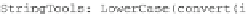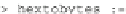Cryptography Reference
In-Depth Information
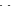
Based on the above table, the following is a function to convert a list of bytes to
a hex string.
Next, we ''invert'' the preceding table, this time to convert strings formed by
two hex digits to the corresponding bytes in integer form, and use this table to give
the associated function that converts hex strings to lists of bytes.
A quick check that these functions behave as intended is the following:
Some of our implementations of schemes are able to encrypt and decrypt binary
files. We use the following procedure to read a file to a list of bytes.
For the inverse process we want to check, before writing a list of bytes to a file,
whether a file with the same name already exists and, in this case, whether it can be
overwritten. The following function checks this and prompts the user about which