Java Reference
In-Depth Information
Using interceptors for programmatic security
In EJB 3 you can set up interceptors that are invoked before and after (around) any EJB
business method. This facility is ideal for crosscutting concerns that shouldn't be duplic-
ated in every method. You could reimplement
listing 6.8
using interceptors instead of hard-
coding security in the business method, as in the following listing.
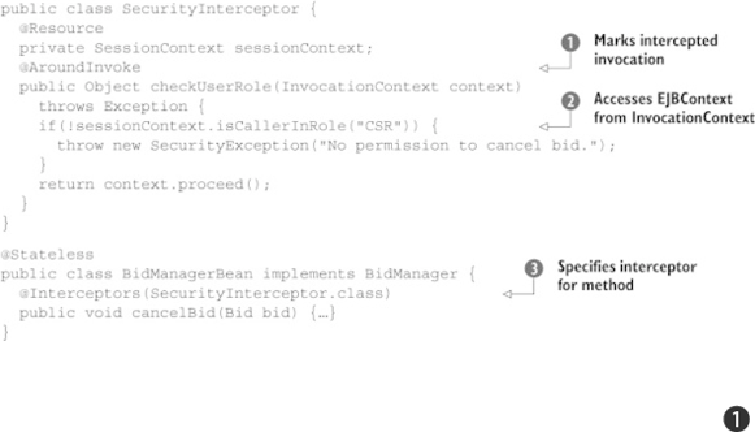
Listing 6.9. Using interceptors with programmatic security
The
SecurityInterceptor
class method
checkUserRole
is designated as
Around-Invoke
, meaning it would be invoked whenever a method is intercepted .
In the method you check to see if the
Principal
is CSR . If the role isn't correct, you
throw a
SecurityException
. The
BidManagerBean
, on the other hand, specifies
the
SecurityInterceptor
class as the interceptor for the
cancelBid
method
.
Note that although using interceptors helps matters a bit in terms of removing hardcoding
from business logic, there's no escaping the fact that there's still a significant amount of
hardcoding. Basically you've moved the hardcoding from the business method to the inter-
ceptors. Moreover, unless you're using a simple security scheme where most EJB methods
have similar authorization rules and you can reuse a small number of interceptors across
the application, things could become complicated very quickly. In effect, you'd have to re-
sort to writing ad hoc interceptors for method-specific authentication combinations. Con-