Information Technology Reference
In-Depth Information
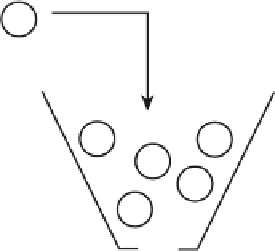
Leaky Bucket Model
Figure 5-21
Token
(Represents each cell upon arrival of cell token generation)
Bucket size
Burst tolerance
Leak Rate
(Can be different for each traffic type)
After the bucket is full, any new tokens represent cells that are noncompliant. Also, noncompli-
ant cells can be discarded or they can have their CLP bit set to 1.
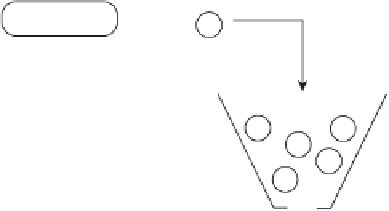
In certain types of traffic policing, cells that are compliant in the first bucket are subjected to a
second test using a second bucket. Figure 5-22 shows this type of traffic policing.
Dual Leaky Bucket Model
Figure 5-22
T
oken
Cell
If first bucket is full,
Discarded
If first bucket
is not full
Bucket Size 1
CDTV
Burst tolerance
PCR
Leak Rate 1
(Can be different for each traffic type)
Token
Bucket Size 2
If second bucket is full
Tagged or discarded
If second bucket is not full
Passes into network
Leak Rate 2



























Search WWH ::

Custom Search