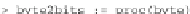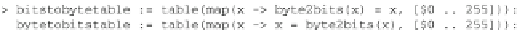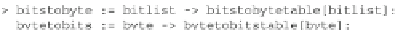Cryptography Reference
In-Depth Information
perform encryption and decryption of messages without having to go to the lower
bit level. Working at the byte level is even more convenient in the case of byte-
oriented algorithms such as AES in which a great number of byte operations are
performed.
We start with a function to pass from bytes, given as integers, to 8-bit lists. Note
that Maple uses the little-endian convention in its implementation of
convert
and, since we use the big-endian convention, we reverse the list:
The following tables are helpful to speed up the process of converting between
integers in the 0..255 range and 8-bit lists.
Using these tables we define a very efficient conversion between bit lists and
bytes.
1
Thus, for efficiency, we generally use
bytetobits
instead of
byte2bits
; the only purpose of the latter function was to help to build the
two preceding tables that once evaluated in the Maple session can also be called
directly from other functions.
A quick check that these functions behave as intended is the following:
As already mentioned, a more compact way to represent bytes is by means of
hex digits, each two-digit hex string corresponding to one byte. More generally,
we can represent any list of bytes by the even-length hex string obtained by
concatenating the hex representations of the bytes in the list. We next give
conversions between bytes or lists of bytes and hex strings, which are used by the
encryption/decryption functions. To make these conversions faster, we use tables.
Note that Maple's
convert/hex
function outputs the alphabetic hex digits as
upper case letters but we use lower case letters instead, as it is more usual in
cryptographic texts and code. We start by building a table (in Array format) with
the correspondences between bytes and hex digits.
1
Alternatively, from Maple v12 onwards, the functions
Join
and
Split
, from the package
Bits
, can also be used for this purpose.