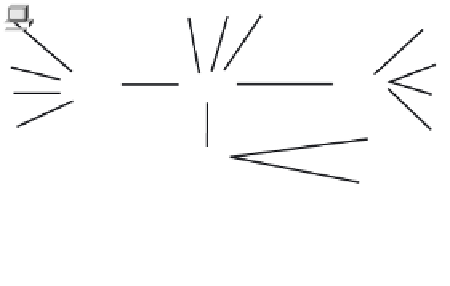
collision domains. Figure 2-5 shows that all devices connected to a repeater are in the same
collision domain; they all compete for the same bandwidth. Repeaters are said to be protocol
transparent because they are not aware of upper-layer protocols, such as IP, IPX, DECnet, and
so on.
Repeaters
Figure 2-5
Repeaters
Collision Domain
Broadcast Domain
Bridges and Layer-2 Switches
Bridges operate in the data-link layer of the OSI model. Bridges learn the MAC layer addresses
of each node of the segments and remember off which port the MAC addresses are located.
The bridge builds a table of MAC addresses and ports. If the destination MAC address of an
incoming frame is not in the table, bridges forward the frame to all ports (minus the port from
which the frame came). If the destination MAC address is in the table, bridges forward the
frame only if the destination MAC address is on another port. Bridges filter the frame if the
destination MAC address is located on the same port on which the frame arrived.
Bridges are store-and-forward devices. They store the entire incoming frame and verify the
checksum before forwarding the frame. If a checksum error is detected, the frame is discarded.
Figure 2-6 shows that bridges define the collision domains; each port off a bridge is a separate
collision domain. Collision domains are also referred to as bandwidth domains because all
devices in the collision domain share the same bandwidth. Bridges do not control broadcasts.
Bridges flood broadcasts out all ports. Bridges are protocol transparent; they are not aware of
upper-layer protocols, such as IP and IPX. Bridges are designed to flood all unknown and
broadcast traffic.
























































Search WWH ::

Custom Search