Information Technology Reference
In-Depth Information
declared enumeration of possible pieces of behaviour, although this is gener-
ally too inflexible. Other approaches limit the policy values to expressions in
a given language, or to restrictive classes of algorithms. Restrictions can be
placed on which aspects of the system state can be accessed or changed by
the policy value, or more complicated constraints applied.
{PolicyEnvelopRule=Policy Value must either allow or
block the Get Loan Phone interaction; it must do so on
the basis only of the states of the User and the
Repair Request and values computed from them.}
«EV_Process»
Phone Loan
Policy
Setting
Behaviour
«EV_PolicyEnvelope»
Phone Loan Policy
Envelope
«EV_Role»
Phone Repair
Provider
«EV_Artefact»
Loan
Handset
value within envelope
«EV_InteractionInitiator»
«EV_ControllingBehaviour»
«EV_AffectedBehaviour»
«EV_ArtefactReference»
«EV_PolicyValue»
Phone Loan
Policy Value
«EV_Interaction»
Get Loan
Phone
«EV_InteractionResponder»
«EV_Role»
User
{PolicyValueRule=Allow interaction if:
- user is a VIP user; or
- repair request is delayed by more than 24 hours.}
Affected Behaviour
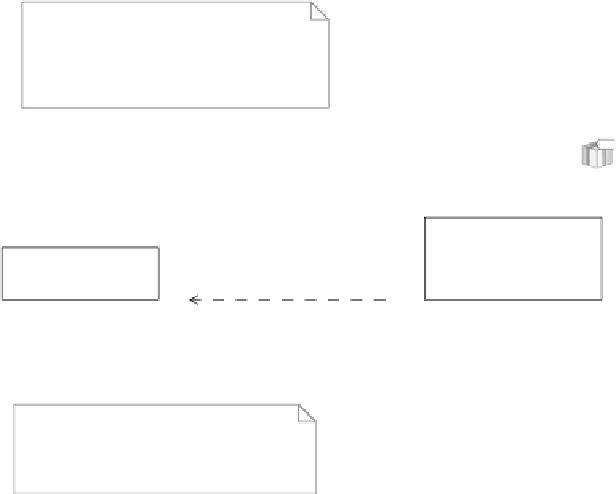
FIGURE 10.2: A policy that controls the issue of loan handsets.
We can see these concepts at work in the example given in figure 10.2.
This shows the policy that controls the circumstances when a handset should
be loaned to a customer. All the related pieces of information are gathered
together into a single diagram, so that the policy can be seen as a whole.
The affected behaviour is identified as being a specific interaction, namely the
interaction in which the handset, seen as an artefact, is transferred from the
phone repair provider to the user. In any particular epoch, this interaction
is constrained to happen only if the guard expressed by the policy value is
satisfied. The policy value can be changed by the policy-setting behaviour,
represented in the figure as a process. The definition of this process will
state what roles can change the value, and in what situation this can happen.
This might involve an agreement between a branch manager and someone at
headquarters. Finally, whatever change is proposed, the policy value must
satisfy the constraints given in the policy envelope. Here, these state that the
value must be a boolean guard and must draw only on information about the
user and the progress of the repair request that the user has made.
In the