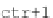Cryptography Reference
In-Depth Information
The decryption algorithm is very similar:
Algorithm 4.10. CTR decryption
.
Input
: An initial counter ctr, a ciphertext
c
=
c
1
...
c
l
, and a block cipher key
k
.
Output
: The plaintext
Dec
(
k
,
c
)
=
m
1
...
m
l
.
Key Stream Computation
:
r
0
ctr
;
for
i
from
1
to
l
do
r
i
:=
:=
F
k
(
ctr
+
i
)
end do
;
Decryption
:
for
i
from 1 to
l
do
m
i
:=
c
i
⊕
r
i
end do
;
return
m
1
...
m
l
.
Note that an adversary who observes a counter being repeatedly used in encryp-
tions with the same key can obtain the result of Xor-ing two plaintext blocks (cor-
responding to these repeated counters) by just Xor-ing the corresponding ciphertext
blocks and, as we have already mentioned, this may give a lot of information about
these plaintexts.
CTR mode has several advantages that make it the mode of choice in many appli-
cations and it looks likely that it will surpass CBC as the most commonly used mode.
For example, both encryption and decryption are parallelizable and the keystream
blocks can be generated from the initial counter before starting the transmission.
Moreover, it is very simple, it does not use the cipher decryption function and does
not require padding as the last block can be a partial block similarly to OFB mode.
Also, it allows random access during decryption, i.e., the
i
th block of ciphertext can
be decrypted independently of the remaining ones. Even more importantly, CTR has
very good security properties and, as shown in Sect.
4.3.2
, if the underlying block
cipher is a pseudo-random function, the randomized version of CTR described above
is CPA secure.